Preface: Two different methods and names, but similar in function.
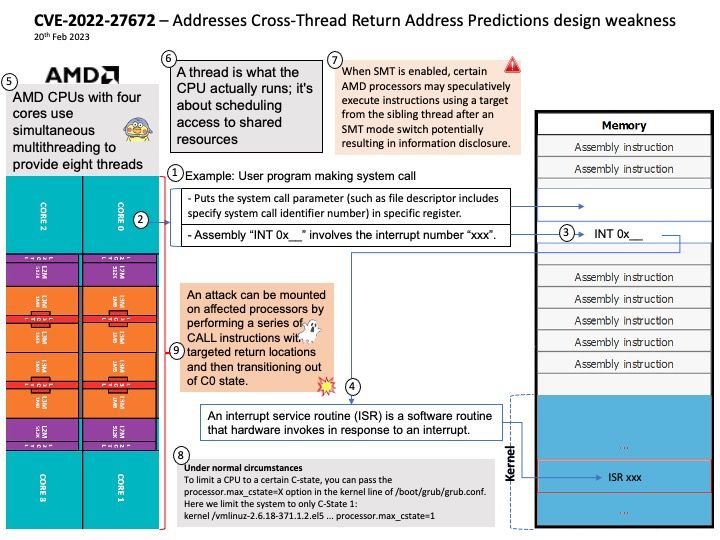
AMD CPUs with four cores use simultaneous multithreading to provide eight threads, and most Intel CPUs with two cores use hyper-threading to provide four threads.
Background: In IBM S390 system configuration. Use the smt= and nosmt kernel parameters to control multithreading.
By default, Linux in LPAR mode uses multithreading if it is provided by the hardware.
In Linux terminology, simultaneous multithreading is also known as SMT or Hyper-Threading. With multithreading enabled, a single core on the hardware is mapped to multiple logical CPUs on Linux. Thus, multiple threads can issue instructions to a core simultaneously during each cycle.
Vulnerability details: When SMT is enabled, certain AMD processors may speculatively execute instructions using a target from the sibling thread after an SMT mode switch potentially resulting in information disclosure.
Remark: AMD internally discovered a potential vulnerability where certain AMD processors may speculatively execute instructions at an incorrect return site after an SMT mode switch that may potentially lead to information disclosure. AMD believes that due to existing mitigations applied to address other speculation-based issues, theoretical avenues for potential exploit of CVE-2022-27672 may be limited only to select virtualization environments where a virtual machine is given special privileges. As of this notice, AMD is not aware of any actual real-world exploits based on this behavior.
Official announcement: For details, please refer to the link – https://www.amd.com/en/corporate/product-security/bulletin/amd-sb-1045