Preface: When using the U-Boot UEFI implementation to boot the operating system the UEFI runtime stays in memory. Use-After-Free (UAF) is a vulnerability related to incorrect use of dynamic memory during program operation. If after freeing a memory location, a program does not clear the pointer to that memory, an attacker can use the error to hack the program.
Background: Why am I reminding devops of this design weakness. See whether if you have experienced similar bugs in 2019.
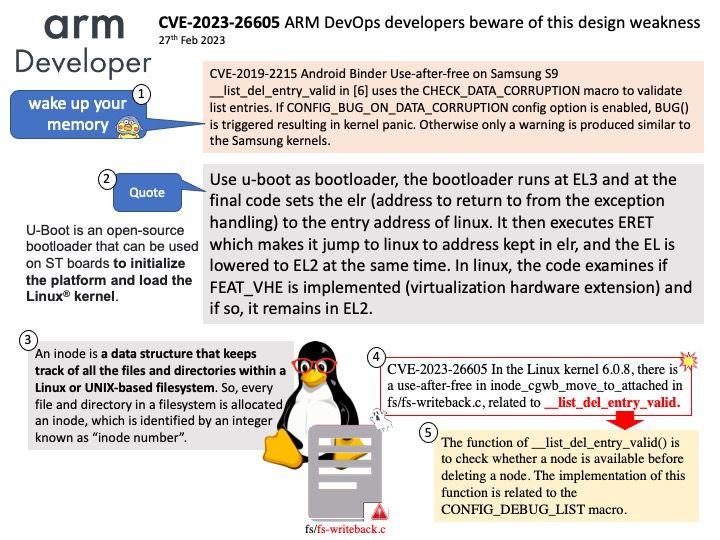
CVE-2019-2215 A use-after-free in binder.c allows an elevation of privilege from an application to the Linux Kernel. No user interaction is required to exploit this vulnerability, however exploitation does require either the installation of a malicious local application or a separate vulnerability in a network facing application.
Vulnerability details: In the Linux kernel 6.0.8, there is a use-after-free in inode_cgwb_move_to_attached in fs/fs-writeback[.]c, related to __list_del_entry_valid.
Official details: For details, please refer to the link – https://lkml.org/lkml/2023/2/22/3