Preface: Existing internet service require DNS lookup function. See whether artificial intelligence world will be replaced this function?
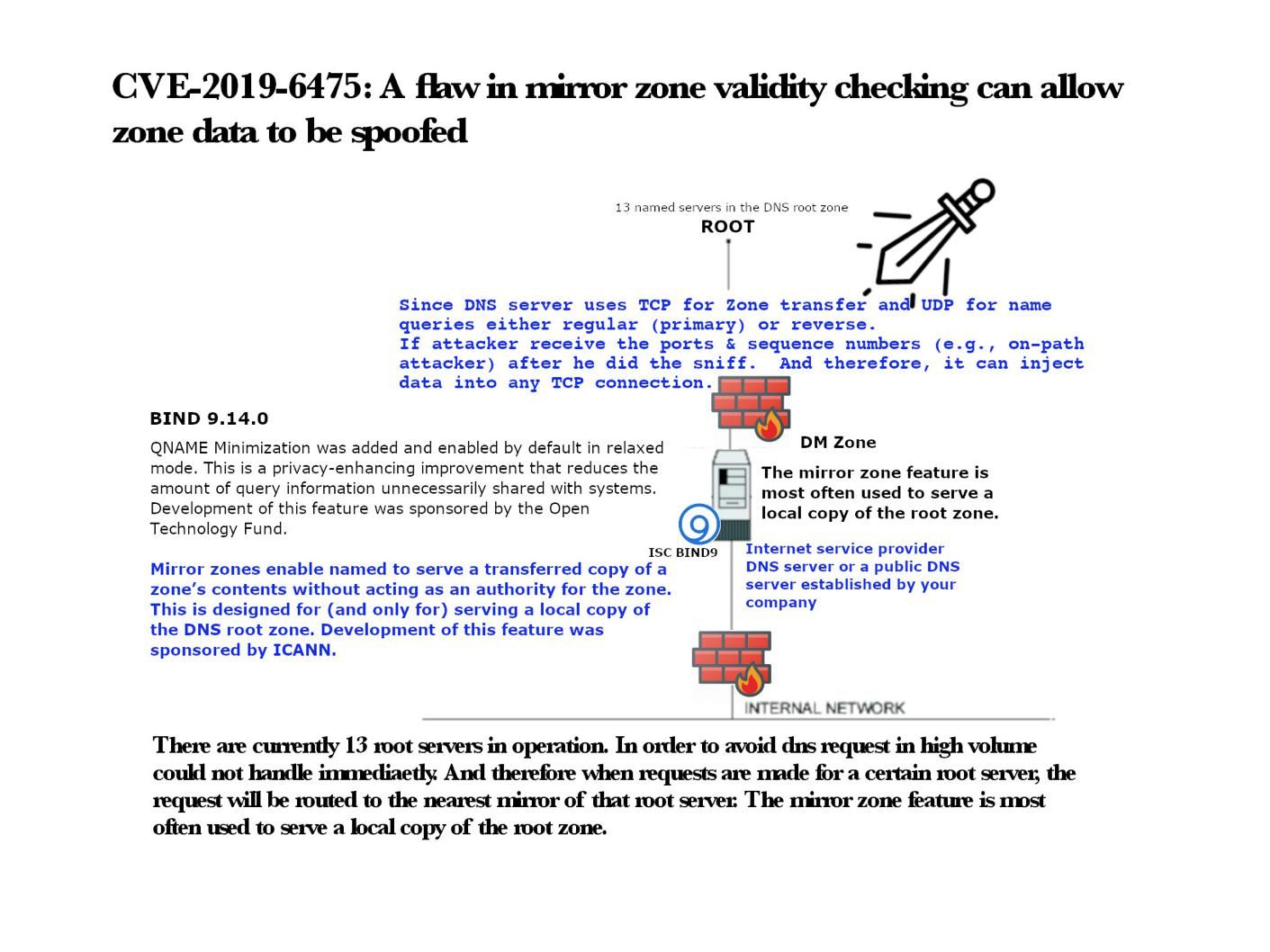
Background: There are currently 13 root servers in operation. In order to avoid DNS request in high volume could not handle immediately. And therefore when requests are made for a certain root server, the request will be routed to the nearest mirror of that root server. The mirror zone feature is most often used to serve a local copy of the root zone. Mirror zones are a BIND feature allowing recursive servers to pre-cache zone data provided by other servers.
Vulnerability details: Found design flaw in BIND version 9.14.0 up to 9.14.6, and 9.15.0 up to 9.15.4. Found that attacker was able to insert themselves into the network path between a recursive server using a mirror zone and a root name server.
The attack method is that the hacker sniffs on the network.
Since DNS uses TCP for Zone transfer and UDP for name queries either regular (primary) or reverse.
When he receive the ports & sequence numbers (e.g., on-path attacker), attacker can inject data into any TCP connection.
Impact:
An on-path attacker who manages to successfully exploit this vulnerability can replace the mirrored zone (usually the root) with data of their own choosing, effectively bypassing DNSSEC protection.
Official announcement – https://kb.isc.org/docs/cve-2019-6475