Preface: It is popular like Java, Python applications can run on all operating systems (Windows, Unix, Linux, Mac).
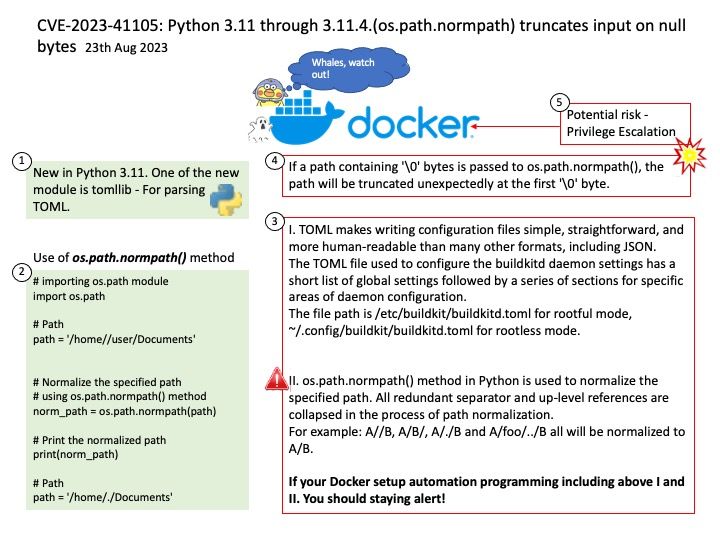
Background: What’s New in Python 3.11. One of the new module is tomllib – For parsing TOML.
I. TOML makes writing configuration files simple, straightforward, and more human-readable than many other formats, including JSON.
The TOML file used to configure the buildkitd daemon settings has a short list of global settings followed by a series of sections for specific areas of daemon configuration.
The file path is /etc/buildkit/buildkitd.toml for rootful mode, ~/.config/buildkit/buildkitd.toml for rootless mode.
II. os[.]path[.]normpath() method in Python is used to normalize the specified path. All redundant separator and up-level references are collapsed in the process of path normalization.
For example: A//B, A/B/, A/./B and A/foo/../B all will be normalized to A/B.
If your Docker setup automation programming including above I and II. You should staying alert.
Vulnerability details:
'\0' means NULL. If a path containing ‘\0’ bytes is passed to os.path.normpath(), the path will be truncated unexpectedly at the first ‘\0’ byte.
In some cases, in which an application would have rejected a filename for security reasons in Python 3.10.x or earlier, but that filename is no longer rejected in Python 3.11 through 3.11.4.
08/23/2023 disclosed
Official announcement: For details, please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2023-41105