Preface: When an Android application needs to access sensitive resources on the device, whether it hit design weakness lead to vulnerability occurs.
Background: Usually, if we want to add some user permissions, we write the following code in the AndroidManifest[.]xml file:
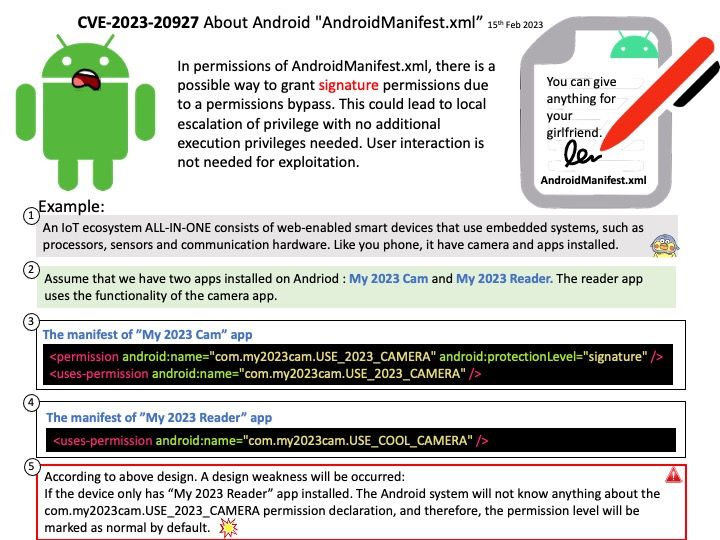
The android system grants these permissions at the installation time but there is one condition. The app that is asking for some permission must be signed with the same signature as that of the app that defines the required permission.
Following are some of the Signature permissions:
1. BIND_ACCESSIBILITY_SERVICE
2. BIND_AUTOFILL_SERVICE
3. BIND_CARRIER_SERVICE
4. BIND_DEVICE_ADMIN
5. BIND_INPUT_METHOD
6. BIND_NFC_SERVICE
7. BIND_TV_INPUT
8. BIND_WALLPAPER
9. READ_VOICEMAIL
10. WRITE_SETTINGS
11. WRITE_VOICEMAIL
Vulnerability details: In permissions of AndroidManifest[.]xml, there is a possible way to grant signature permissions due to a permissions bypass. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.
Official announcement: For details, see the link – https://nvd.nist.gov/vuln/detail/CVE-2023-20927