Preface: Back to forty years ago, computer trend in mainstream is command mode. When Microsoft windows GUI born, people favour Windows OS. As time goes by, because of Microsoft system vulnerability, people said I like Linux. As of today, from time-to-time you will heard Linux Kernel vulnerability occurs. Can you change to Microsoft windows now? A classic Linux operating system footprint is smaller than Microsoft windows. Besides, opensource software assists Linux even it has vulnerability. If a merchant is to choose between being cost-effective (free) and paying for the option to license the product. Perhaps they are not so worry about vulnerability. The truth is that even though you pay to but software product it also bundle with vulnerability matter.
Background: CPU supports multiple threads per physical core also referred to as Simultaneous multithreading (SMT) or Hyper-Threading (HT).
AMD and Intel chips with micro-op caches are vulnerable to Spectre-style attacks. The attacks exploit the micro-op cache to leak secrets in three ways:
- Across the user-kernel boundary.
- Between two SMT (Simultaneous MultiThreading) threads running on the same physical core
- Along a mis-speculated execution paths
This design weakness depends on how the CPU uses his internal memory cache (level 1). So the vulnerability doesn’t specify which brand is vulnerable. Perhaps all is fall into the scope.
On systems with simultaneous multi-threading (SMT), attacks are possible from the sibling thread, as level 1 cache and branch target buffer(BTB) may be shared between hardware threads in a CPU core. A malicious program running on the sibling thread may influence its peer’s BTB to steer its indirect branch speculations to gadget code, and measure the speculative execution’s side effects left in level 1 cache to infer the victim’s data.
Disable Hyper-Threading (SMT) to Avoid Spectre-Like Exploits, but causing CPU performance issue.
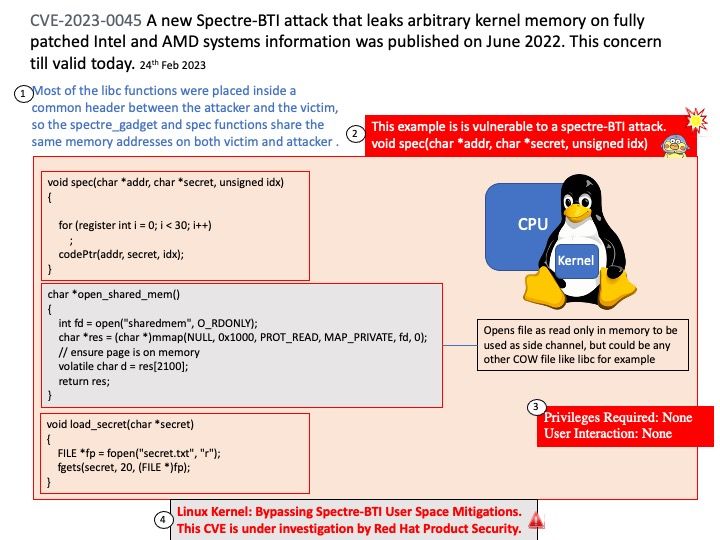
Vulnerability details:
The Linux kernel does not correctly mitigate SMT attacks, as discovered through a strange pattern in the kernel API using STIBP as a mitigation. For details, please refer to this link – https://bugzilla.redhat.com/show_bug.cgi?id=2167288