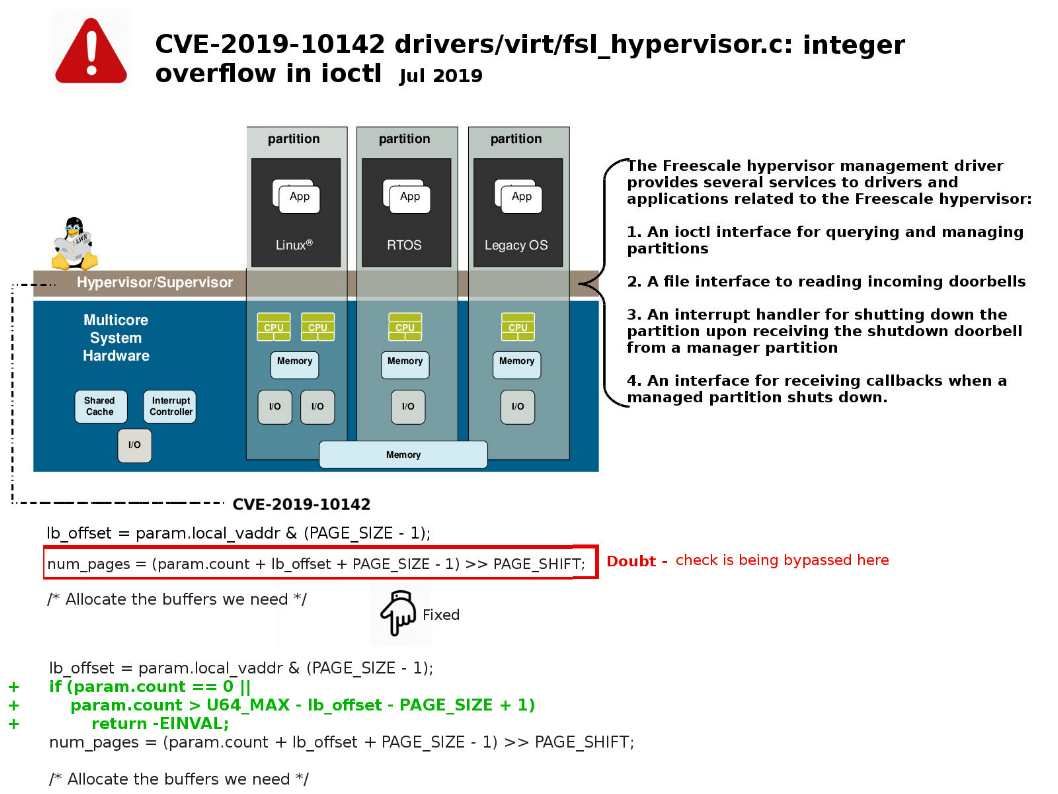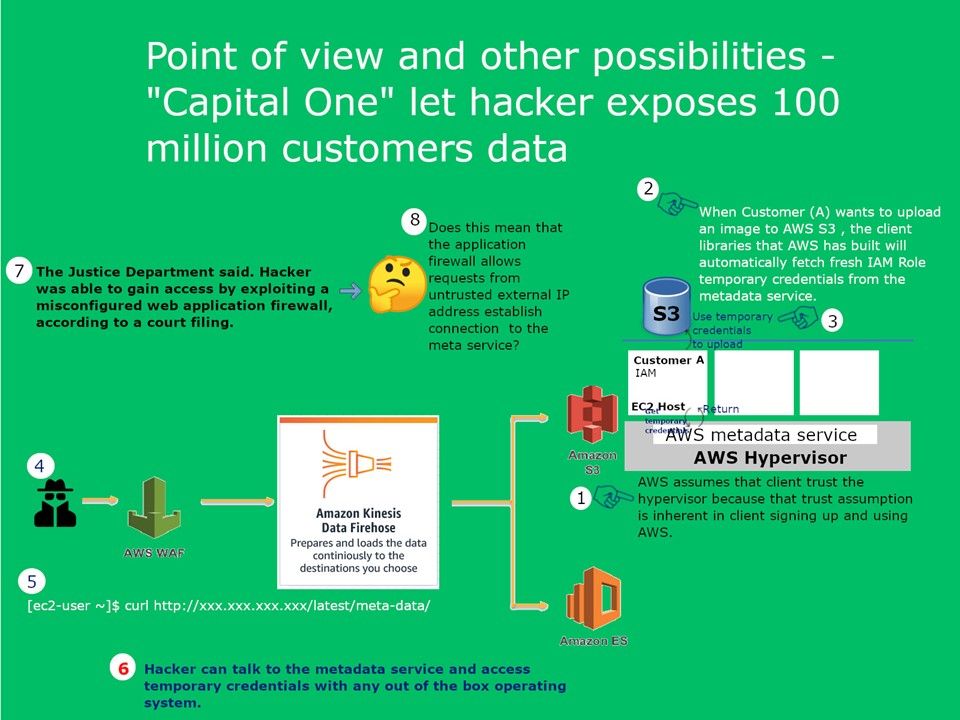
Cyber criminal is under arrested. She is accused of breaking into a “Capital One” computer facility and gaining access to 140,000 Social Security numbers, 1 million Canadian Social Insurance numbers and 80,000 bank account numbers.
Security Focus : Cyber criminal is under arrested. She is accused of breaking into a “Capital One” computer facility and gaining access to 140,000 Social Security numbers, 1 million Canadian Social Insurance numbers and 80,000 bank account numbers. Technical guy may known that there is a design limitation occurs on AWS. The metadata service provides temporary credentials. There is no authentication and no authorization to access the service. A mis-configure firewall policy will causes untrusted source establish connection to meta service. For more details, please refer to attach diagram.
Headline News – A hacker gained access to 100 million Capital One credit card applications and accounts
https://edition.cnn.com/2019/07/29/business/capital-one-data-breach/index.html