Preface: Friendly speaking, the similar types of attack apply to all Linux base devices including firewall.
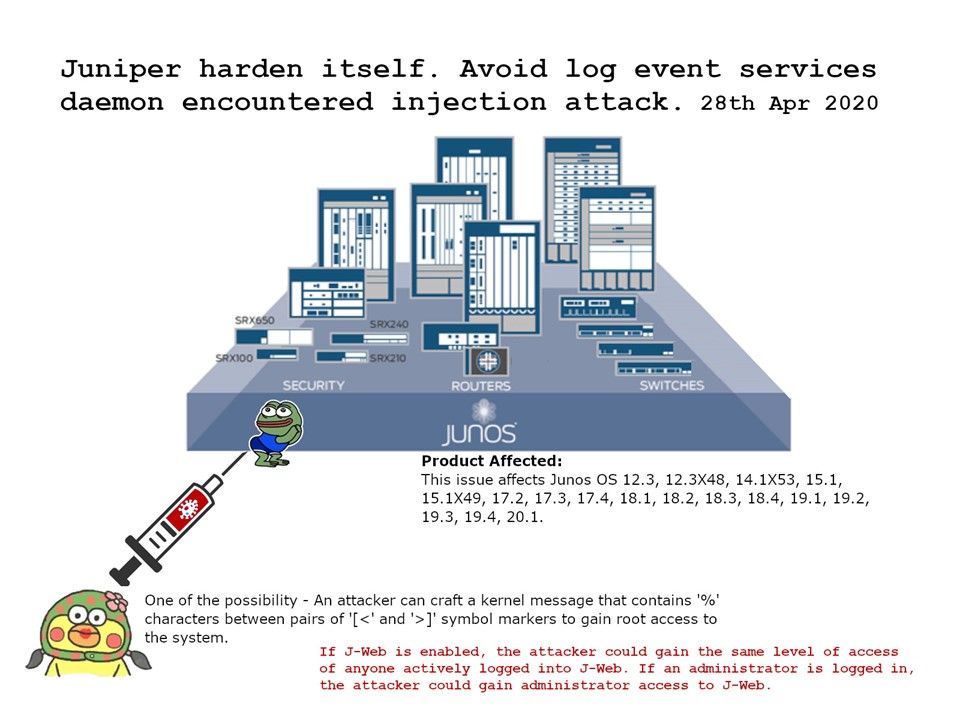
The impact of this vulnerability – If J-Web is enabled, the attacker could gain the same level of access of anyone actively logged into J-Web. If an administrator is logged in, the attacker could gain administrator access to J-Web.
My observation: One of the possibility is that an attacker can craft a kernel message that contains ‘%’ characters between pairs of ‘[<‘ and ‘>]’ symbol markers to gain root access to the system. Perhaps if the attacker goal to do surveillance, he can delete the log events and fool the SIEM system. Since SIEM log event correlation functions relies on log event.
Official announcement – https://kb.juniper.net/InfoCenter/index?page=content&id=JSA11021