Preface: Internet of Things (IoT) and machine-to-machine (M2M) technologies need to use a messaging and connectivity protocol in order to exchange information from a remote location.
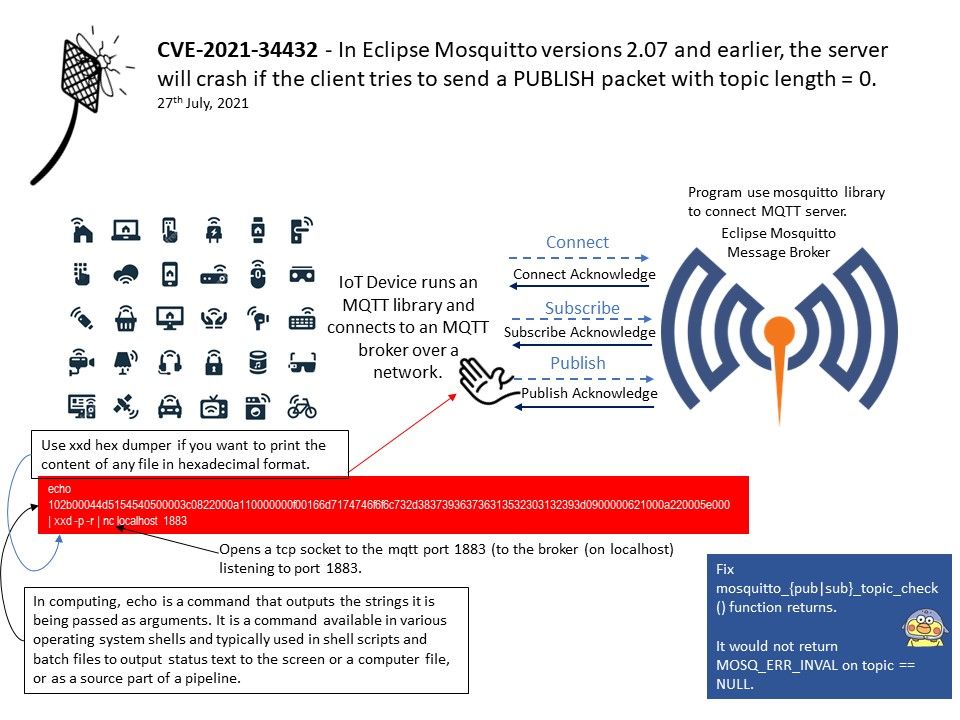
Background: MQTT is a binary-based protocol and has command and command acknowledgement format. So every time a client sends a command to the broker, the broker sends an acknowledgement. This communication protocol is actually based on the TCP/IP protocol. So first there will be a TCP connection establishment and then there will be MQTT connection establishment and then the data transfer will occur. After which TCP connection will be terminated.
An MQTT broker is a server that receives all messages from the clients and then routes the messages to the appropriate destination clients.
Vulnerability details: In Eclipse Mosquitto versions 2.07 and earlier, the server will crash if the client tries to send a PUBLISH packet with topic length = 0.
Remedy: The design weakness was patched in version 2.08.
Client library: Fix mosquitto_{pub|sub}_topic_check() functions not returning MOSQ_ERR_INVAL on topic == NULL.
Causes: Under following condition, it will returns MOSQ_ERR_INVAL if the topic string is too long.