Preface: ALPC (Advanced/Asynchronous Local Procedure Call) is a C/S model technology developed by Microsoft to replace LPC for native RPC.
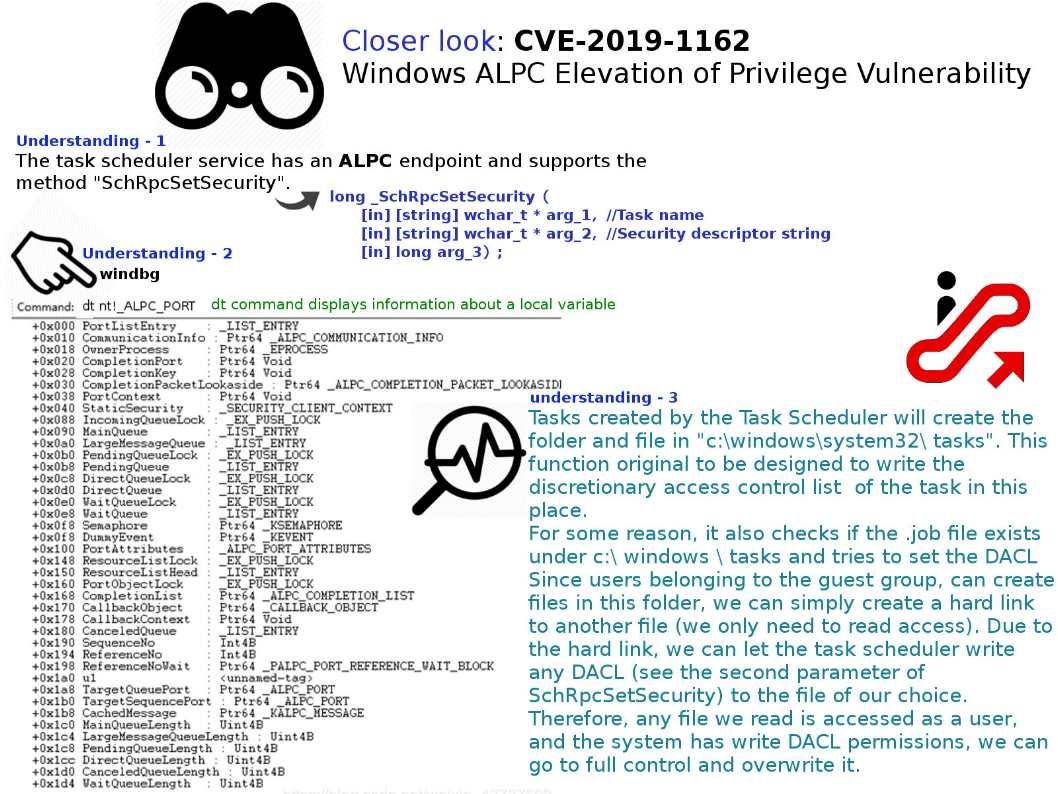
Vulnerability details: Tasks created by the Task Scheduler will create the folder and file in “c:\windows\system32\ tasks”. This function original to be designed to write the discretionary access control list of the task in this place. For some reason, it also checks if the .job file exists under c:\ windows \ tasks and tries to set the DACL
Since users belonging to the guest group, can create files in this folder, we can simply create a hard link to another file (we only need to read access). Due to the hard link, we can let the task scheduler write any DACL (see the second parameter of SchRpcSetSecurity) to the file of our choice. Therefore, any file we read is accessed as a user, and the system has write DACL permissions, we can go to full control and overwrite it.
Vendor announcement : https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-1162