Preface: (DLL) side-loading is an increasingly popular cyber attack method that takes advantage of how Microsoft Windows applications handle DLL files.
Background:
Where is the Citrix VDA?
By default, the supportability MSI is installed in C:\Program Files (x86)\Citrix\Supportability Tools\ . You can change this location on the Components page of the VDA installer’s graphical interface, or with the /installdir command-line option.
Vulnerability Details: A vulnerability has been identified in Citrix Virtual Apps and Desktops that could, if exploited, allow a user of a Windows VDA that has either Citrix Profile Management or Citrix Profile Management WMI Plugin installed to escalate their privilege level on that Windows VDA to SYSTEM.
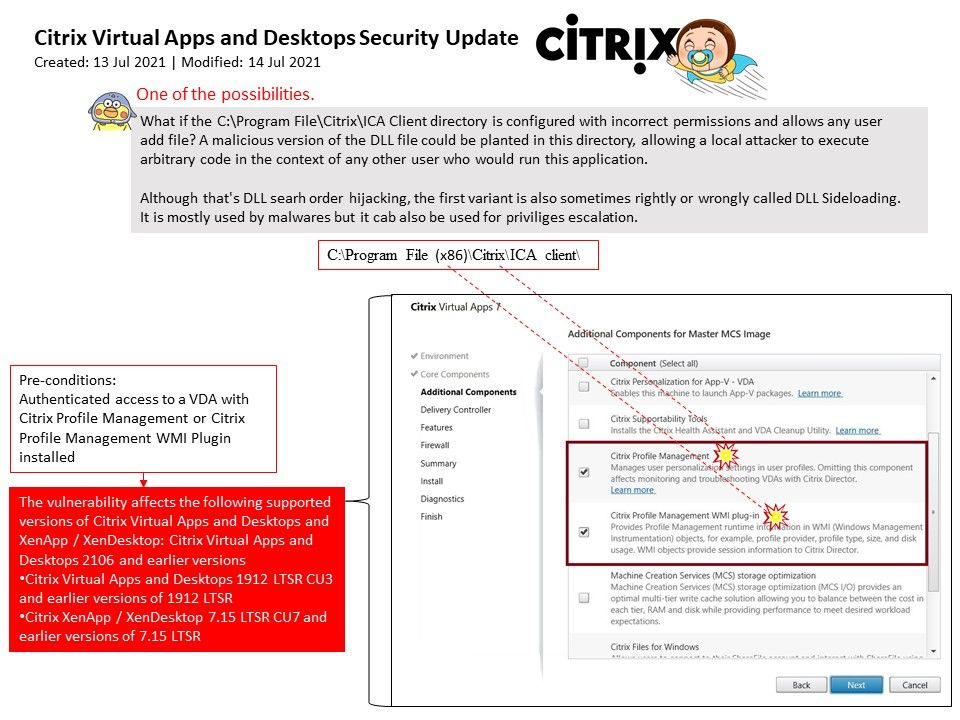
One of the possibilities: What if the C:\Program File\Citrix\ICA Client directory is configured with incorrect permissions and allows any user add file? A malicious version of the DLL file could be planted in this directory, allowing a local attacker to execute arbitrary code in the context of any other user who would run this application. Although that’s DLL searh order hijacking, the first variant is also sometimes rightly or wrongly called DLL Sideloading. It is mostly used by malwares but it cab also be used for privileges escalation.
Official details: https://support.citrix.com/article/CTX319750