Preface: Doing web browsing and open document is our daily life. Opps! But it will hit a DoS vulnerability.
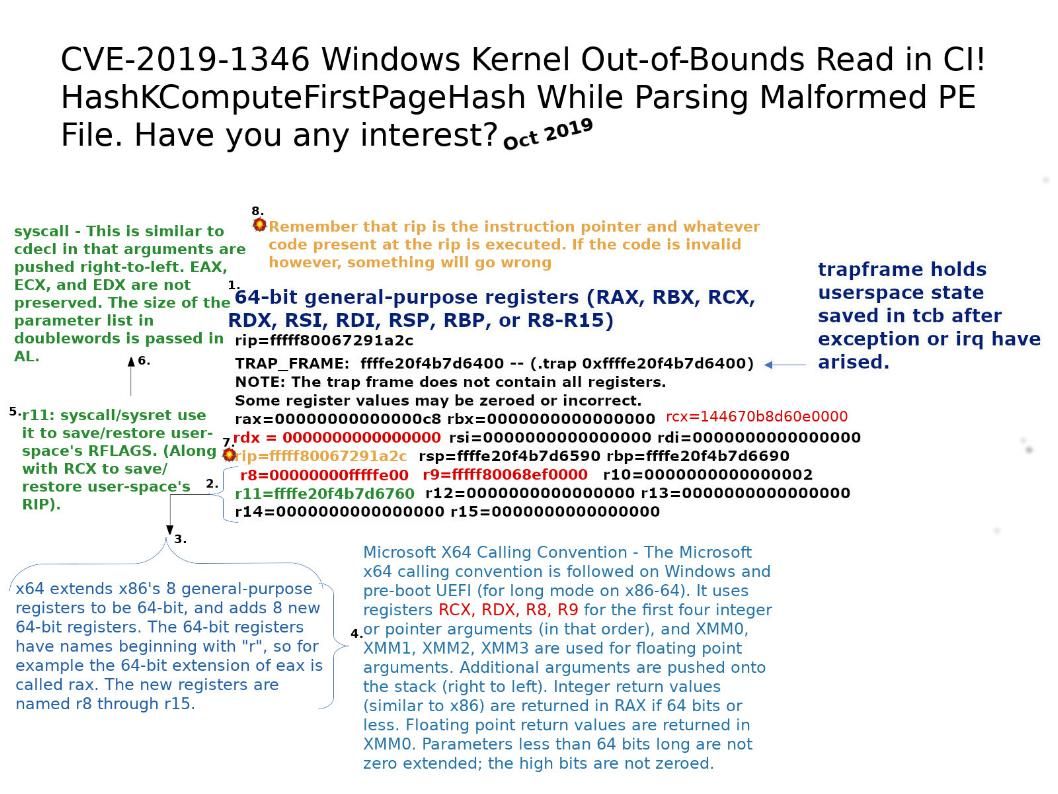
Background: x64 extends x86’s 8 general-purpose registers to be 64-bit, and adds 8 new 64-bit registers. The 64-bit registers have names beginning with “r”, so for example the 64-bit extension of eax is called rax. The new registers are named r8 through r15.
Remember that rip is the instruction pointer and whatever code present at the rip is executed. If the code is invalid however, something will go wrong .
Vulnerability details: A denial of service vulnerability exists when Windows improperly handles objects in memory. An attacker who successfully exploited the vulnerability could cause a target system to stop responding. The crash occurs when any system component calls LoadLibraryEx(LOAD_LIBRARY_AS_DATAFILE | LOAD_LIBRARY_AS_IMAGE_RESOURCE) against the file, either directly or through another API such as GetFileVersionInfoSizeExW() or GetFileVersionInfoW().
Official announcement – https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-1346