Preface: A ransomware attack paralyzed the networks of at least 200 U.S. companies, said headline News. President Biden announces investigation into international ransomware attack on 3rd Jul, 2021.
Background analysis: Cyber criminals are turning to fileless attacks to bypass firewalls. These attacks embed malicious code in scripts or load it into memory without writing to disk.
- Malware tricks you into installing software, allowing scammers to access your files and track your actions.
- Ransomware is a form of malware goal to locks the user out of their files or their device.
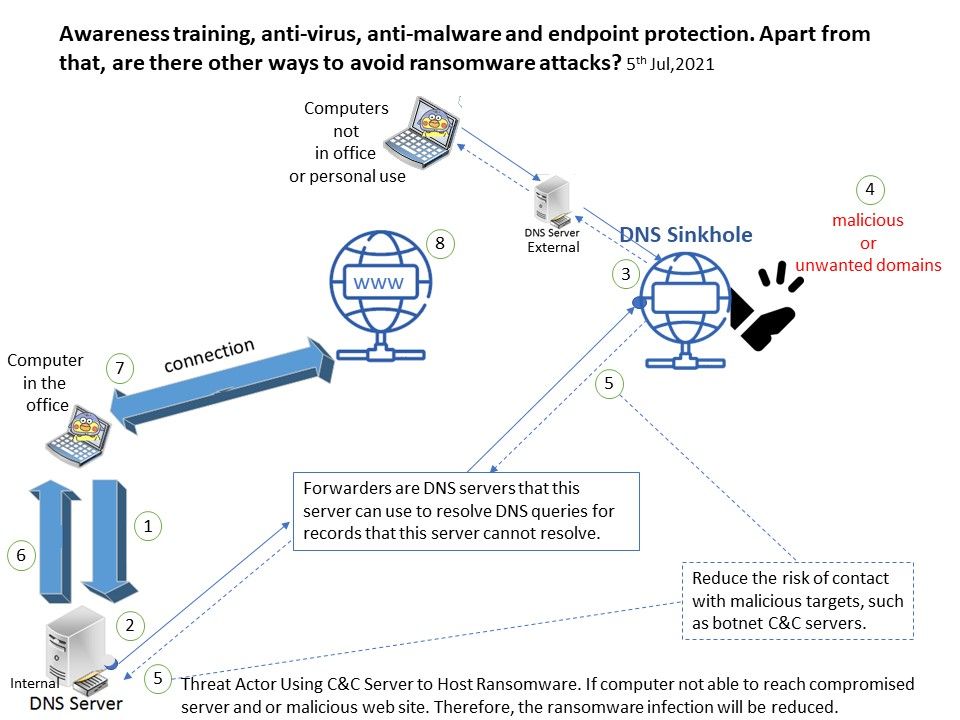
However, whether it is malware or ransomware, they all rely on working with C&C servers. Cybercriminals use C&C servers to host ransomware. If the computer cannot access the infected server and/or malicious website. Therefore, ransomware infections will be reduced.
How DNS Sinkholing reduce the infection hit rate? In fact, the firewall cannot see the originator of the DNS query. When the client tries to connect to a malicious domain, the existing solution is likely to wait for the download and let the anti-virus and malware protection mechanisms isolate the malicious file.
Sinkholing can be done at different levels. Both ISPs and Domain Registrars are known to use sinkholes to help protect their clients by diverting requests to malicious or unwanted domain names onto controlled IP addresses.
Question: If the solution is mature and well-defined. But why the service provider does not implement it. Is it a cost factor?