Preface: The DNS Client is capable of resolving the IP address of a host from the host’s name. It does this by sending DNS requests to a DNS Server. The IP address of a DNS Server is specified in the network interface configuration file or can be obtained from the DHCP Server for the Local Area Network.
Product background: Nucleus RTOS is a proven, reliable, and fully optimized RTOS. Nucleus has been used successfully deployed in highly demanding markets with rigorous safety and security requirements such as industrial systems, medical devices, airborne systems, automotive and more.
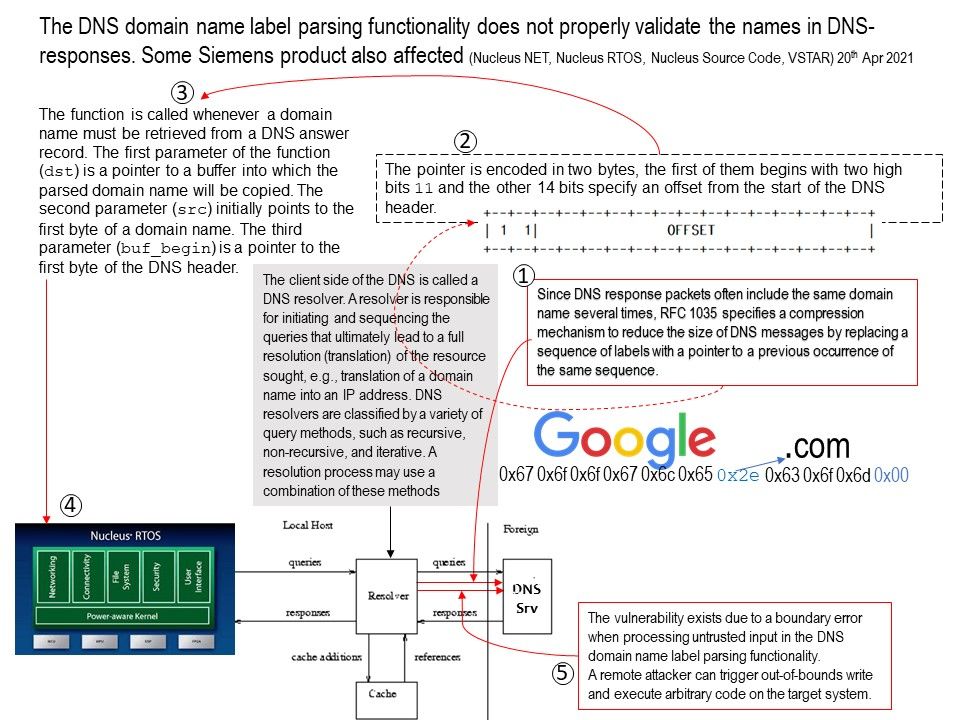
Vulnerability details: The DNS domain name label parsing functionality does not properly validate the names in DNS-responses. When DNS packet compression offset such that src jumps back to the same compression pointer, the TCP/IP stack will reach a Denial-of-Service condition. For more details, please refer to official announcement – https://cert-portal.siemens.com/productcert/pdf/ssa-705111.pdf
Workarounds: Avoid using DNS client of affected versions. When remote access is required, use secure methods, such as Virtual Private Networks (VPNs)