Preface: A series of sequential read functions for seq operations are defined in fs/seq_file.c. These functions were first introduced in 2001, but have not been used much in the kernel before, and after the 2.6 kernel, many / The seq function is heavily used in proc’s read-only files.
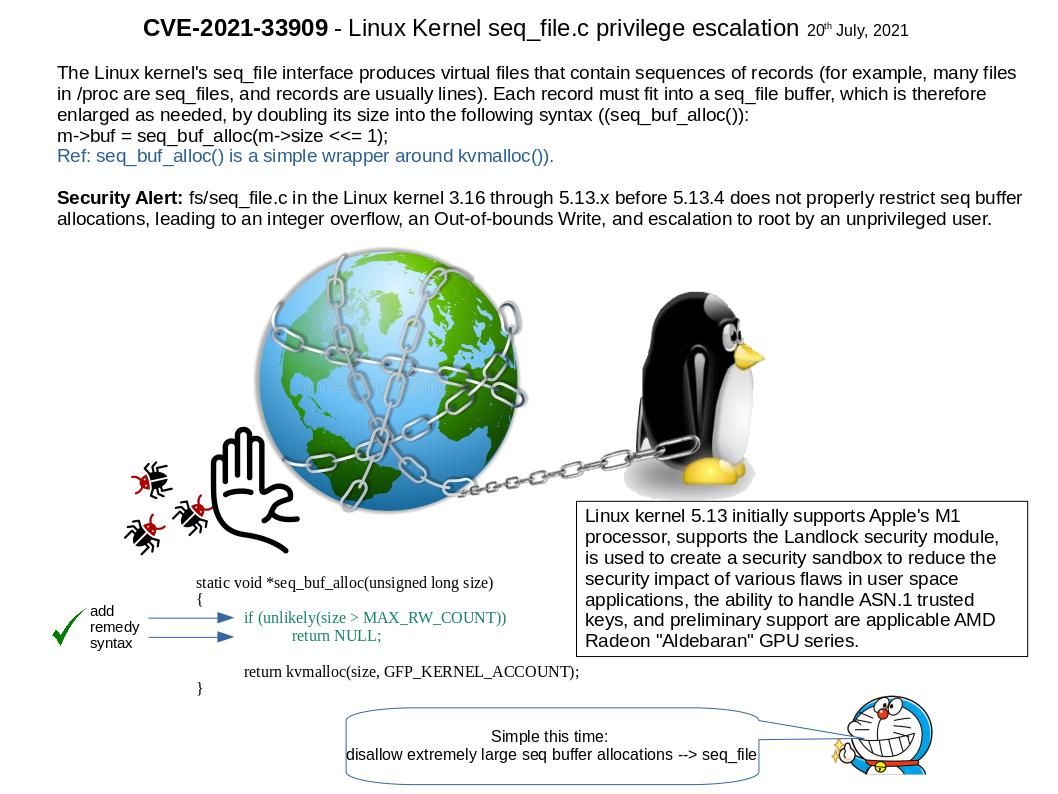
Synopsis: Linux kernel 5.13 initially supports Apple’s M1 processor, supports the Landlock security module, is used to create a security sandbox to reduce the security impact of various flaws in user space applications, the ability to handle ASN.1 trusted keys, and preliminary support are applicable AMD Radeon “Aldebaran” GPU series.
Background: About There are numerous ways for a device driver (or other kernel component) to provide information to the user or system administrator. One useful technique is the creation of virtual files, in debugfs, /proc or elsewhere. Virtual files can provide human-readable output without any special utilities. The Linux kernel’s seq_file interface produces virtual files that contain sequences of records.
Vulnerability details: s/seq_file[.]c in the Linux kernel 3.16 through 5.13.x before 5.13.4 does not properly restrict seq buffer allocations, leading to an integer overflow, an Out-of-bounds Write, and escalation to root by an unprivileged user. For more information on this matter, please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2021-33909