Preface: CISA urges vigilance on the VMware Workspace ONE UEM console.
Background: The aim of configure the httphandler for display blobs (Binary Large Object) such as an image, a video or a file.
In a nutshell the blobhandler allows us to get an URL to diplay a blob stored in our database.Whether is there any cyber security on this method? As far as we know, it is possible to Call HTTPhandler from jQuery, Pass data and retrieve in JSON format. A vulnerability remediation has been released by vendor last Friday (16th Dec, 2021). A Server Side Request Forgery (SSRF) vulnerability in VMware Workspace ONE UEM console was privately reported to VMware. Patches and workarounds are available to address this vulnerability in affected VMware products. The issue has been mitigated for VMware-hosted Workspace ONE consoles. For more details, please refer the link – https://www.vmware.com/security/advisories/VMSA-2021-0029.html
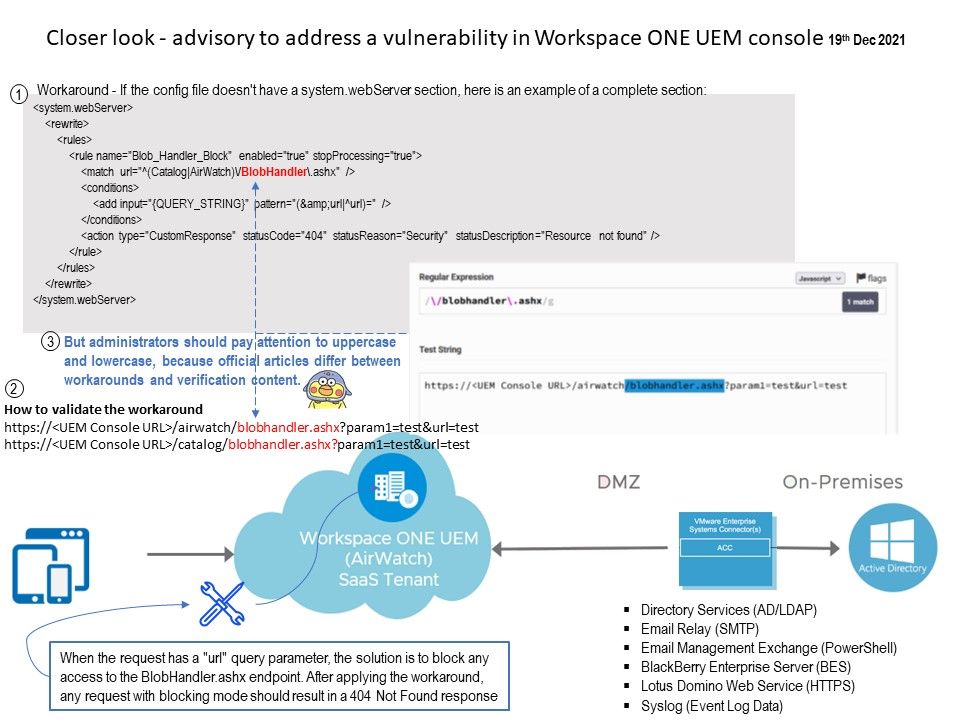
Observation: A workaround has been given by vendor. When the request has a “url” query parameter, the solution is to block any access to the BlobHandler.ashx endpoint. After applying the workaround, any request with blocking mode should result in a 404 Not Found response. For more details. please refer to link – https://kb.vmware.com/s/article/87167
Not sure whether is there another regular expression embedded in web server side? Otherwise, VMware administrator should be careful about the case sensitive matter.