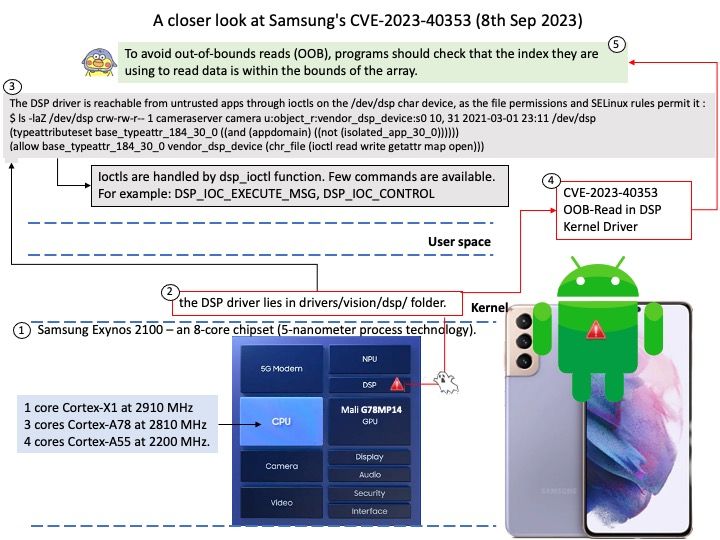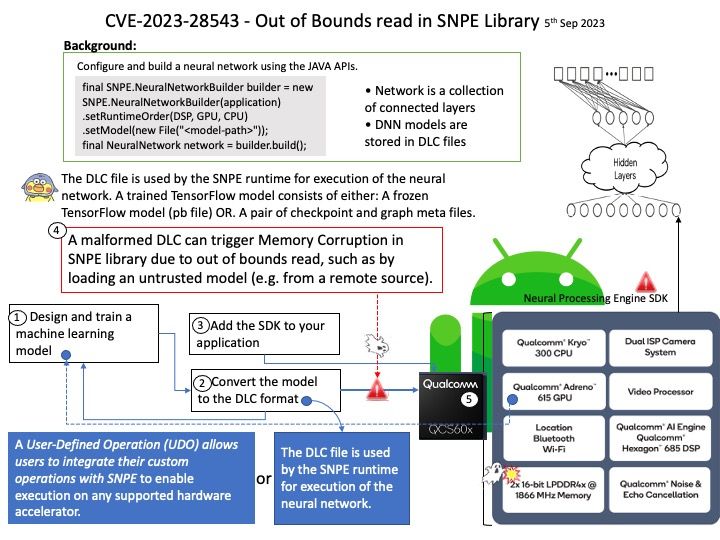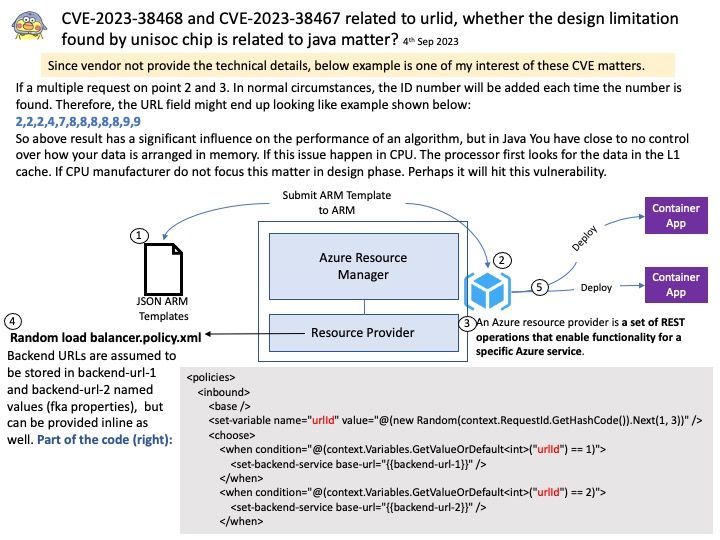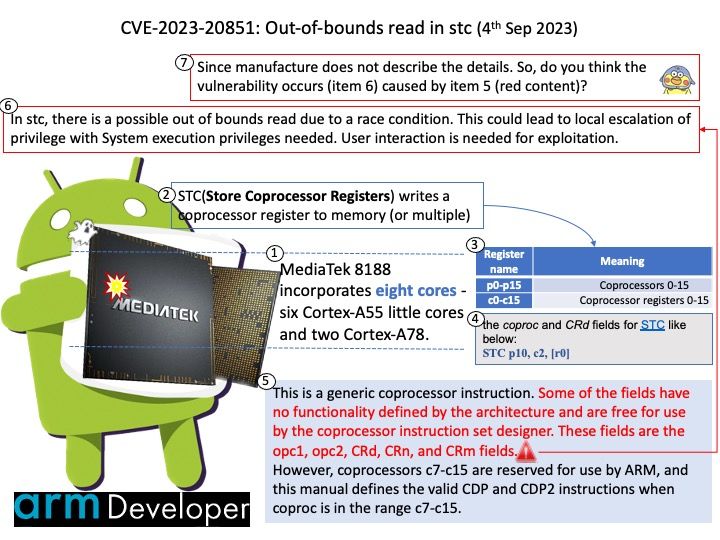
Preface: When technology world relies on cloud computing. Meanwhile fast switching includes high speed backbone will be counted. The technology shift physical network device go to virtual computing platform. That said, the traditional design goal one software installs to one hardware unit. For instance, a single operating system install on one hardware device has been change. The actual example are Cumulus Linux and Cisco IOS. Both are major players in cloud computing network switching technology.
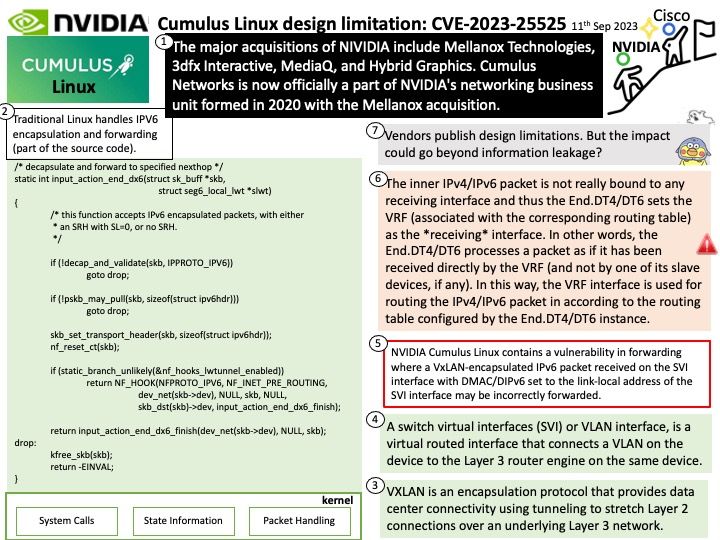
Background: VXLAN is an encapsulation protocol that provides data center connectivity using tunneling to stretch Layer 2 connections over an underlying Layer 3 network. The VXLAN encapsulation mechanism encapsulates the IPv6 packets in the overlay as IPv4 UDP packets and uses IPv4 routing to transport the VXLAN encapsulated traffic. A switch virtual interfaces (SVI) or VLAN interface, is a virtual routed interface that connects a VLAN on the device to the Layer 3 router engine on the same device.
Remark: Virtual routing and forwarding (VRF) is an IP-based computer network technology that enables the simultaneous co-existence of multiple virtual routers (VRs) as instances or virtual router instances (VRIs) within the same router.
Vulnerability details: NVIDIA Cumulus Linux contains a vulnerability in forwarding where a VxLAN-encapsulated IPv6 packet received on the SVI interface with DMAC/DIPv6 set to the link-local address of the SVI interface may be incorrectly forwarded. A successful exploit may lead to information disclosure.
My observation: The inner IPv4/IPv6 packet is not really bound to any receiving interface and thus the End.DT4/DT6 sets the VRF (associated with the corresponding routing table) as the *receiving* interface. In other words, the End.DT4/DT6 processes a packet as if it has been received directly by the VRF (and not by one of its slave devices, if any). In this way, the VRF interface is used for routing the IPv4/IPv6 packet in according to the routing table configured by the End.DT4/DT6 instance.
*Vendors publish design limitations. But the impact could go beyond information leakage?
Official announcement: For details, please refer to the link – https://nvidia.custhelp.com/app/answers/detail/a_id/5480