Preface: Now that said, SSO reduces the number of attack surfaces because users only log in once each day and only use one set of credentials. Reducing login to one set of credentials improves enterprise security. Or are there other concerns?
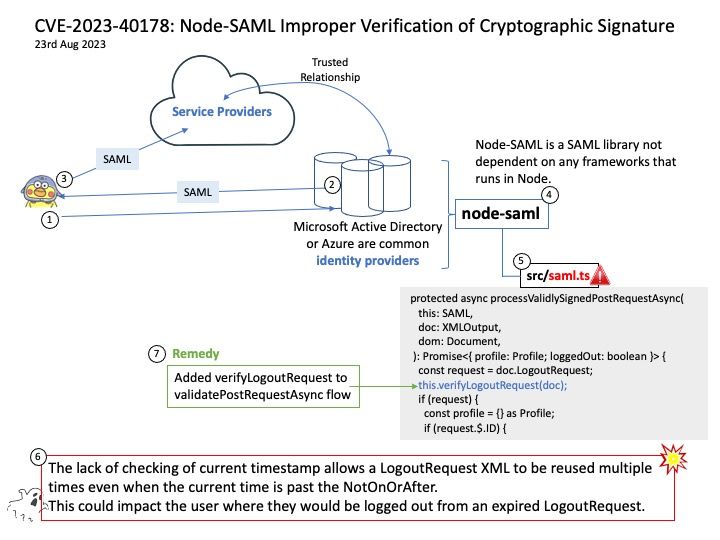
Background: Node-SAML has built in support for SLO including. Signature validation. IdP initiated and SP initiated logouts. Decryption of encrypted name identifiers in IdP initiated logout. Redirect and POST SAML Protocol Bindings.
A SAML Service Provider (SP) is a system entity that receives and accepts authentication assertions in conjunction with a Single Sign-On (SSO) profile of the Security Assertion Markup Language (SAML). For example: Gmail, Salesforce,…etc
An identity provider performs the authentication that the end user is who they say they are and sends that data to the service provider along with the user’s access rights for the service. Microsoft Active Directory or Azure are common identity providers. Salesforce and other CRM solutions are usually service providers, in that they depend on an identity provider for user authentication.
Vulnerability details: Node-SAML is a SAML library not dependent on any frameworks that runs in Node. The lack of checking of current timestamp allows a LogoutRequest XML to be reused multiple times even when the current time is past the NotOnOrAfter. This could impact the user where they would be logged out from an expired LogoutRequest. In bigger contexts, if LogoutRequests are sent out in mass to different SPs, this could impact many users on a large scale.
Remedy: This issue was patched in version 4.0.5.
Official announcement: For details, please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2023-40178