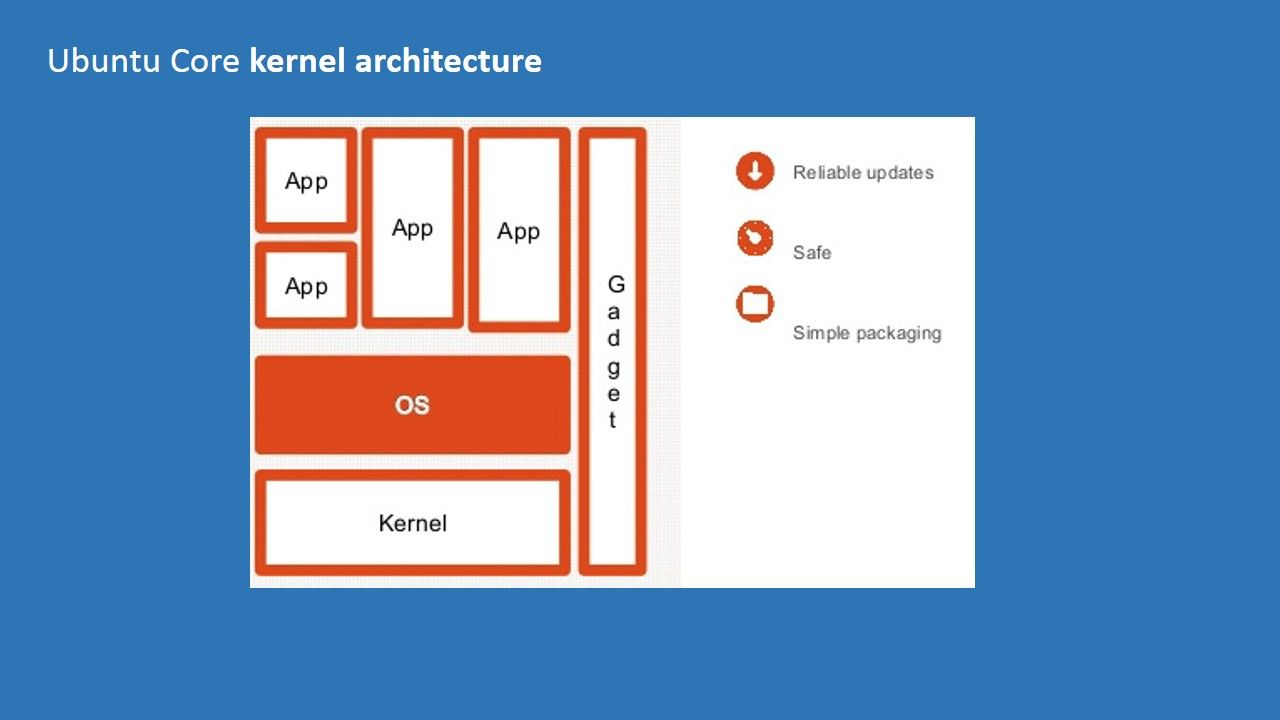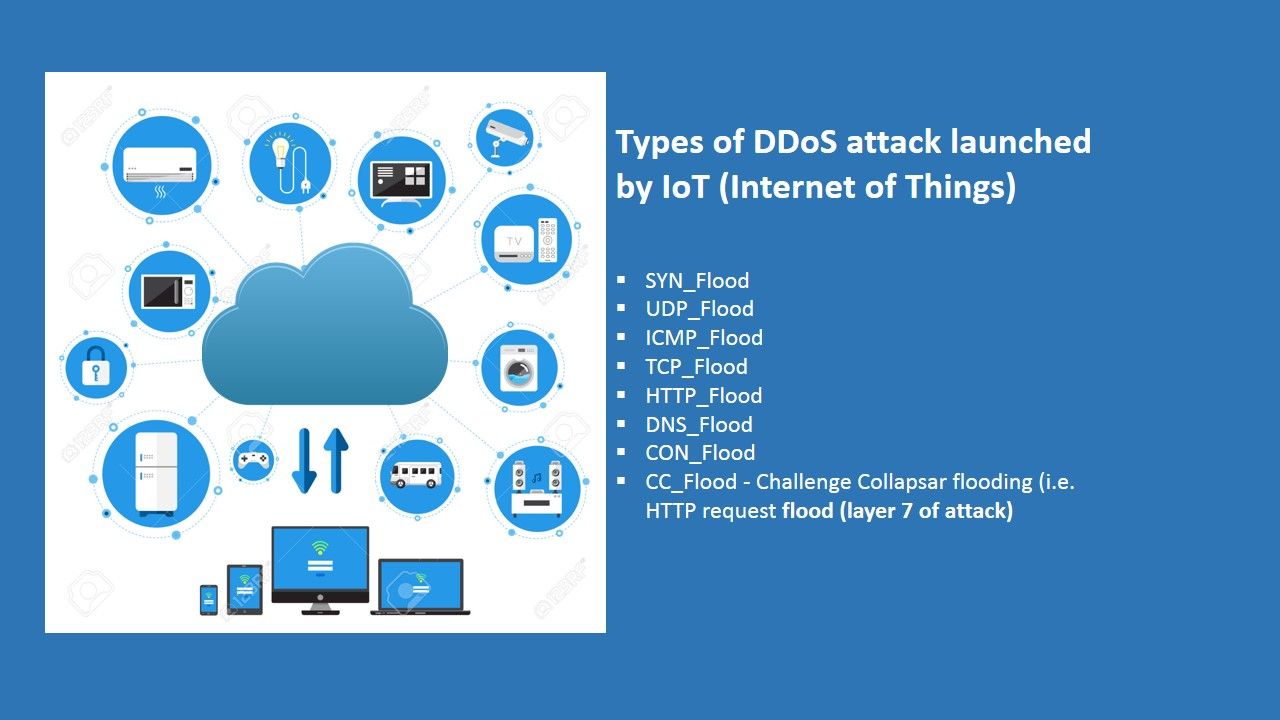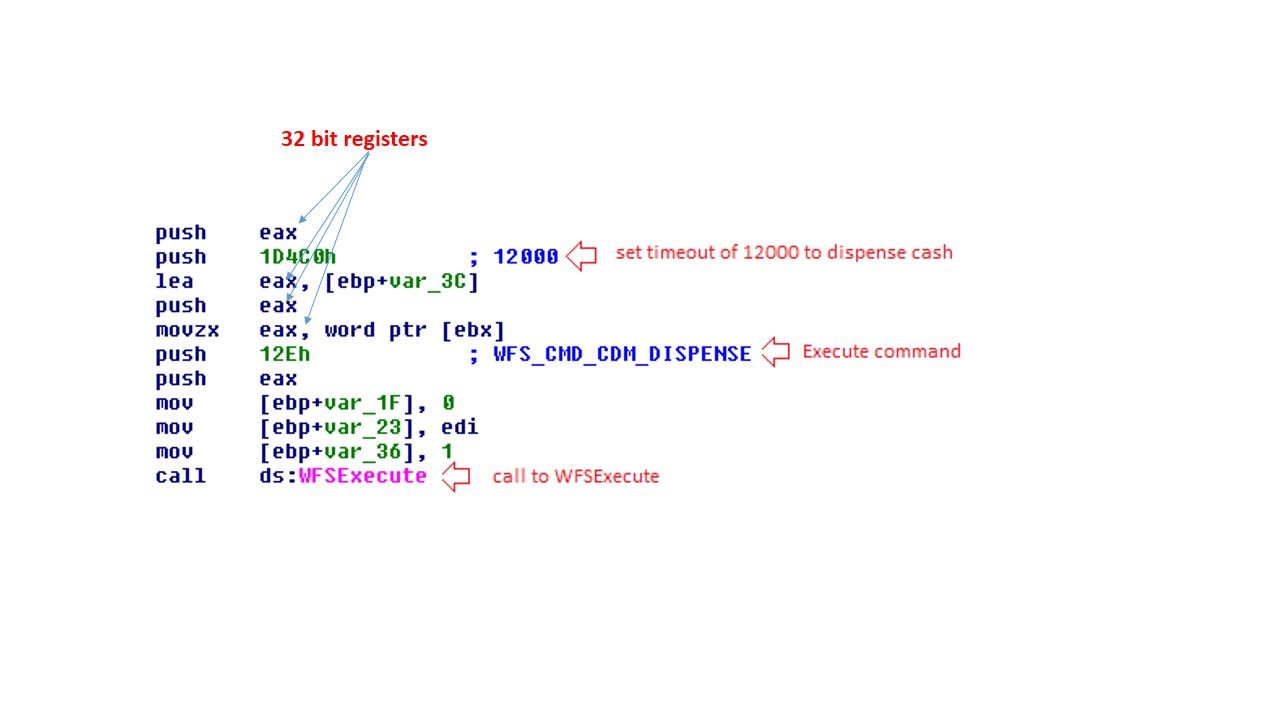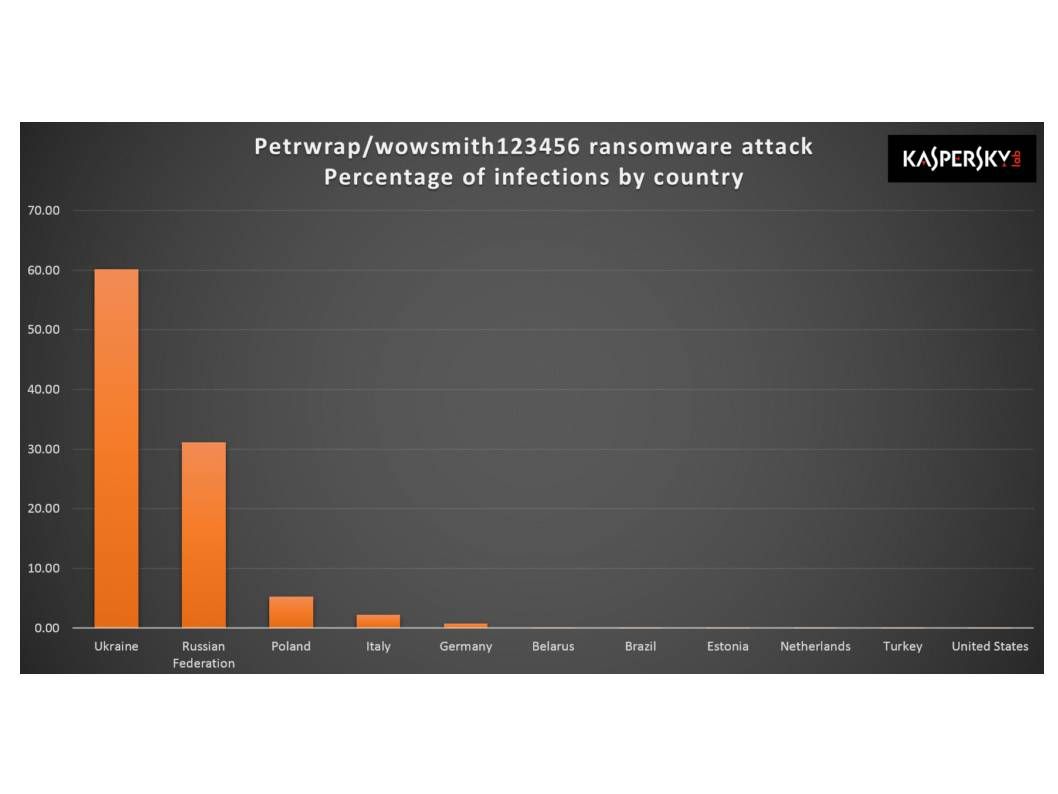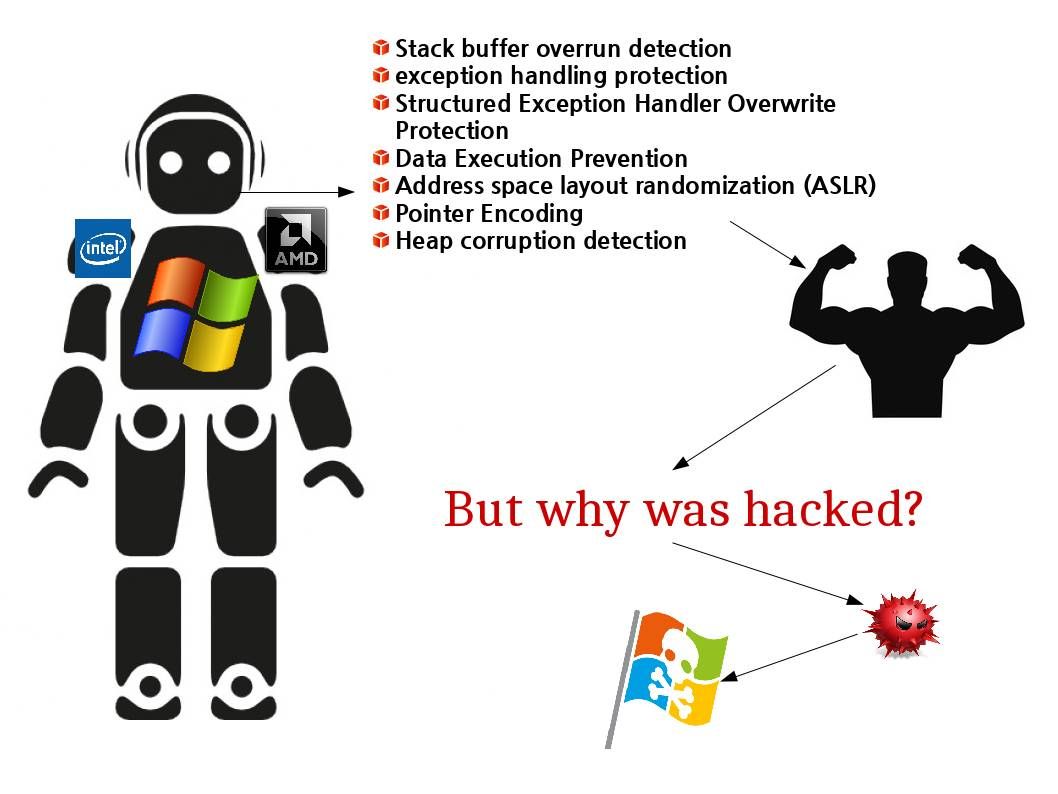
Preface:
A simple question was asked by kernel? Why I was hacked even though I have comprehensive protective system?
Background:
The windows Operating System development team fully understand relies on market anti virus might not protecting their core OS significantly. Since the computer user not only using Microsoft word processing application. They are allow the 3rd party application vendor run on top of their operating system.
They provides security defense mechanism to 3rd party software developers on their OS products since 2002. Such advanced protective mechanism also apply to windows XP SP2 and windows server 2003. 
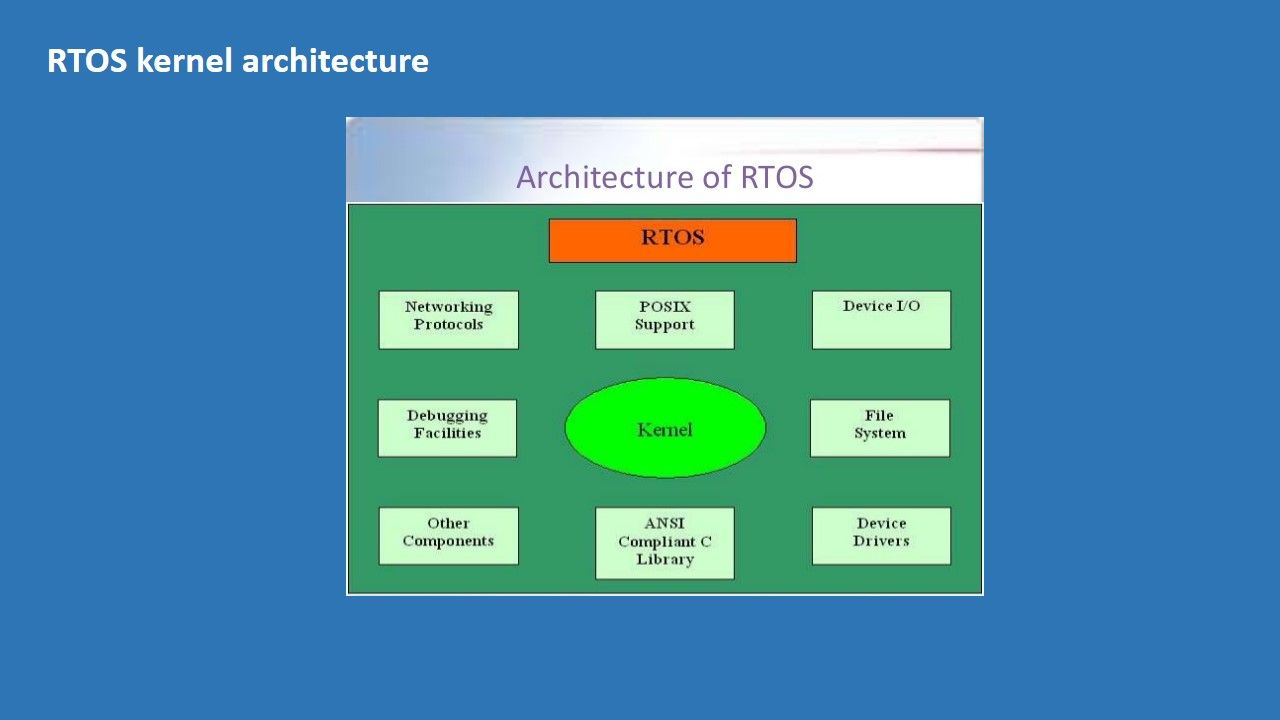
Introduction – Microsoft Comprehensive protective system for 3rd party application development (cookbook)

Top 3 protection features overview
Stack buffer overrun detection
The Detection capability was introduced to the C/C++ compiler in Visual Studio .NET. The /GS switch only inserts checks into function that it “recognizes as subject to buffer overrun problems.
Mitigation scheme – add below instruction in a commonly used header file to increase the number of functions protected by /GS:
#pragma strict_gs_check(on)
Preventing the SEH Overwrites with SEHOP
Structured Exception Handling (SEH) is a Windows mechanism for handling both hardware and software exceptions consistently. In many cases, an attacker will choose to overwrite the exception handler function pointer with an address that contains instructions that are equivalent to a pop reg, pop reg, ret. This allows an attacker to reliably execute arbitrary code by transferring control to the EstablisherFrame that the exception dispatcher passes as the second parameter when calling an exception handler. (see below diagram for reference)
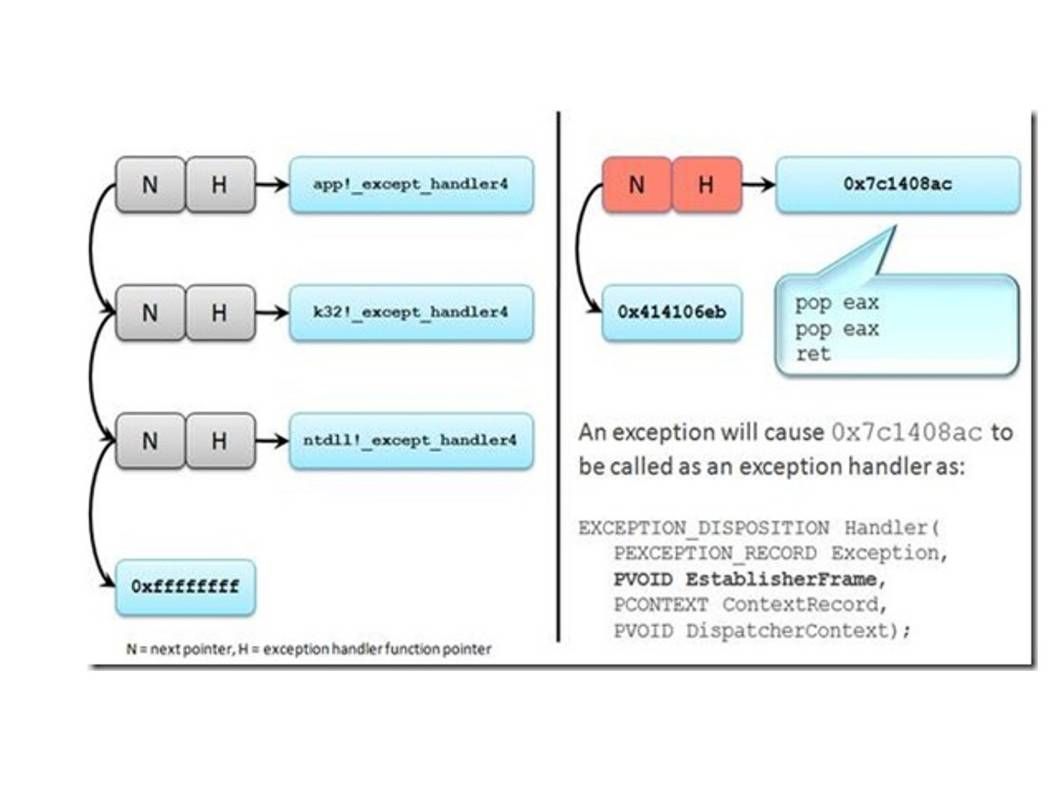
Remark: The SEH overwrite technique uses a software vulnerability to execute arbitrary code by abusing the 32-bit exception dispatching facilities provided by Windows.
Mitigation scheme:
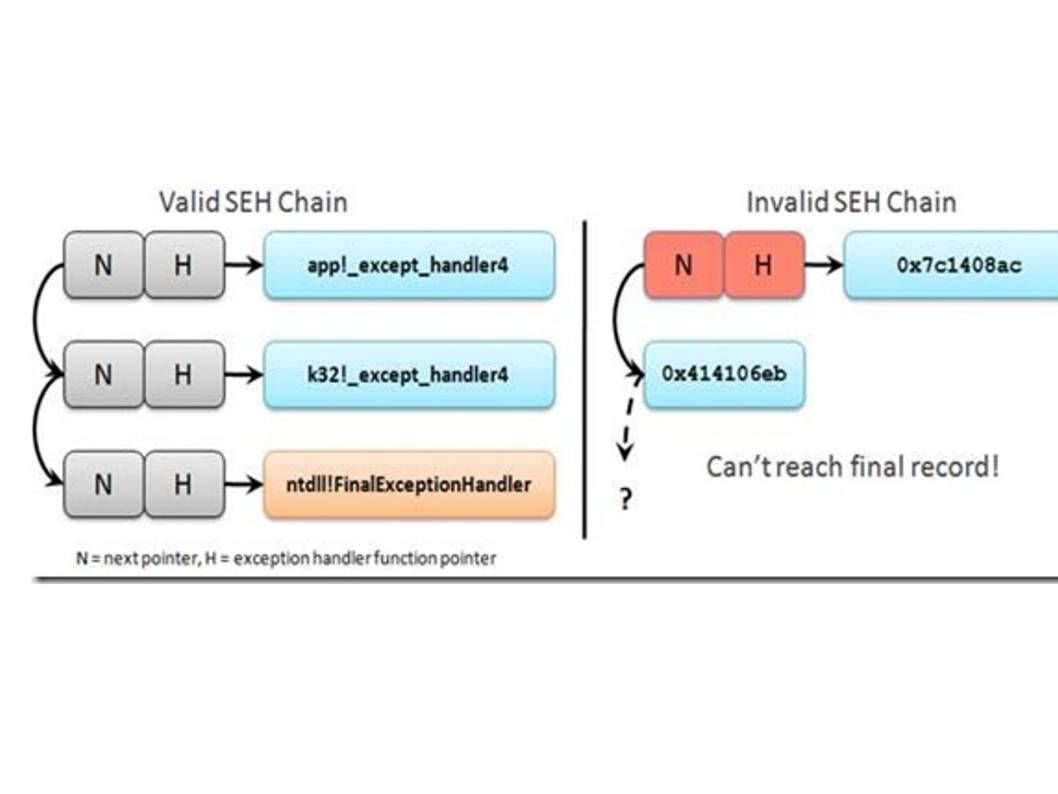
Adding dynamic checks to the exception dispatcher that do not rely on having metadata derived from a binary. This is the approach taken by SEHOP. SEHOP achieves this functionality in two distinct steps.
- Insertion of a symbolic exception registration record as the tail record in a thread’s exception handler list.
- Ensure that the symbolic record can be reached and that it is valid
Below diagram illustration of this logic:
Address space layout randomization (ASLR)
Address Space Layout Randomisation (ASLR) is a technology used to help prevent shellcode from being successful. It does this by randomly offsetting the location of modules and certain in-memory structures. Data Execution Prevention (DEP) prevents certain memory sectors, e.g. the stack, from being executed. By default, Windows Vista and later will randomize system DLLs and EXEs. In order to prevent an attacker from reliably jumping to, for example, a particular exploited function in memory, ASLR randomly arranges the address space positions of key data areas of a process, including the base of the executable and the positions of the stack, heap and libraries. It provides random stack and heap allocations and page load every time a process starts. Even though system process was hacked. The malware cannot execute shellcode theoretically.
Below articles are my research on ASLR topic on Virtual Machine and other operation system . Should you have interest. Please review below articles for reference.
Copy – He is great partner of virtual machine but he can kill VM simultaneously – address space layout randomization
The enemy of ASLR (Address space layout randomization) – memory leak
But why was hacked ?
Technical insight – It looks that using ASLR feature protect windows OS products are perfect. But the cyber security incident happened from past proven that ASLR is hard to avoid side-channel attack. For instance, the vulnerabilities (CVE-2016-7260 and CVE-2016-7259) could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application that could exploit the vulnerabilities and take control of an affected system. The windows OS system including 2008,2008R2, 2012,2012R2 and 2016.
Another example alert by Microsoft that attackers are using a blend of in-memory malware, legitimate pen-testing tools and a compromised updater to attack banks and tech firms. Similar type of attack was happened on 2013 of several South Korean organizations via a malicious version of an installer from storage service SimDisk.
Below details of information can help you to developing more idea in regards of this matter.
The operating system can promote a driver’s StartType to be a boot start driver depending on the BootFlags value specified in the driver’s INF. You can specify one or more (ORed) of the following numeric values in the INF file, expressed as a hexadecimal value:
- If a driver should be promoted to be a boot start driver on network boot, specify 0x1 (CM_SERVICE_NETWORK_BOOT_LOAD).
- If a driver should be promoted on booting from a VHD, specify 0x2 (CM_SERVICE_VIRTUAL_DISK_BOOT_LOAD)
- If a driver should be promoted while booting from a USB disk, specify 0x4 (CM_SERVICE_USB_DISK_BOOT_LOAD).
- If a driver should be promoted while booting from SD storage, specify 0x8 (CM_SERVICE_SD_DISK_BOOT_LOAD)
- If a driver should be promoted while booting from a disk on a USB 3.0 controller, specify 0x10 (CM_SERVICE_USB3_DISK_BOOT_LOAD).
- If a driver should be promoted while booting with measured boot enabled, specify 0x20 (CM_SERVICE_MEASURED_BOOT_LOAD).
- If a driver should be promoted while booting with verifier boot enabled, specify 0x40 (CM_SERVICE_VERIFIER_BOOT_LOAD).
- If a driver should be promoted on WinPE boot, specify 0x80 (CM_SERVICE_WINPE_BOOT_LOAD).
Windows registry: Turn on/off ASLR feature: (see below)
ASLR by setting HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management\MoveImages
Summary:
ASLR does not affect runtime performance. However it might slow down the initial loading of modules. But it is not in full capability to protect your windows OS system.
A reminder . Do not ignore unimportant item.