Background: Google Go Language is suitable for web development especially front-end development. Quite a lot of companies using GO. For instance Facebook, Twitter, YouTube, Apple, Dropbox, Docker, Soundcloud, Mozilla Firefox, The New York Times, Github, GOV.UK and UBER.
Vulnerability details: A vulnerability in the net/url package in Golang Go could allow an unauthenticated, remote attacker to bypass security restrictions on a targeted system. The affect product inlcudes version prior 12.12.7 and prior 1.11.12.
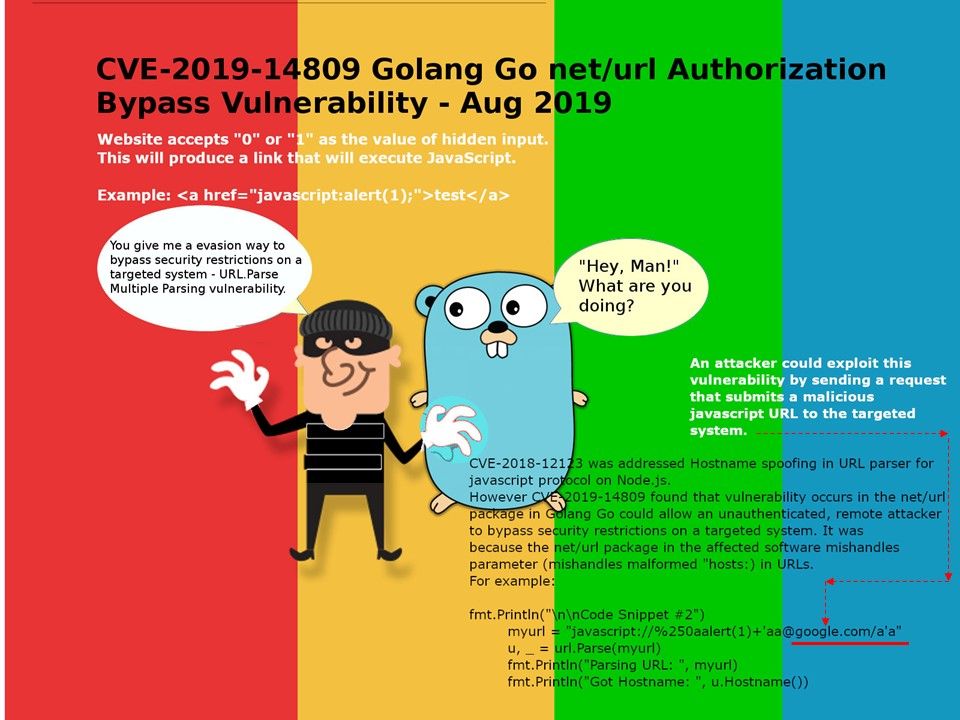
Observation: CVE-2018-12123 was addressed Hostname spoofing in URL parser for javascript protocol on Node.js.
However CVE-2019-14809 found that vulnerability occurs in the net/url package in Golang Go could allow an unauthenticated, remote attacker to bypass security restrictions on a targeted system. It was because because the net/url package in the affected software mishandles parameter (mishandles malformed “hosts:) in URLs. For more details, please see attached diagram for reference.
Remedy: Golang has released software updates at the following – link: https://github.com/golang/go/releases