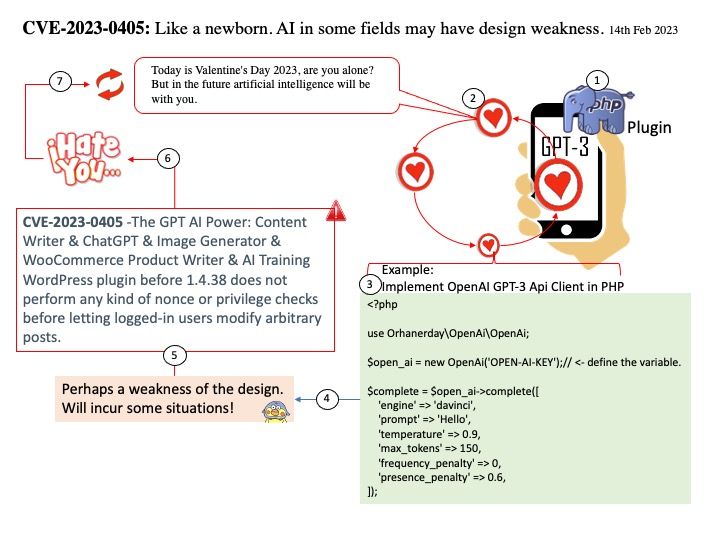
Preface: Today is Valentine’s Day 2023, are you alone? But in the future artificial intelligence will be with you.
Background: With an AI content writer, all you need to do is enter your desired topic or keyword into the plugin settings, and then AI will immediately generate an article that reads as if it were written by a human. You’ll get unique, engaging stories without having to spend hours typing out paragraphs or researching facts. Plus, you’ll have a consistent style and tone that you can use for all of your content.
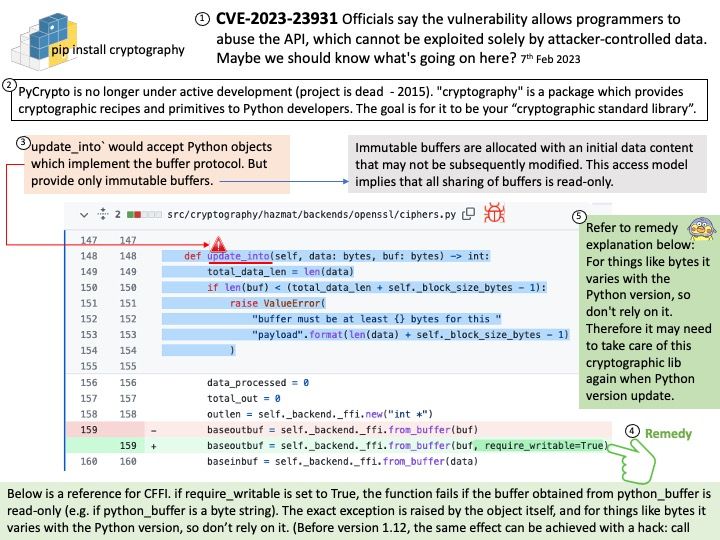
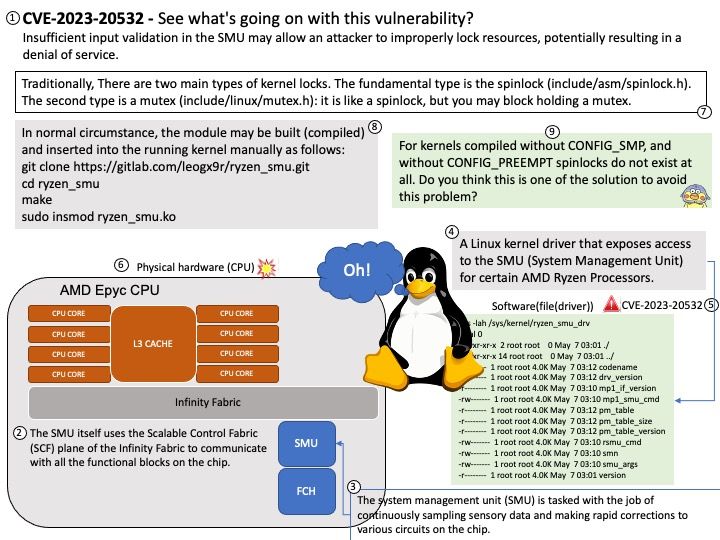
Vulnerability details: The GPT AI Power: Content Writer & ChatGPT & Image Generator & WooCommerce Product Writer & AI Training WordPress plugin before 1.4.38 does not perform any kind of nonce or privilege checks before letting logged-in users modify arbitrary posts.
Ref: CWE is classifying the issue as CWE-862. The software does not perform an authorization check when an actor attempts to access a resource or perform an action. This is going to have an impact on integrity, and availability.
Solution: Upgrading to version 1.4.38 eliminates this vulnerability.
Official Announcement: For details, see the link – https://wpscan.com/vulnerability/3ca9ac21-2bce-4480-9079-b4045b261273
Before you enjoy it with your AI girlfriend, I wish you have a great Valentine’s Day today.
_8th_Feb_2023.jpg)