Preface: Secure loading of libraries to prevent DLL preloading attacks, said Microsoft.
Background: When an application dynamically loads a dynamic link library (DLL) without specifying a fully qualified path, Windows tries to locate the DLL by searching a well-defined set of directories. If an attacker gains control of one of the directories, they can force the application to load a malicious copy of the DLL instead of the DLL that it was expecting. These attacks are known as “DLL preloading attacks” and are common to all operating systems that support dynamically loading shared DLL libraries. Even experts discovered that malware exploit similar method to inject code into system process.
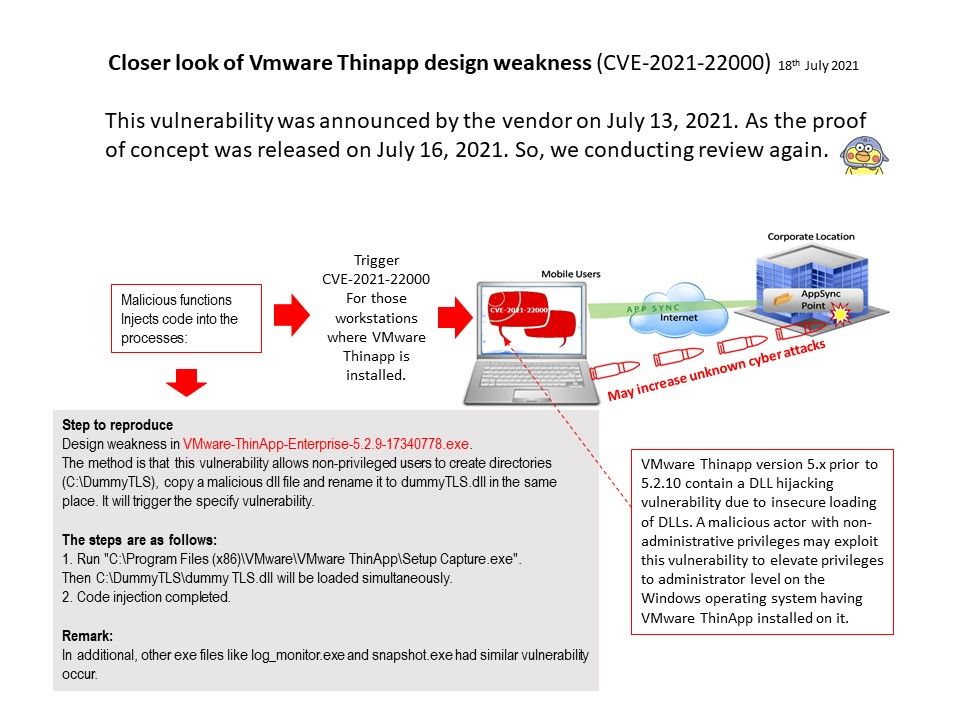
Closer look of the POC details:
Design weakness in VMware-ThinApp-Enterprise-5.2.9-17340778[.]exe.
The method is that this vulnerability allows non-privileged users to create directories (C[:]\DummyTLS), copy a malicious dll file and rename it to dummyTLS[.]dll in the same place.It will trigger the specify vulnerability.
The steps are as follows:
- Run “C[:]\Program Files (x86)\VMware\VMware ThinApp\Setup Capture[.]exe”.
Then C[:]\DummyTLS\dummy TLS.dll will be loaded simultaneously. - Code injection completed.
In additional, other exe files like log_monitor[.]exe and snapshot[.]exe had similar vulnerability occur.
VMware security advisory – https://www.vmware.com/security/advisories/VMSA-2021-0015.html