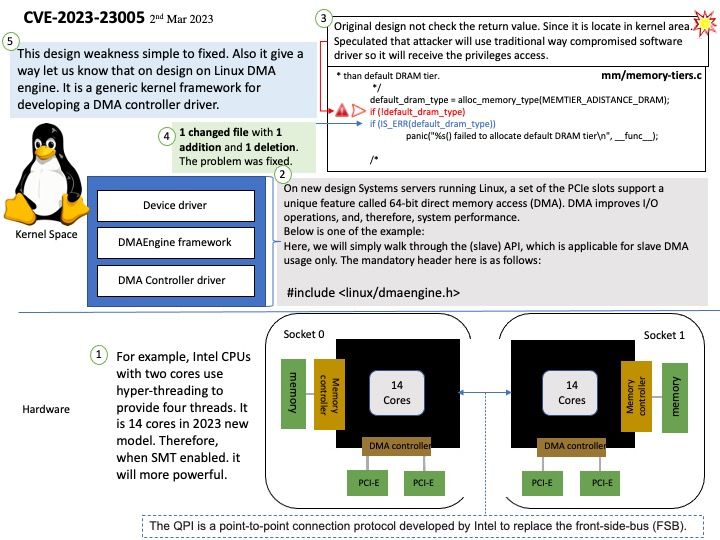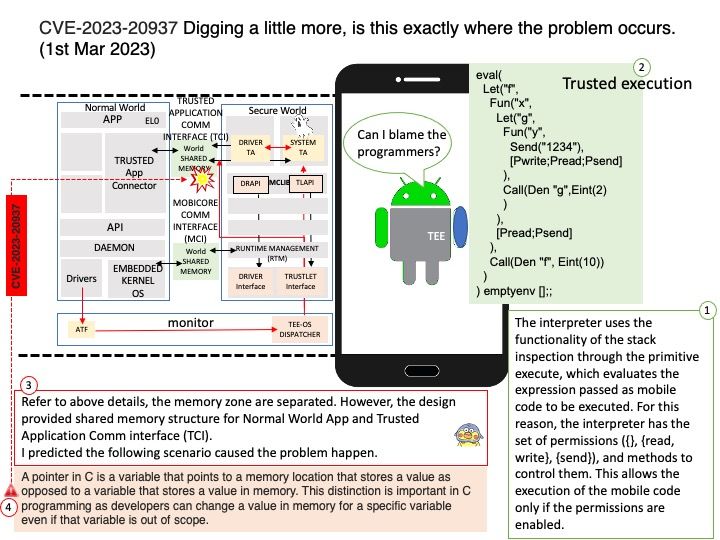
Preface: It’s always easy to forget things. Forget even your girlfriend’s birthday. So, whatever security alerts, after more than a year, become worthless. It seems nothing. Maybe not for you. But I totally agree.
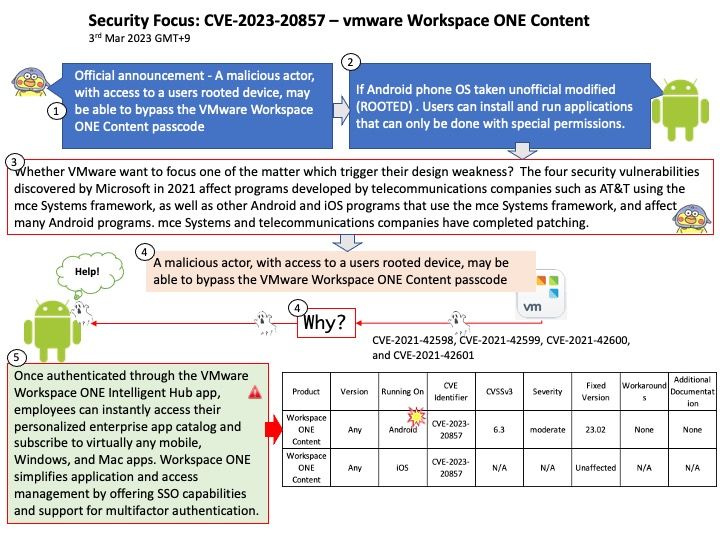
Background: If Android phone OS taken unofficial modified (ROOTED) . Users can install and run applications that can only be done with special permissions. Perhaps you will say, if such procedure taken. It is hard to garantee is there any malware implanted. So, run any mobile apps on top will be in risk. As a result. What is the actual meanings wriiten by VMware described in their security advisory?
Do you remember the following news?
The four security vulnerabilities discovered by Microsoft in 2021 affect programs developed by telecommunications companies such as AT&T using the mce Systems framework, as well as other Android and iOS programs that use the mce Systems framework, and affect many Android programs. mce Systems and telecommunications companies have completed patching.
Vulnerability details: A malicious actor, with access to a users rooted device, may be able to bypass the VMware Workspace ONE Content passcode.
For official information, see url – https://www.vmware.com/security/advisories/VMSA-2023-0006.html