Preface: PePe the frog, he will never die. PePe could appear anywhere. May be you can see him in political world or your whatsapp communications. Even CVE vulnerability record details.
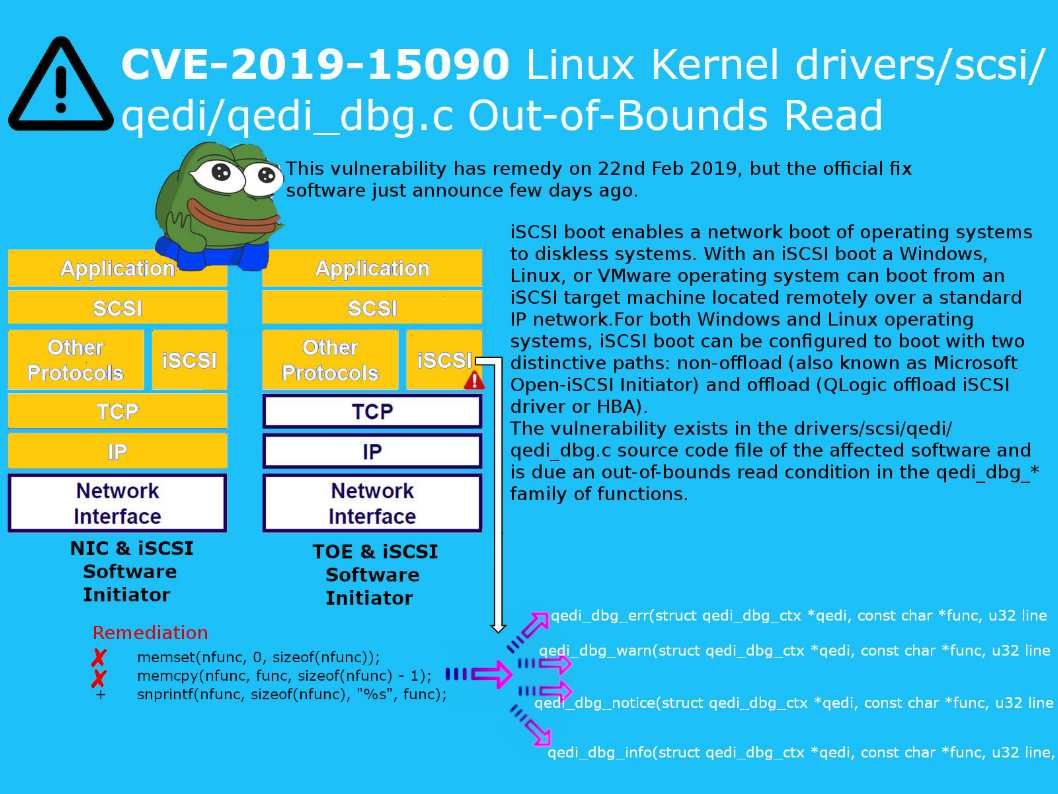
QLogic offload iSCSI driver (qedi_dbg.c) technical background – For both Windows and Linux operating systems, iSCSI boot can be configured to boot with two distinctive paths: non-offload (also known as Microsoft Open-iSCSI Initiator) and offload (QLogic offload iSCSI driver or HBA). iSCSI Offload uses the TCP Offload Engine (TOE) technology in network interface cards (NICs) to offload the processing of the TCP/IP stack to a network controller.
Vulnerability details: The vulnerability exists in the drivers/scsi/qedi/qedi_dbg.c source code file of the affected software and is due an out-of-bounds read condition in the qedi_dbg_* family of functions.
Common Functions in C/C++ memcpy()memset(). These functions are categorized into the subcategory transfer memory. With memcpy, you not only copy your own out-of-bounds area, such as some malloc block which was previously freed, but also an area from a completely different running program.
Remedy: Kernel.org has released software updates at the following link – https://www.kernel.org/