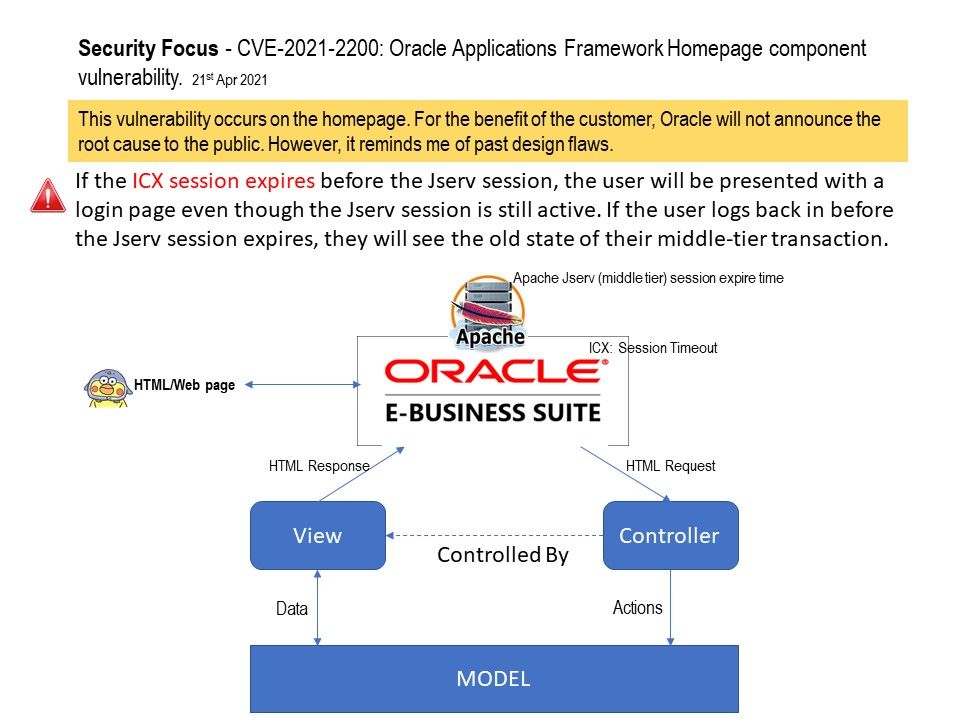
Background: OA Framework is based on J2EE technology called BC4J (Business Components for Java) The OA Framework is a Model-view-controller (MVC) framework built using J2EE (Java 2 Platform, Enterprise Edition) technologies.
Vulnerability details: According to CVE-2021-2200, the vulnerability occurs on the homepage. For the benefit of the customer, Oracle will not announce the root cause to the public. However, it remind me that a design weakness had occurred in the same place in past (see below):
“If the ICX session expires before the Jserv session, the user will be presented with a login page even though the Jserv session is still active. If the user logs back in before the Jserv session expires, they will see the old state of their middle-tier transaction.”
Perhaps this new vulnerability is different. It had high CVSS score (9.1). Meanwhile it is allow Remote Exploit without Auth. But vendor do not provide the root cause. So we must waiting for official announcement.
Oracle security-alerts, please refer to link – https://www.oracle.com/security-alerts/cpuapr2021.html
Reference: ICX: Session Timeout – Use this profile option to enforce an inactivity time-out. If a user performs no Oracle E-Business Suite operation for a time period longer than the time-out value (specified in minutes), the user’s session is disabled. The user is provided an opportunity to re-authenticate and re-enable a timed-out session. If re-authentication is successful, the session is re-enabled and no work is lost. Otherwise, Oracle E-Business Suite exits without saving pending work. If this profile option is set to 0 or NULL, then user sessions will never time out due to inactivity.