Preface: Sometimes misconfiguration or abuse will be transformed as a vulnerability.
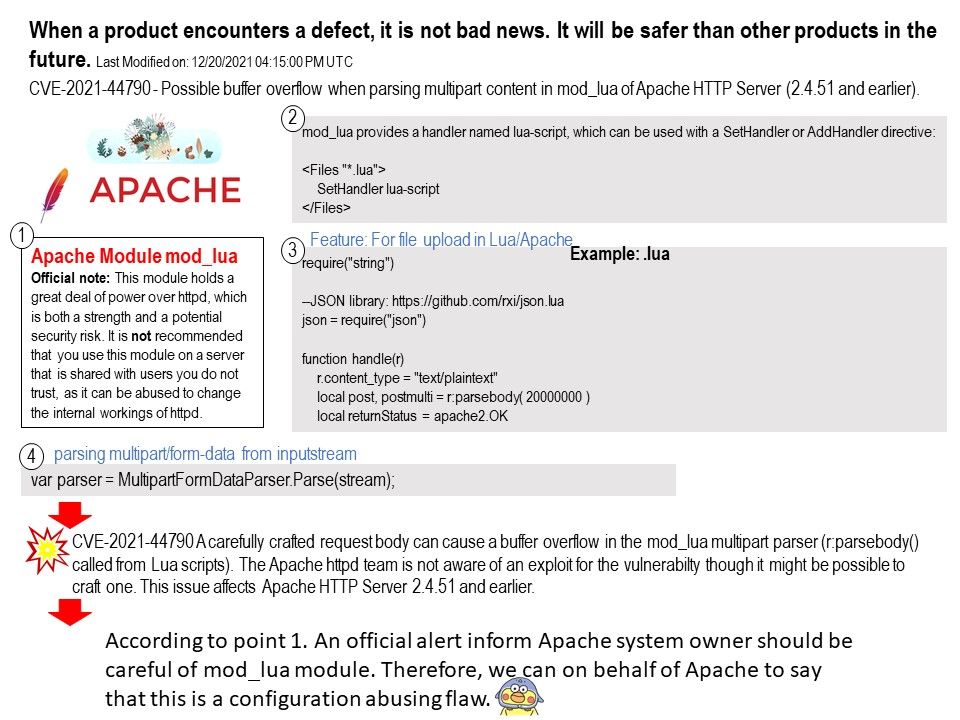
Background: Apache Module mod_lua (Official note) -This module holds a great deal of power over httpd, which is both a strength and a potential security risk. It is not recommended that you use this module on a server that is shared with users you do not trust, as it can be abused to change the internal workings of httpd.
The basic module loading directive is shown as follow: LoadModule lua_module modules/mod_lua[.]so.
Remark: mod_lua provides a handler named lua-script, which can be used with a SetHandler or AddHandler directive.
Vulnerability details: CVE-2021-44790 A carefully crafted request body can cause a buffer overflow in the mod_lua multipart parser (r:parsebody() called from Lua scripts).
The Apache httpd team is not aware of an exploit for the vulnerabilty though it might be possible to craft one. This issue affects Apache HTTP Server 2.4.51 and earlier.
Comment: According to point 1. The official warning informs Apache system owners to be careful with mod_lua modules.
So we can say on behalf of Apache that this is a configuration abuse defect.
Reference: https://www.openwall.com/lists/oss-security/2021/12/20/4