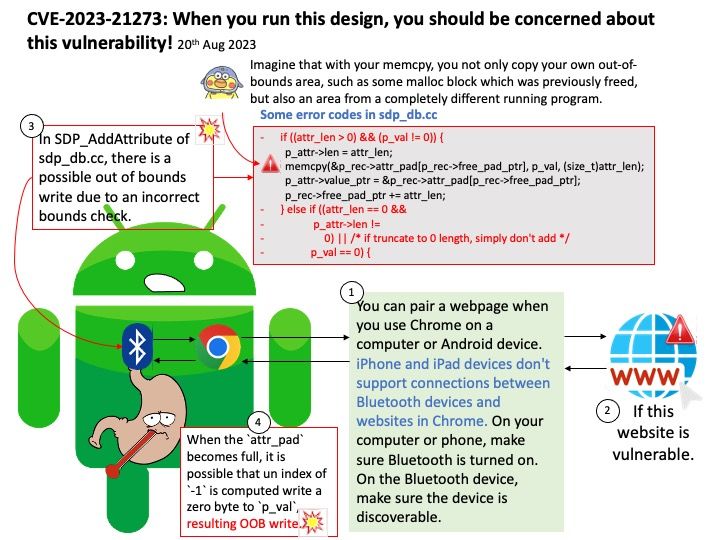
(1st Sep 2023)
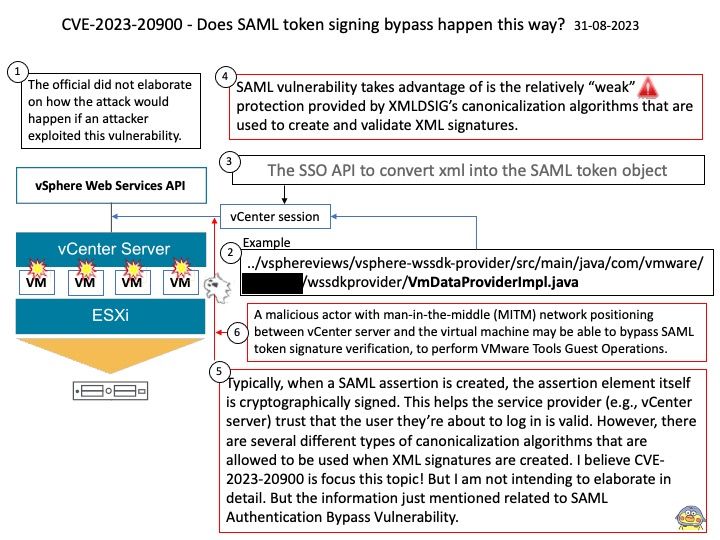
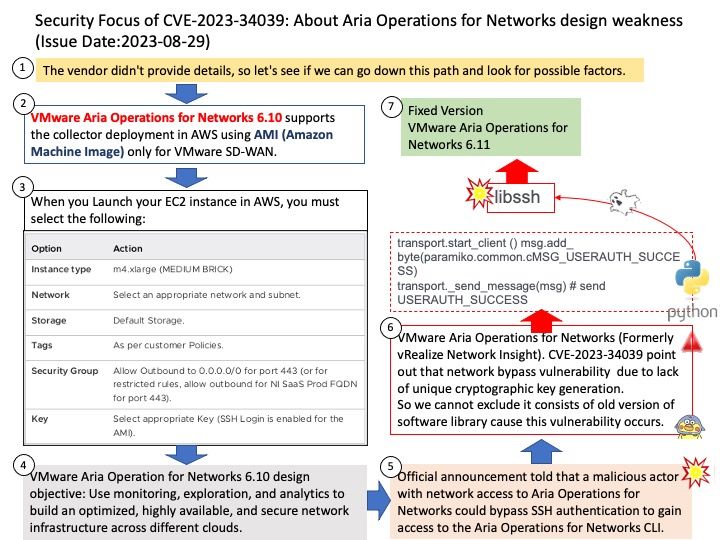
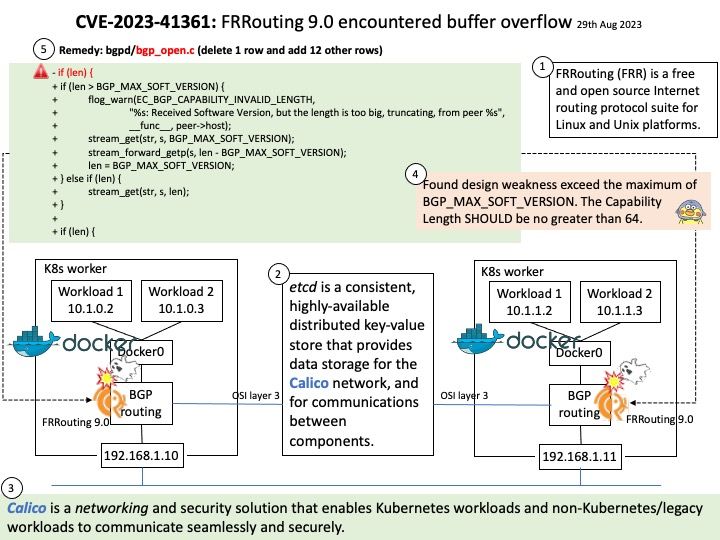
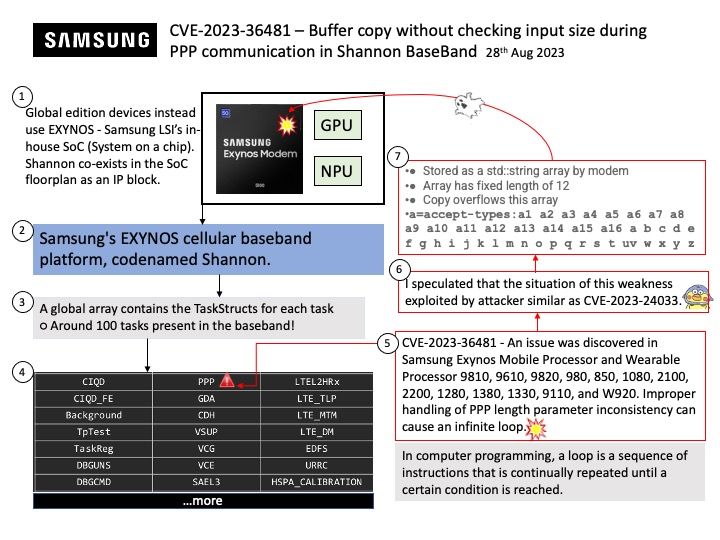
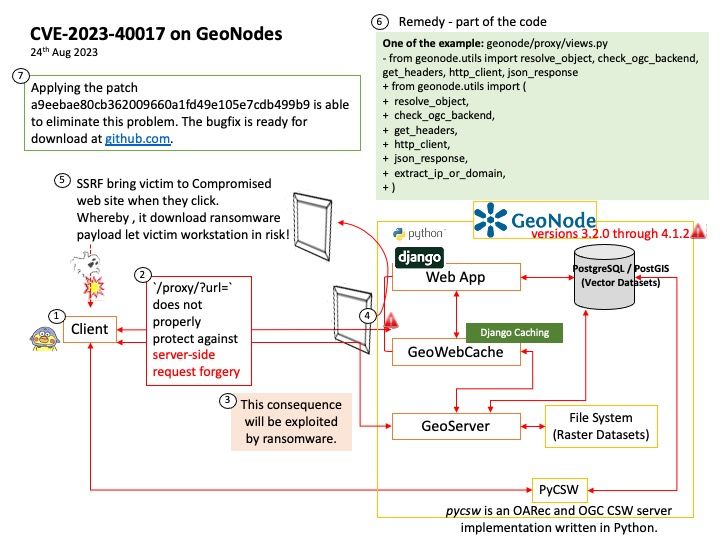
Preface: AI (Artificial intelligence) moves from big data normalization to learning to understand data, so called trained. It require large amount of computer processing resources.
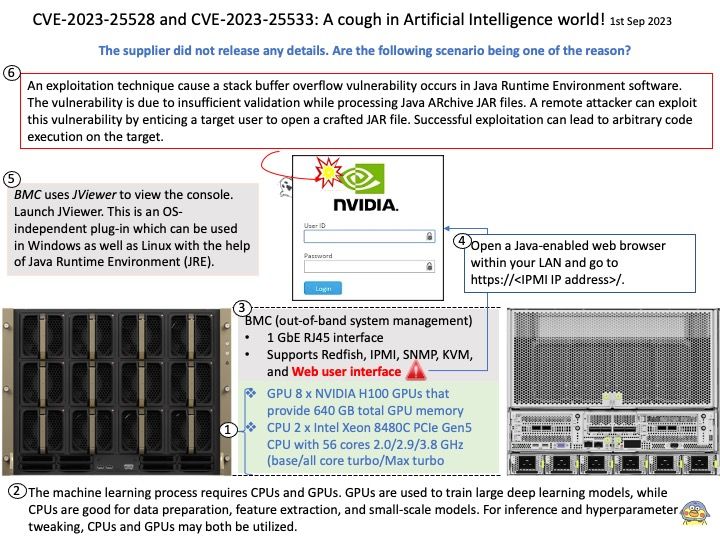
The machine learning process requires CPUs and GPUs. GPUs are used to train large deep learning models, while CPUs are good for data preparation, feature extraction, and small-scale models. For inference and hyperparameter tweaking, CPUs and GPUs may both be utilized.
Background: The NVIDIA Hopper architecture will supersede the already powerful NVIDIA Ampere architecture.
The NVIDIA DGX H100 System is the universal system purpose-built for all AI infrastructure and workloads, from analytics to training to inference. The system is built on eight NVIDIA H100 Tensor Core GPUs. If you want to run Java programs, but not develop them, download the Java Runtime Environment, or JRE.
BMC uses JViewer to view the console. Launch JViewer – This is an OS-independent plug-in which can be used in Windows as well as Linux with the help of Java Runtime Environment (JRE).
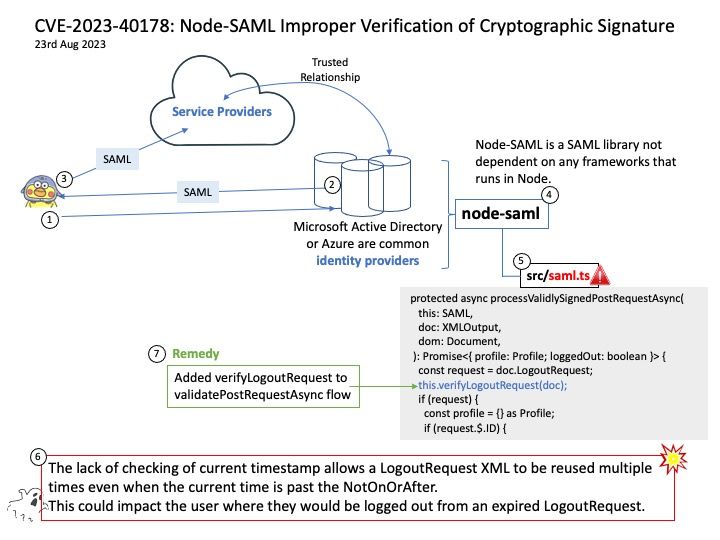
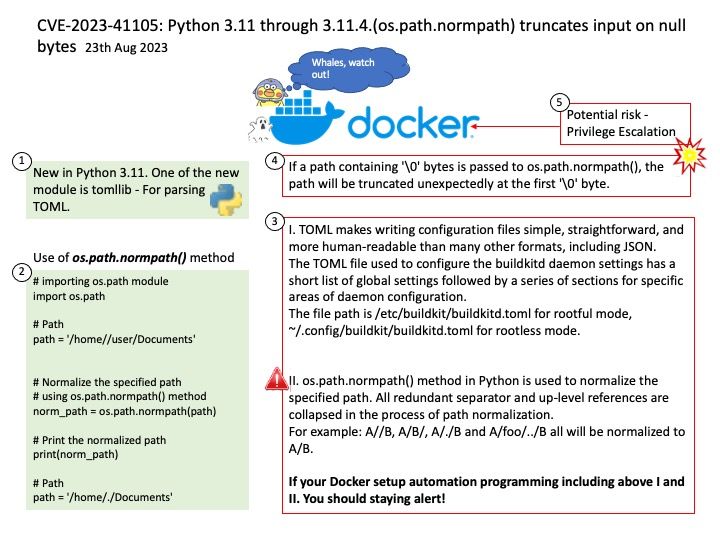
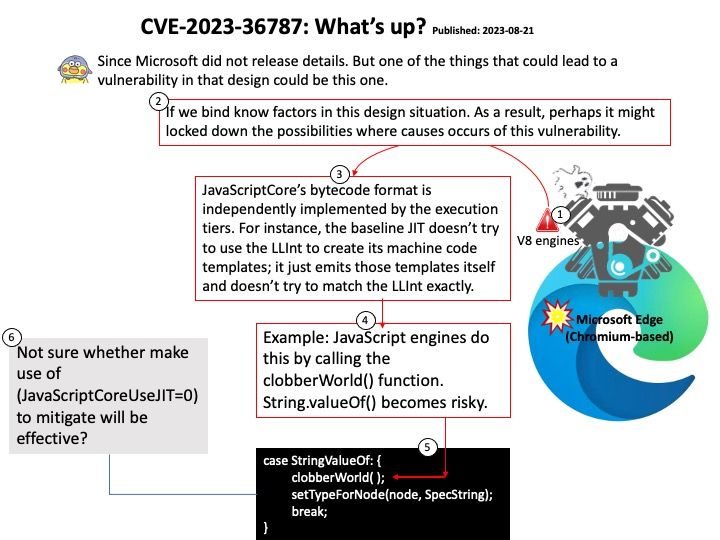
Vulnerability details:
CVE-2023-25528 – NVIDIA DGX H100 baseboard management controller (BMC) contains a vulnerability in a web server plugin, where an unauthenticated attacker may cause a stack overflow by sending a specially crafted network packet. A successful exploit of this vulnerability may lead to arbitrary code execution, denial of service, information disclosure, and data tampering.
CVE-2023-25533 – NVIDIA DGX H100 BMC contains a vulnerability in the web UI, where an attacker may cause improper input validation. A successful exploit of this vulnerability may lead to information disclosure, code execution, and escalation of privileges.
Official announcement: For details, please refer to the link – https://nvidia.custhelp.com/app/answers/detail/a_id/5473