Preface: Perhaps when you do the web scan or web penetration test. XSS will be easy to find out. However people has contempt this matter.
How to avoid XSS happen?
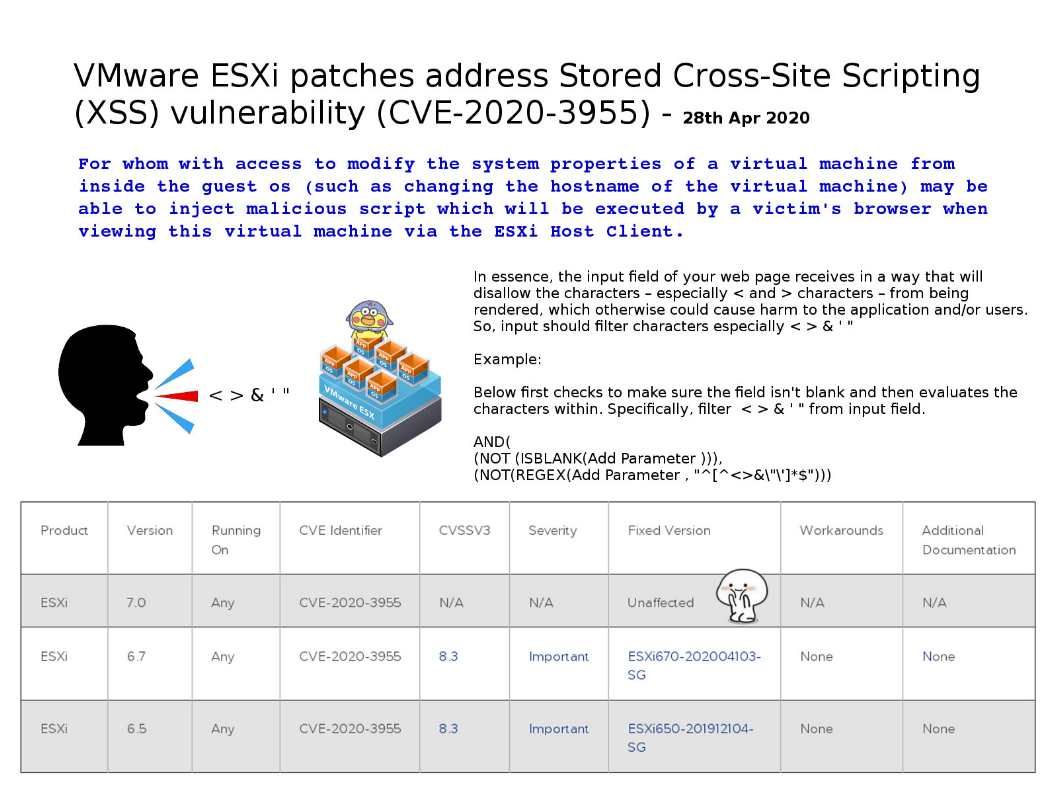
1. Input should filter characters especially < > & ‘ ” .
2. Whitelisting and input validation are more commonly associated with SQL injection, they can also be used as an additional method of prevention for XSS.
3. Sanitizing user input.
About CVE-2020-3955: For whom with access to modify the system properties of a virtual machine from inside the guest os (such as changing the hostname of the virtual machine) may be able to inject malicious script which will be executed by a victim’s browser when viewing this virtual machine via the ESXi Host Client.
Remedy: VMware official announcement – https://www.vmware.com/security/advisories/VMSA-2020-0008.html