Preface: IDC report predicted that By 2024, 60% of industrial organizations will integrate data from edge OT systems with cloud-based reporting and analytics, moving from single-asset views to sitewide operational awareness.
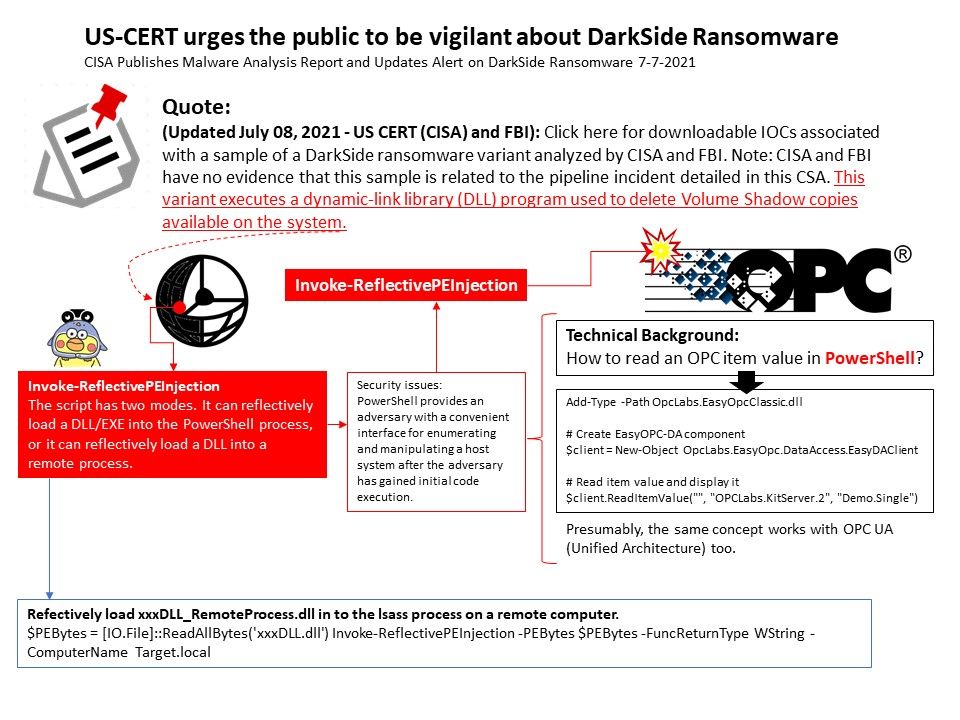
Background: PowerShell provides an adversary with a convenient interface for enumerating and manipulating a host system after the adversary has gained initial code execution.
Security Focus: According to the observation of the security company. You can use PowerShell to execute various Base64 encoding commands. The trend of operation technology will be programmed and developed on powershell.
Cybercriminals responsible for ransomware activities often try to delete them so that their victims cannot restore file access by restoring to shadow copies. The method is to use this (Invoke-ReflectivePEInjection to directly inject DLL into PowerShell).
Meanwhile, they require system administrator privileges, so they rely on zero-day and unpatched victim workstations for privilege escalation.
Remark: What’s more telling is the inclusion of function names that correspond with a PowerShell payload called “Invoke-ReflectivePEInjection”, which lets an attacker inject a dynamic link library (DLL) directly into PowerShell.
Should you have interested of above details. CISA Publishes Malware Analysis Report and Updates Alert on DarkSide Ransomware. For more details, please refer to link – https://us-cert.cisa.gov/ncas/alerts/aa21-131a