Preface: Perhaps my alert late for 3 days, but the specify vulnerability hide himself in webLogic product for few years!
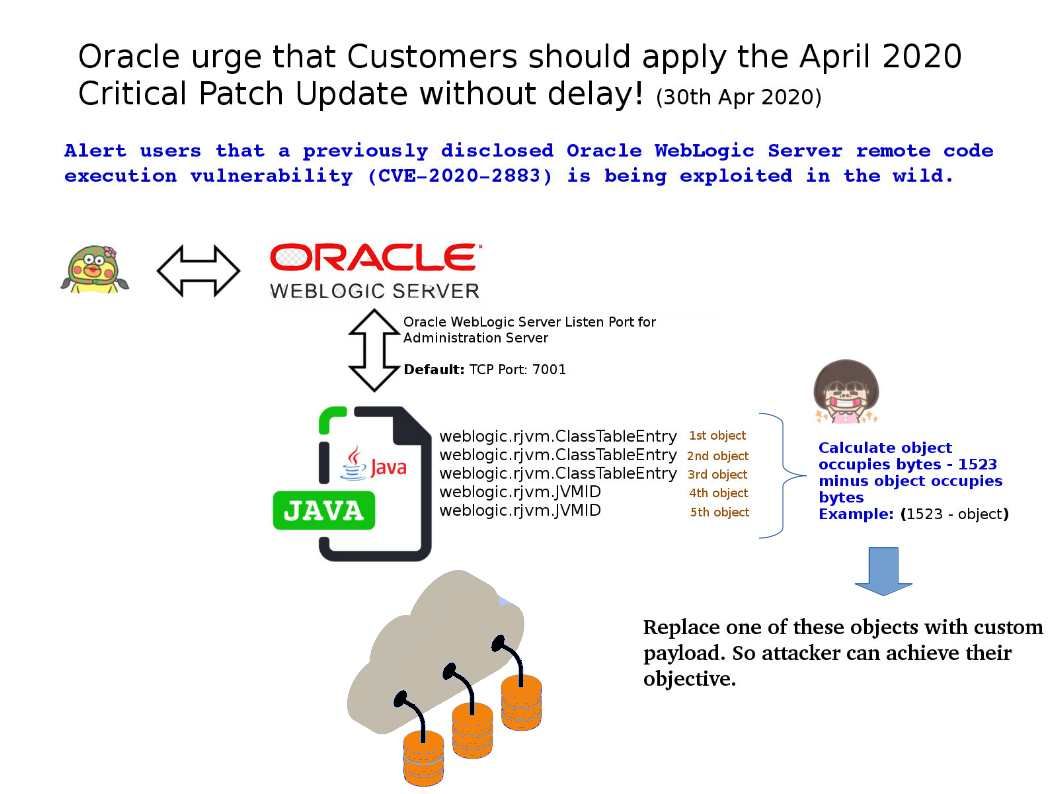
Vulnerability details: Alert users that a previously disclosed Oracle WebLogic Server remote code execution vulnerability (CVE-2020-2883) is being exploited in the wild. You can read the official announcement in following link – https://blogs.oracle.com/security/apply-april-2020-cpu
One of the exploit methods – The attacker can locate all of the objects by packet capture. For more details, please refer to attached diagram for reference. As a result, the attacker can replace these objects with his malicious payload. Since the server receives the data and unpacks (deserializes) without integrity check. And therefore it let attacker execute the malicious code on the underlying WebLogic core, allowing the attacker to take control over unpatched systems.