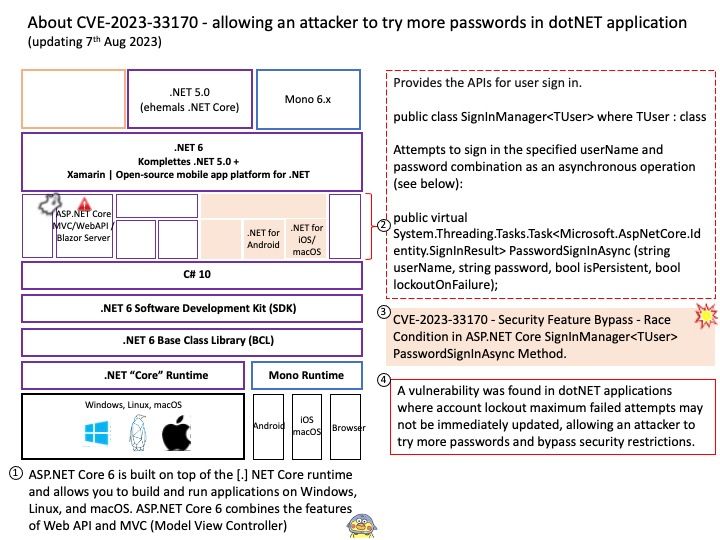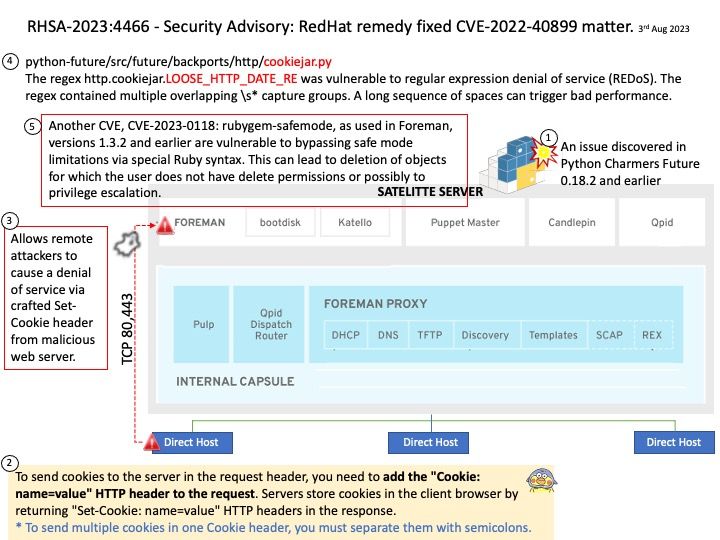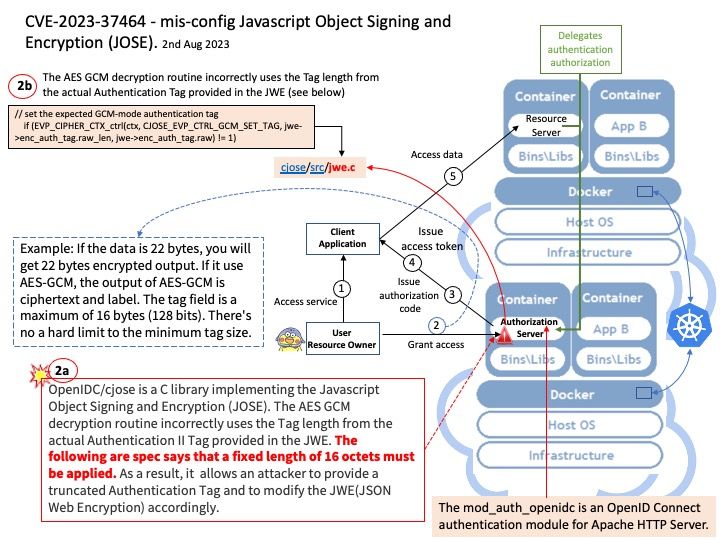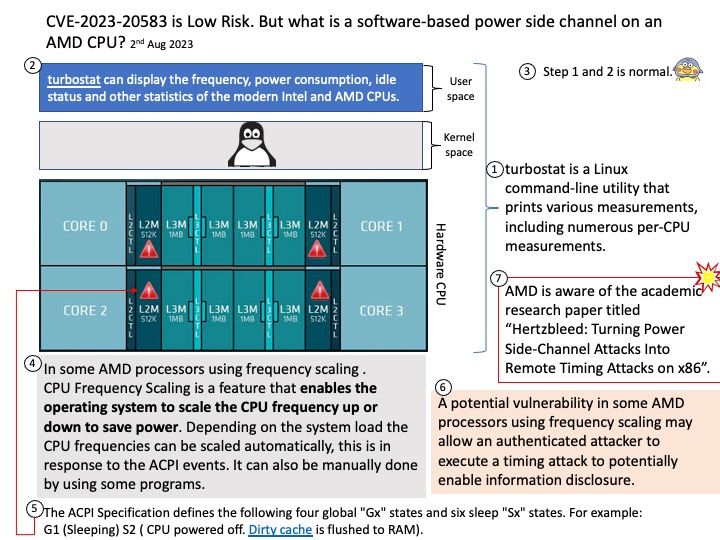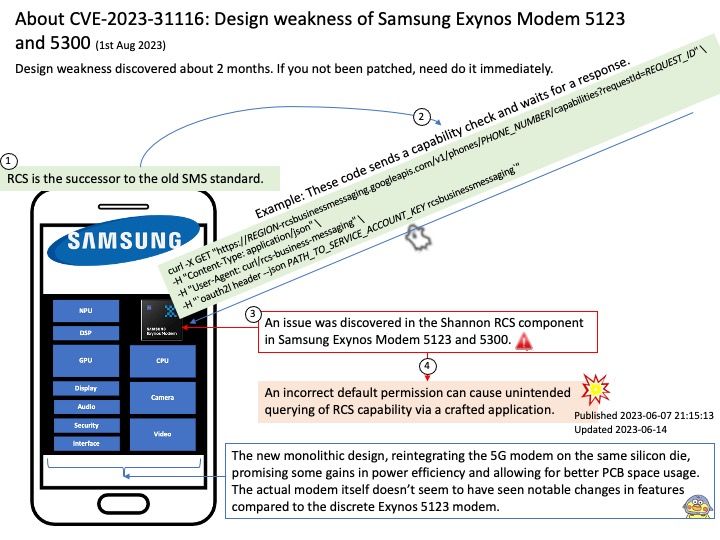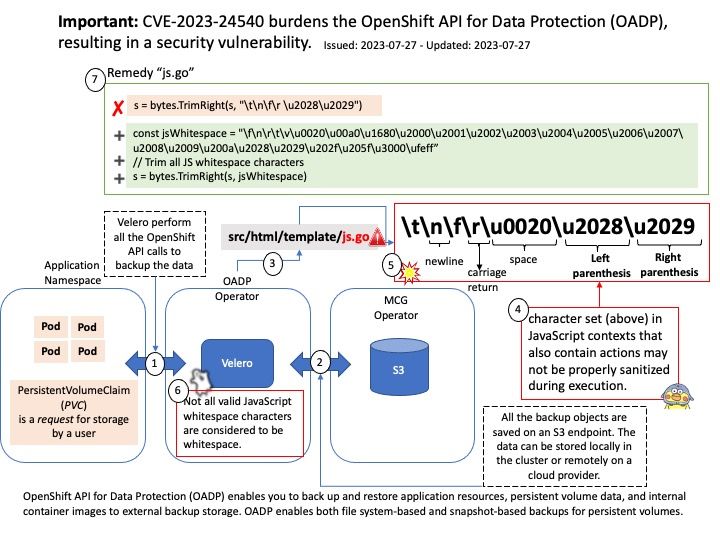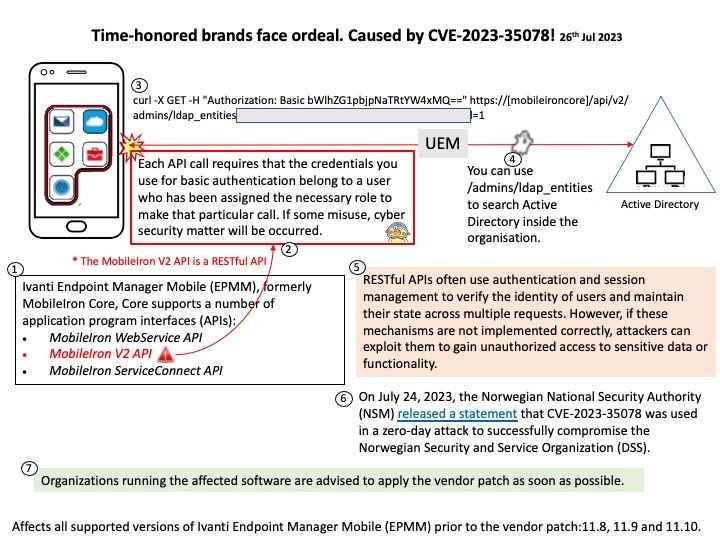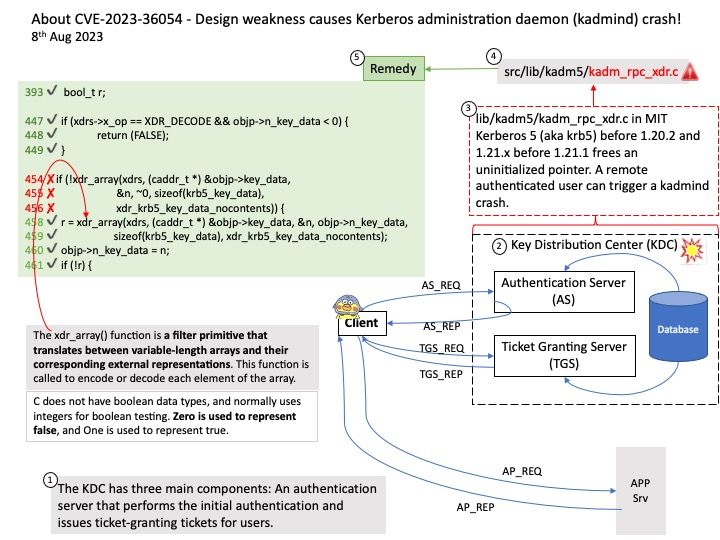
Preface: Kerberos runs as a third-party trusted server known as the Key Distribution Center (KDC). Each user and service on the network is a principal. The KDC has three main components: An authentication server that performs the initial authentication and issues ticket-granting tickets for users.
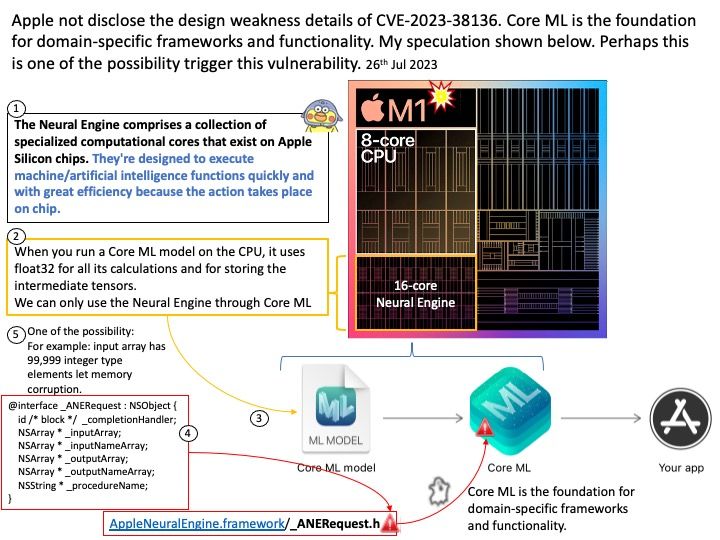
Background: Kerberos implementations also exist for other operating systems such as Apple OS, FreeBSD, UNIX, and Linux.
Ref: The patch adds Privileged Attribute Certificate (PAC) signatures to the Kerberos PAC buffer. A PAC is an extension to a Kerberos ticket that contains information about a user’s privileges.
What are the changes in Kerberos October 2023?
October 10, 2023 – Full Enforcement phase
Removes support for the registry subkey KrbtgtFullPacSignature. Removes support for Audit mode. All service tickets without the new PAC signatures will be denied authentication.
Vulnerability details: lib/kadm5/kadm_rpc_xdr[.]c in MIT Kerberos 5 (aka krb5) before 1.20.2 and 1.21.x before 1.21.1 frees an uninitialized pointer. A remote authenticated user can trigger a kadmind crash. This occurs because _xdr_kadm5_principal_ent_rec does not validate the relationship between n_key_data and the key_data array count.
Official announcement: For details, please refer to link – https://nvd.nist.gov/vuln/detail/CVE-2023-36054