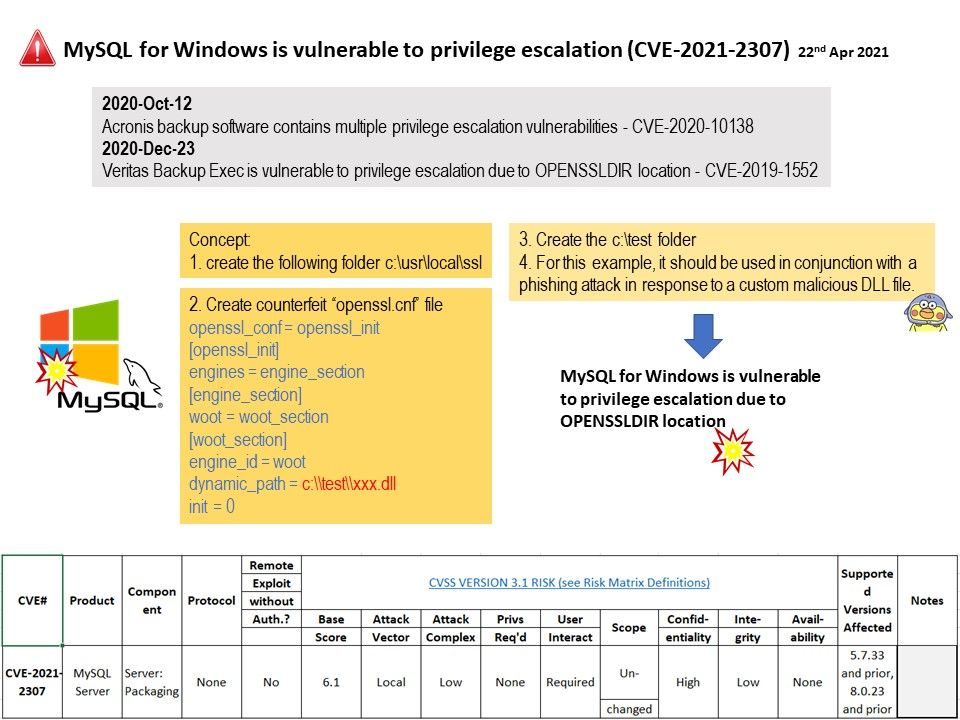
Preface: Similar design concepts rely on OpenSSL, and it is not news to encounter vulnerabilities. This time it was just a “Old wine in new bottles“.
Background: MySQL source build on WINDOWS using Mingw. therefore it find themselves looking at sub-directories of ‘C:/usr/local’, which may be world writable, which enables untrusted users to modify OpenSSL’s default configuration insert CA certificates, modify (or even replace) existing engine modules, etc.
For OpenSSL 1.0.2, ‘/usr/local/ssl’ is used as default for OPENSSLDIR on all Unix and Windows targets, including Visual C builds.
Vulnerability details: Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: Packaging). Supported versions that are affected are 5.7.33 and prior and 8.0.23 and prior. Easily exploitable vulnerability allows unauthenticated attacker with logon to the infrastructure where MySQL Server executes to compromise MySQL Server. For more details, please refer to the following link https://kb.cert.org/vuls/id/567764
Reference: The latest release of MySQL (version 8.0) has several new features including the incorporation of a transaction data dictionary that stores information about database objects. In addition, Atomic DDL or (Atomic data definition statements) allows statements to combine data diction updates, storage engine operations and binary log write associated with a DDL operation into a single, atomic transaction.