Preface: Race conditions are most commonly associated with computer science and programming. They occur when two computer program processes, or threads, attempt to access the same resource at the same time and cause problems in the system. Race conditions are considered a common issue for multithreaded applications.
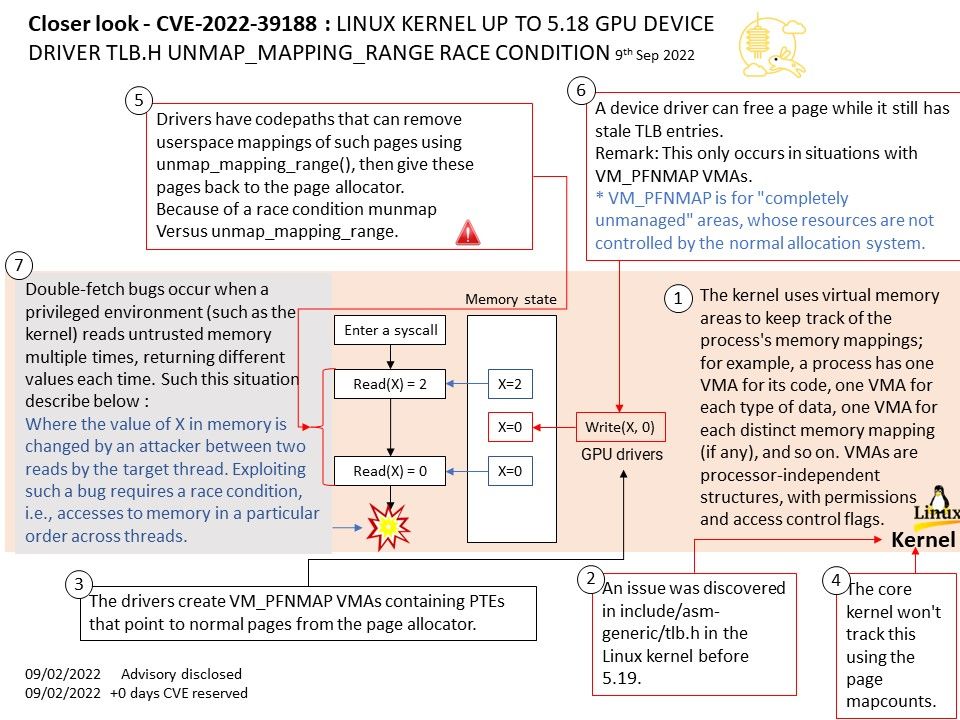
Background: The kernel uses virtual memory areas to keep track of the process’s memory mappings; for example, a process has one VMA for its code, one VMA for each type of data, one VMA for each distinct memory mapping (if any), and so on. VMAs are processor-independent structures, with permissions and access control flags.
Vulnerability details: An issue was discovered in include/asm-generic/tlb[.]h in the Linux kernel before 5.19. Because of a race condition (unmap_mapping_range versus munmap), a device driver can free a page while it still has stale TLB entries. This only occurs in situations with VM_PFNMAP VMAs.
Summary found by Google project zero – There are drivers (in particular GPU drivers) that create VM_PFNMAP VMAs containing PTEs that point to normal pages from the page allocator. VM_PFNMAP means that the core kernel won’t track this using the page mapcounts.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2022-39188
.jpg)
.jpg)
.jpg)
.jpg)