Preface: From a security perspective, what is the difference between configuration errors and vulnerabilities? Perhaps the potential impact are the same if it is involves privileges control function.
Product background: NSX-T Data Center supports cloud-native applications, bare metal workloads, multi-hypervisor environments, public clouds, and multiple clouds. NSX-T aim to protect applications with workload-level micro-segmentation and sophisticated security. Regardless of the physical network topology within and between the data center and the native public cloud, the network and security principles can be managed in a consistent manner.
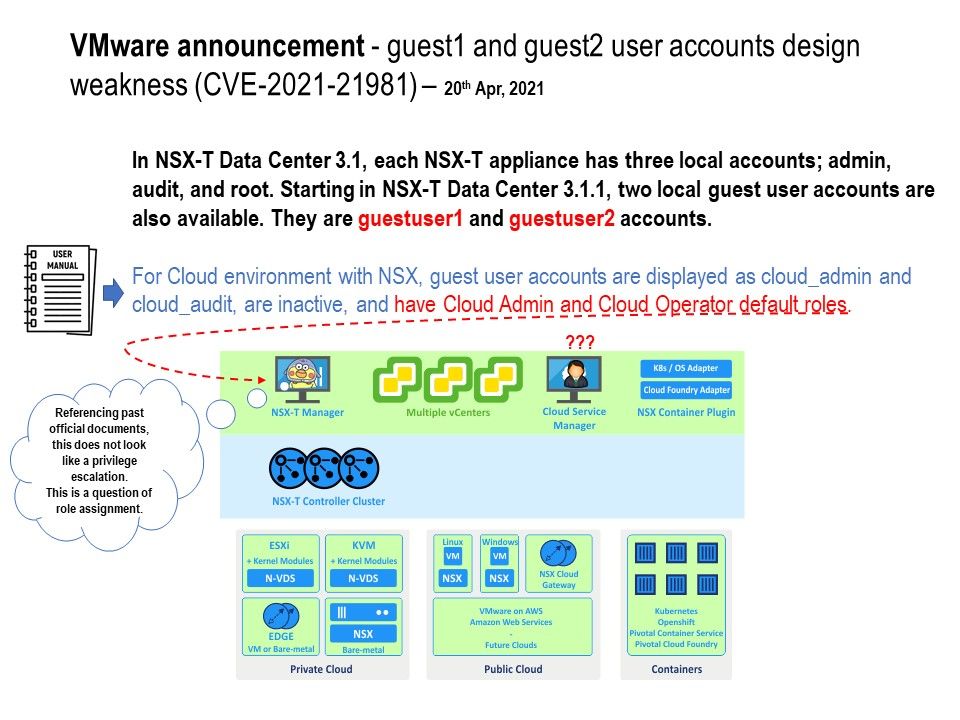
Vulnerability details: Official announcement said that a privilege escalation vulnerability in VMware NSX-T was privately reported to VMware. However when you read the old version of document. The document written down that For Cloud environment with NSX, guest user accounts are displayed as cloud_admin and cloud_audit, are inactive, and have Cloud Admin and Cloud Operator default roles. This is correct. Or is that right?
The official details link is here – https://www.vmware.com/security/advisories/VMSA-2021-0006.html