Preface: Heard that Long-term support (LTS) for Linux kernels is being reduced from six to two years now.
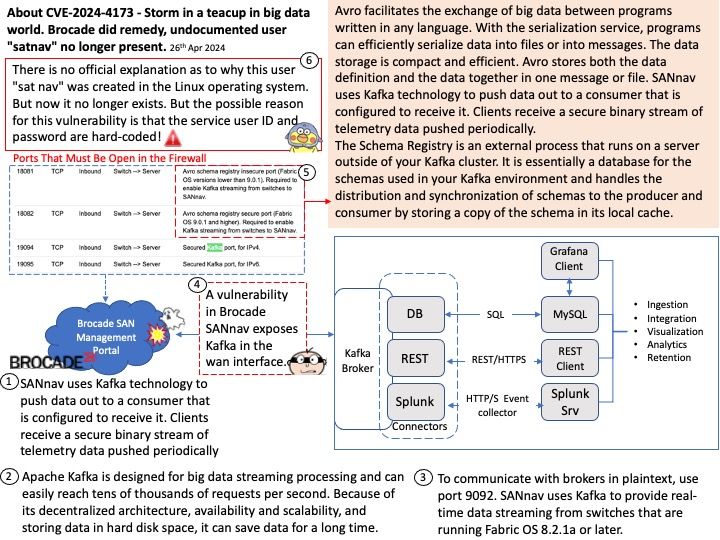
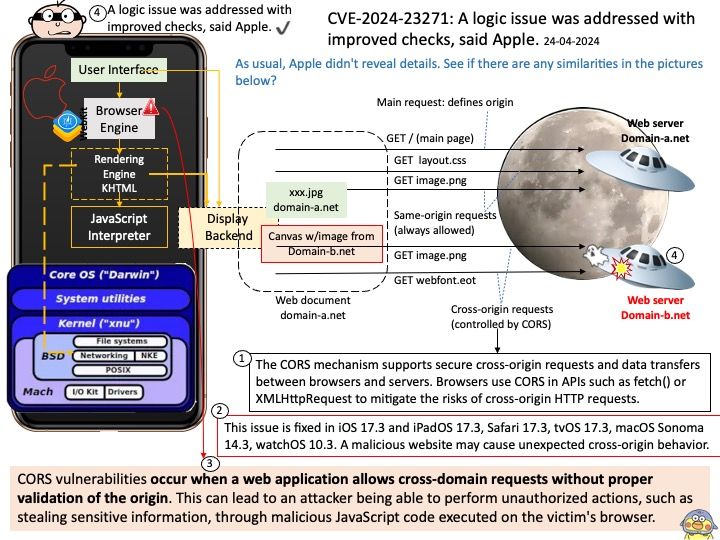
Background: Greg Kroah-Hartman is a major Linux kernel developer. As of April 2013, he is the Linux kernel maintainer for the -stable branch, the staging subsystem, USB, driver core, debugfs, kref, kobject, and the sysfs kernel subsystems, Userspace I/O, and TTY layer.
What will be the next LTS kernel?
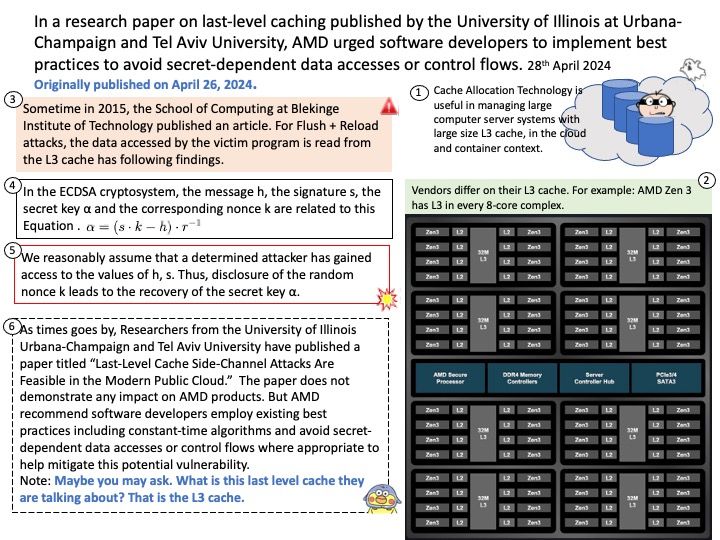
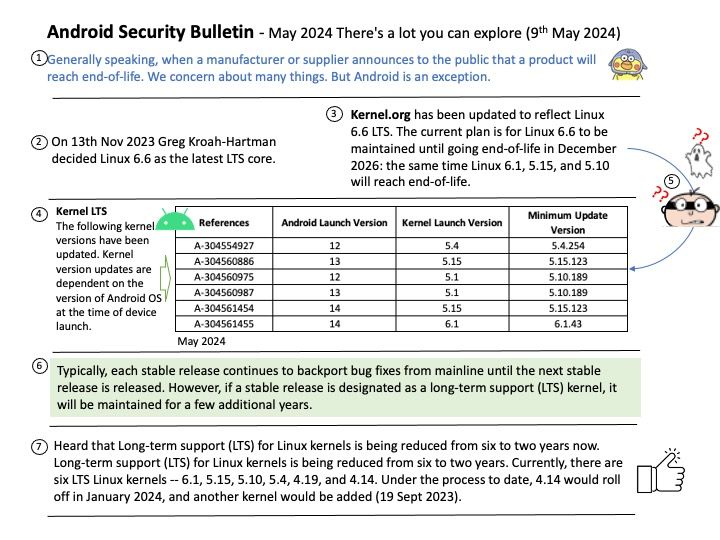
But in any event Greg Kroah-Hartman has decided to go ahead and declare Linux 6.6 as the newest LTS kernel. Kernel.org has been updated to reflect Linux 6.6 LTS. The current plan is for Linux 6.6 to be maintained until going end-of-life in December 2026: the same time Linux 6.1, 5.15, and 5.10 will reach end-of-life.
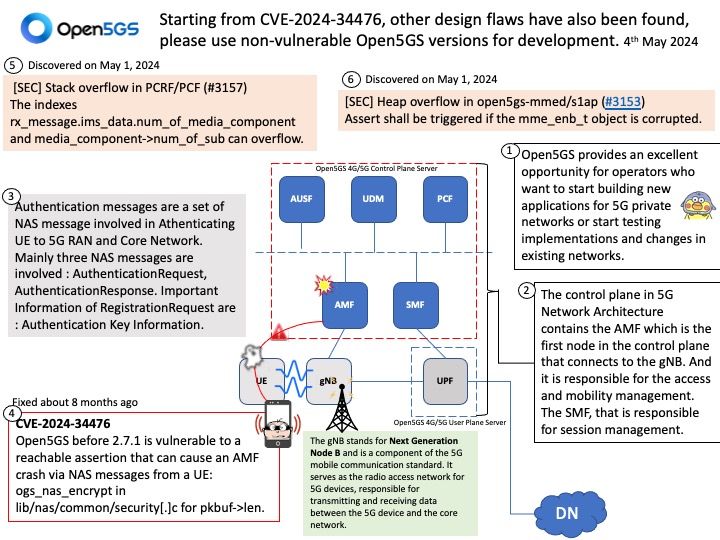
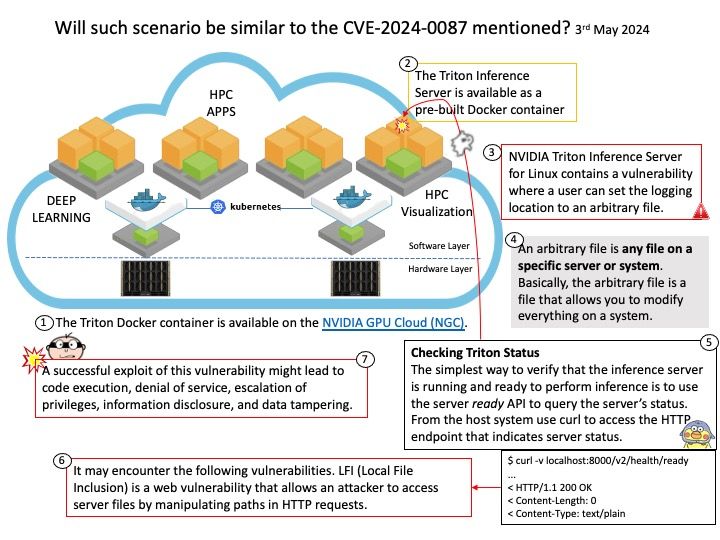
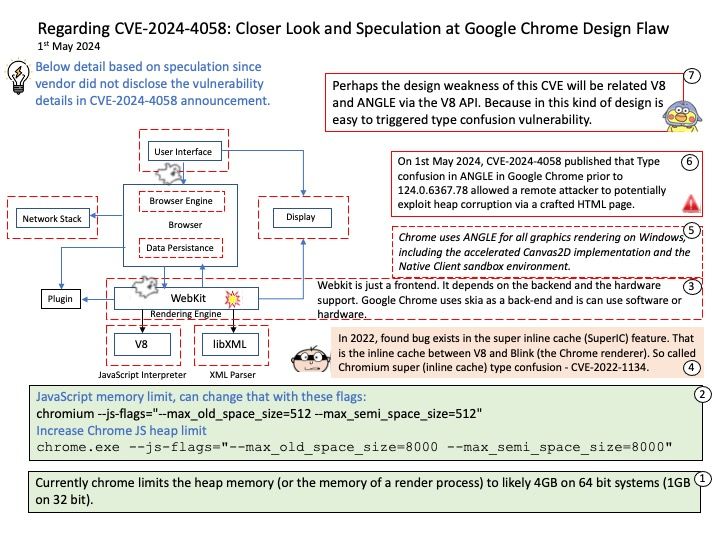
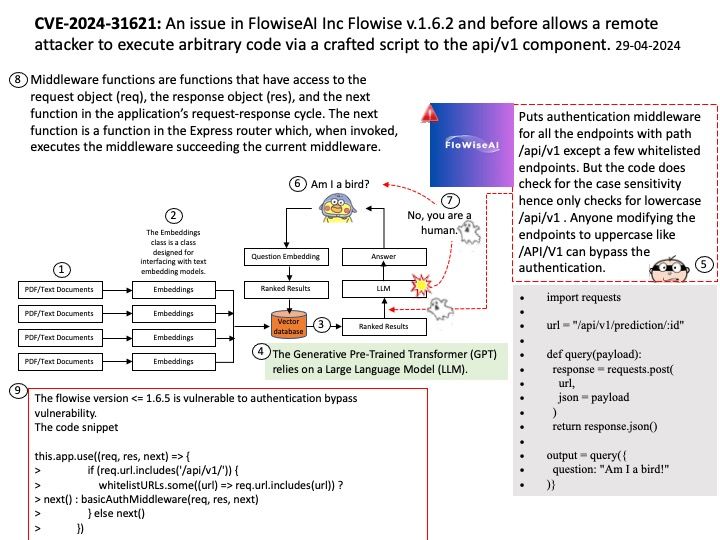
Android Security Bulletin—May 2024 (Published May 6, 2024)
The diagram above shows that kernel versions have been updated. Kernel version updates are dependent on the version of Android OS at the time of device launch. Please refer to the following link for details:
https://source.android.com/docs/security/bulletin/2024-05-01