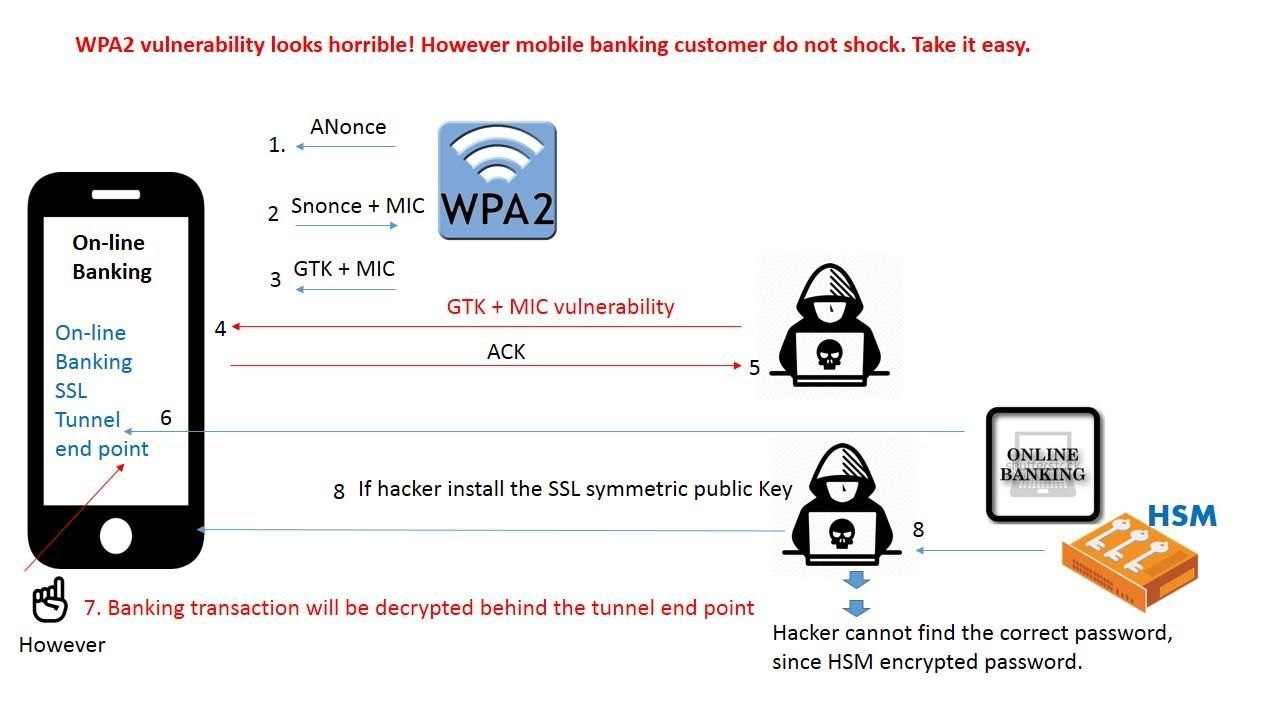
WPA2 vulnerability found. But online Banking system customer do not shock. Take it easy. The WPA2 wireless encryption scheme looks secure before specifics vulnerability occurred. Security expert found that hacker is able to relies on 3rd handshake doing injection which causes man-in-the-middle of attack. As a result your wireless network data traffic will be hunted by hacker. The data includes on-line banking credentials, social media credentials,….etc. But if you think it over. The SSL tunnel end point of online banking web application is seat on your mobile. Hacker must install the web server SSL public PKI key certificate in the 1st phase, otherwise he cannot view the data embedded in the traffic pattern. Perhaps hacker already install the public cert. However a HSM will be protect your password from online banking system. Since password will be shown as random code. Hacker cannot reuse. How about VISA 3D secure method? You will receive SMS alert of your payment transactions finally. You can verify by yourself. For more detail about the WPA2 vulnerability, please refer below url for reference.
Hi are using WordPress for your blog platform? I’m new to the blog world but I’m trying to get started and create my own. Do you require any coding knowledge to make your own blog? Any help would be really appreciated!|
I simply want to mention I am just new to blogging and absolutely enjoyed your web-site. Almost certainly I’m want to bookmark your site . You certainly have exceptional articles and reviews. Thanks a lot for sharing with us your blog.
whoah this blog is wonderful i love reading your articles. Keep up the great work! You know, lots of people are hunting around for this info, you could help them greatly.