Preface: Since we launched it in 2014, Kubernetes running strong. It is becoming “the Linux of the cloud,” according to Jim Zemlin, Executive Director of the Linux Foundation. Analysts estimate that 54 percent of Fortune 100 companies use Kubernetes across a spectrum of industries including finance, manufacturing, media, and others.
Giant will sick as normal people (so called vulnerability):
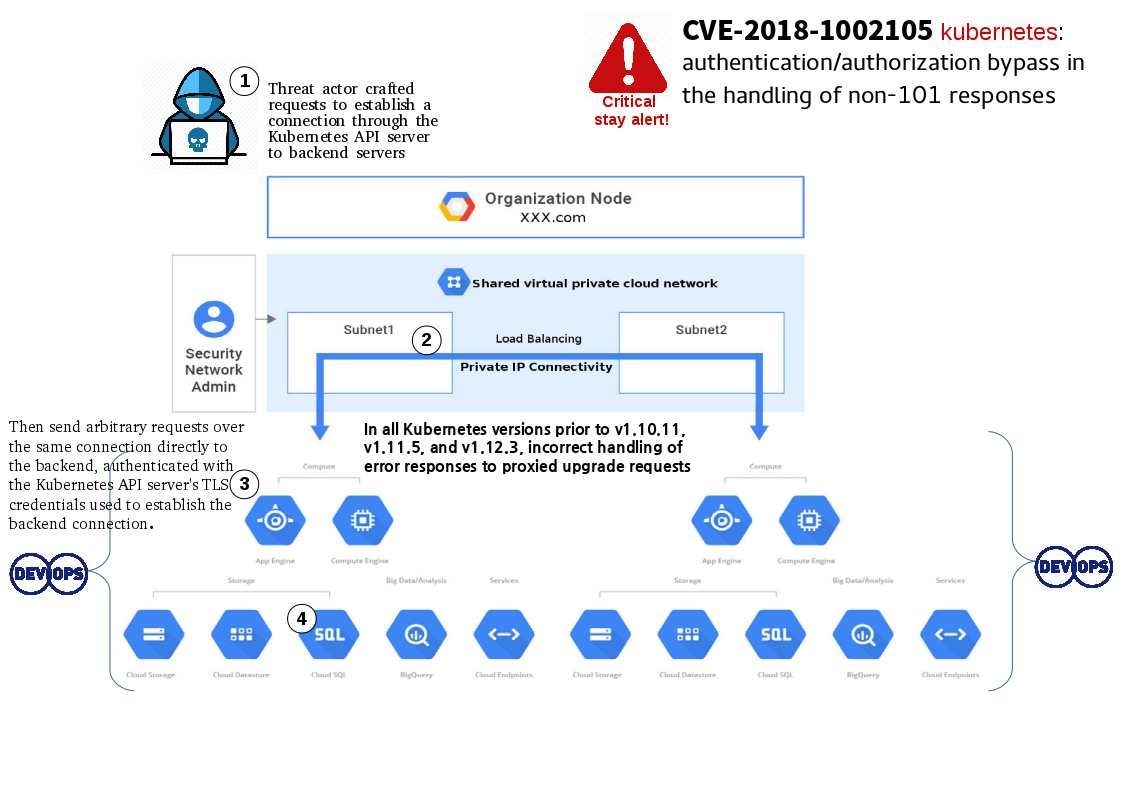
Critical – CVE-2018-1002105 kubernetes: authentication/authorization bypass in the handling of non-101 responses. Reference: https://access.redhat.com/security/cve/cve-2018-1002105
CVE-2018-1002101 – In Kubernetes versions 1.9.0-1.9.9, 1.10.0-1.10.5, and 1.11.0-1.11.1, user input was handled insecurely while setting up volume mounts on Windows nodes, which could lead to command line argument injection. Reference:
Reference: https://github.com/kubernetes/kubernetes/issues/65750
CVE-2018-1002103 – The attacker can use DNS rebinding to indirectly make requests to the Kubernetes Dashboard, create a new Kubernetes Deployment running arbitrary code. If minikube mount is in use, the attacker could also directly access the host filesystem.
Reference: https://github.com/kubernetes/minikube/issues/3208