Background: Magento is an e-commerce platform written in PHP atop the zend-framework, available under both open-source and commercial licenses. It is written in an advanced object-oriented idiom that uses the MVC pattern and XML configuration files, aiming for flexibility and extensibility.
Vulnerabilities announced this week – Hints
Vendor have the right to remain vulnerability details and not disclose to public. And therefore we only obtain below information.
PHP Object Injection – Arbitrary code execution (Critical) – CVE-2020-9663
Stores cross-site scripting – Sensitive information disclosure (Important) – CVE-2020-9665
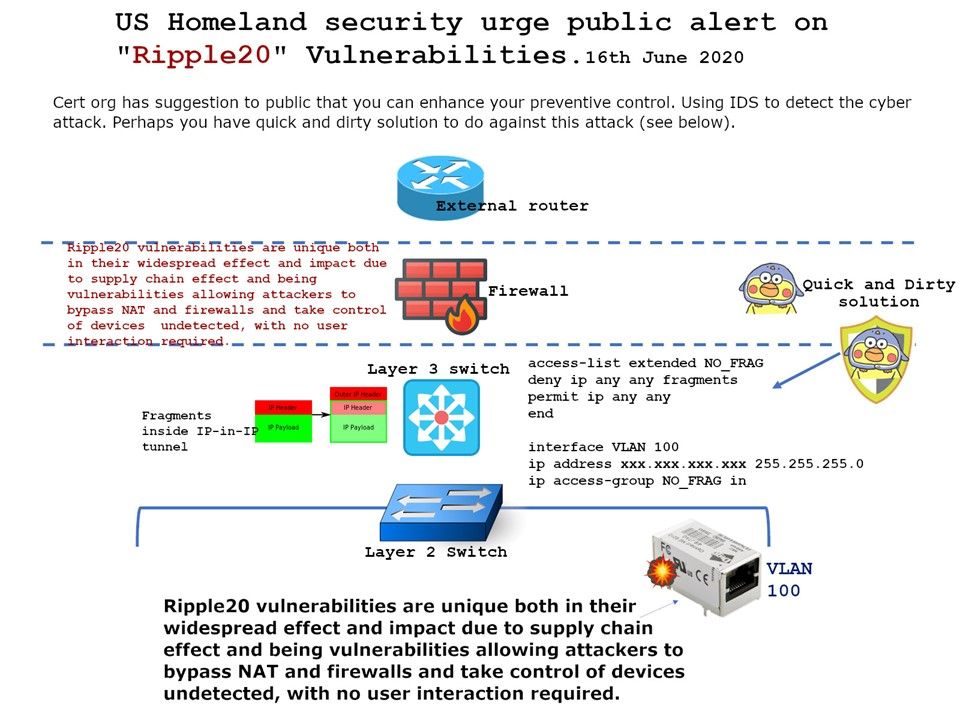
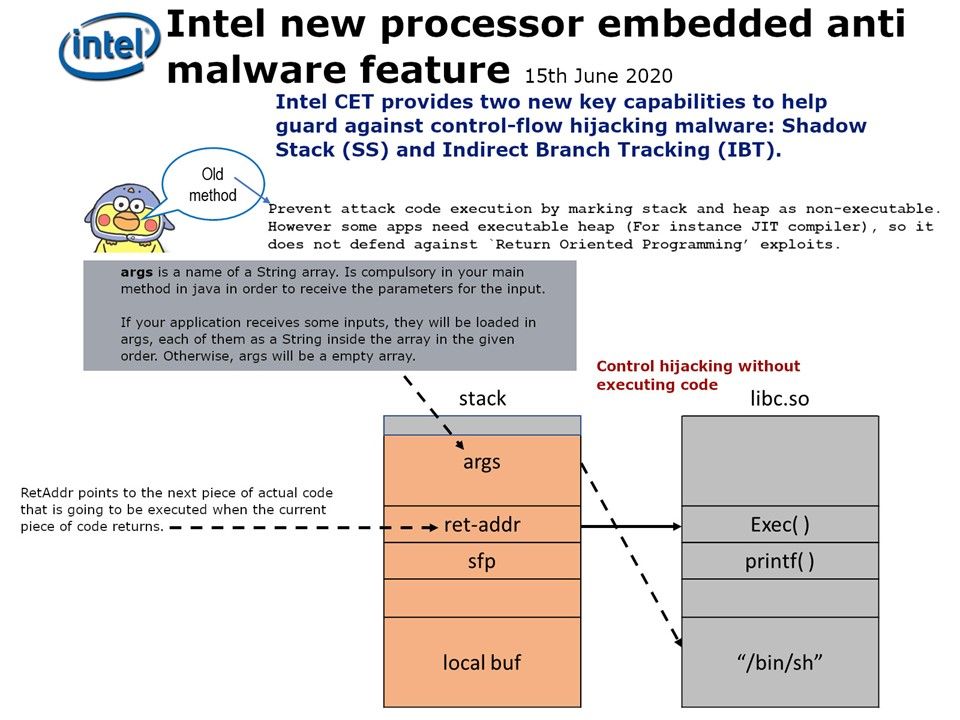
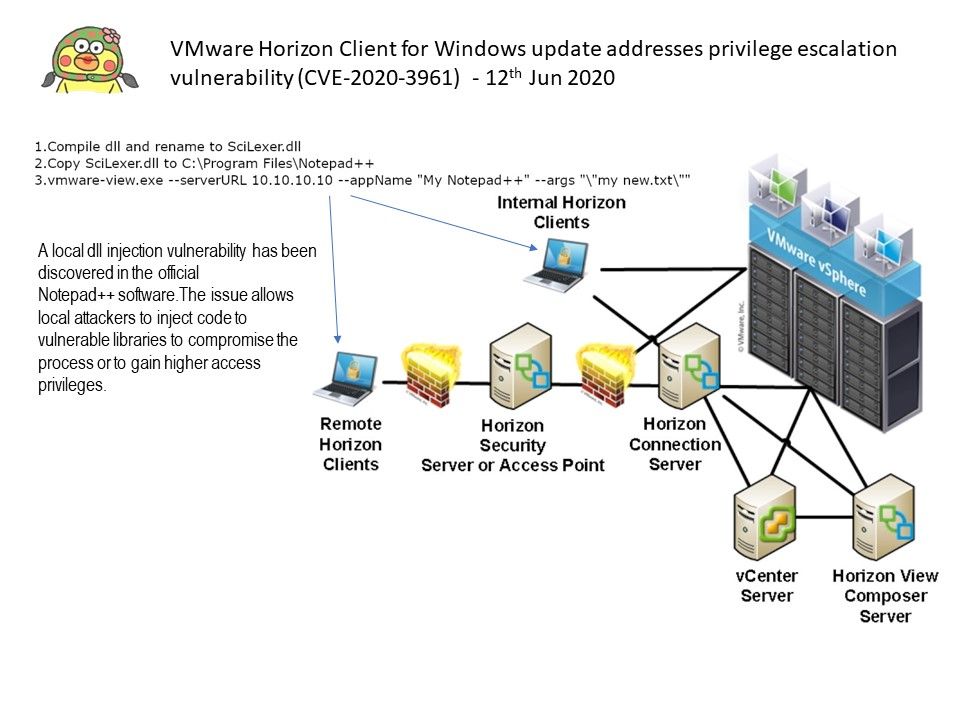
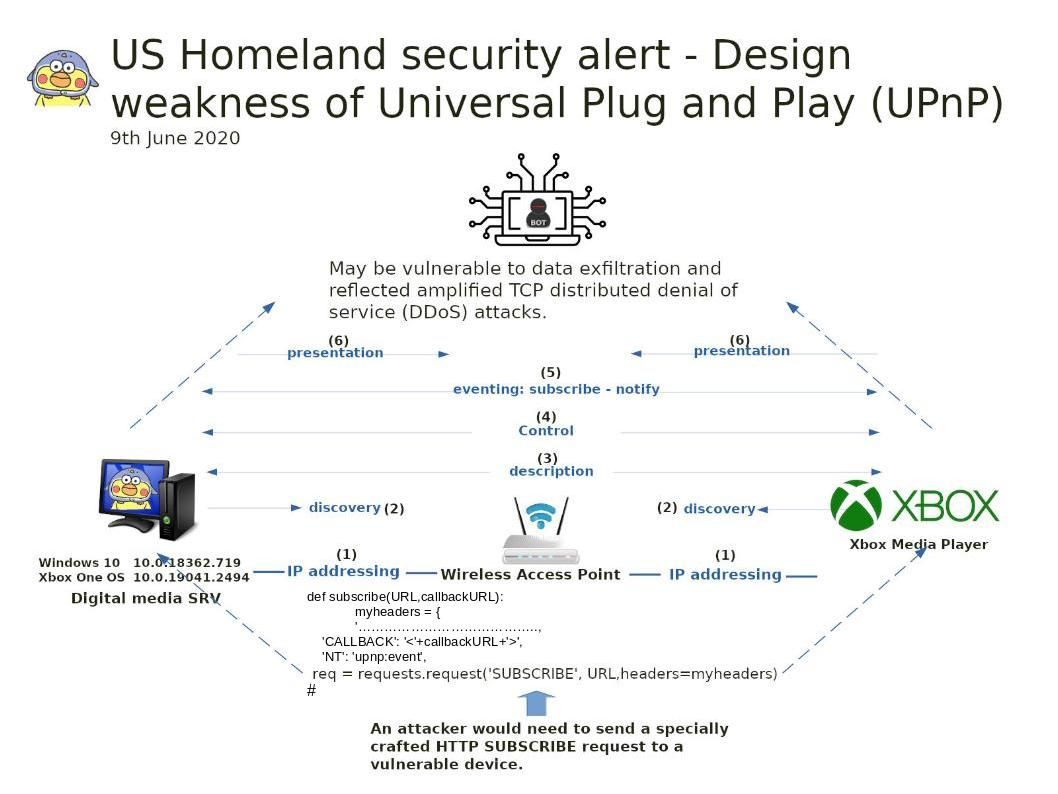
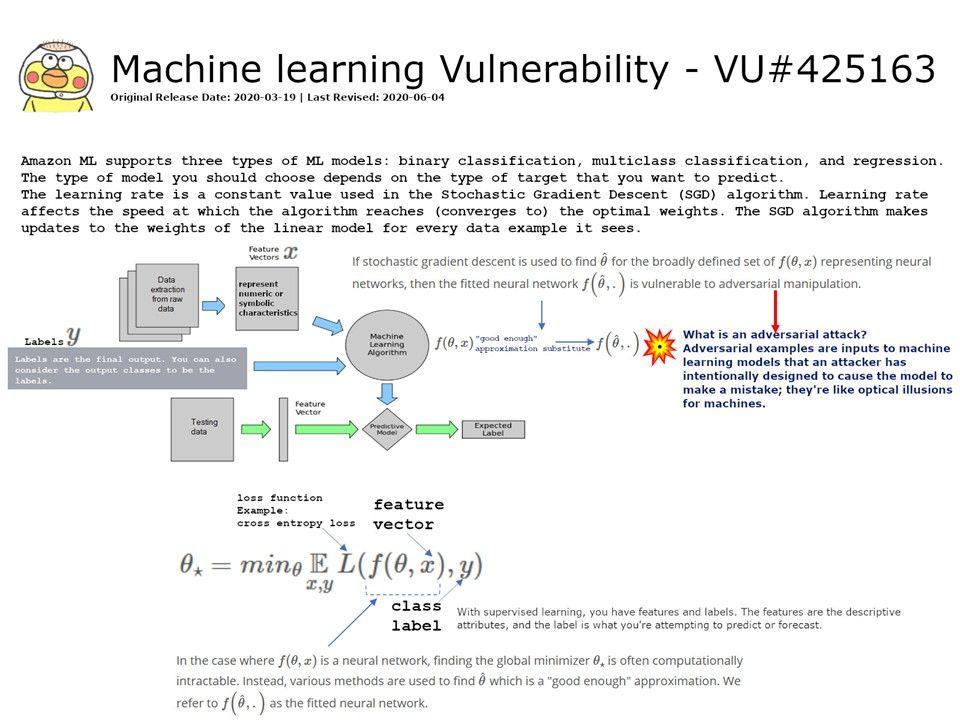
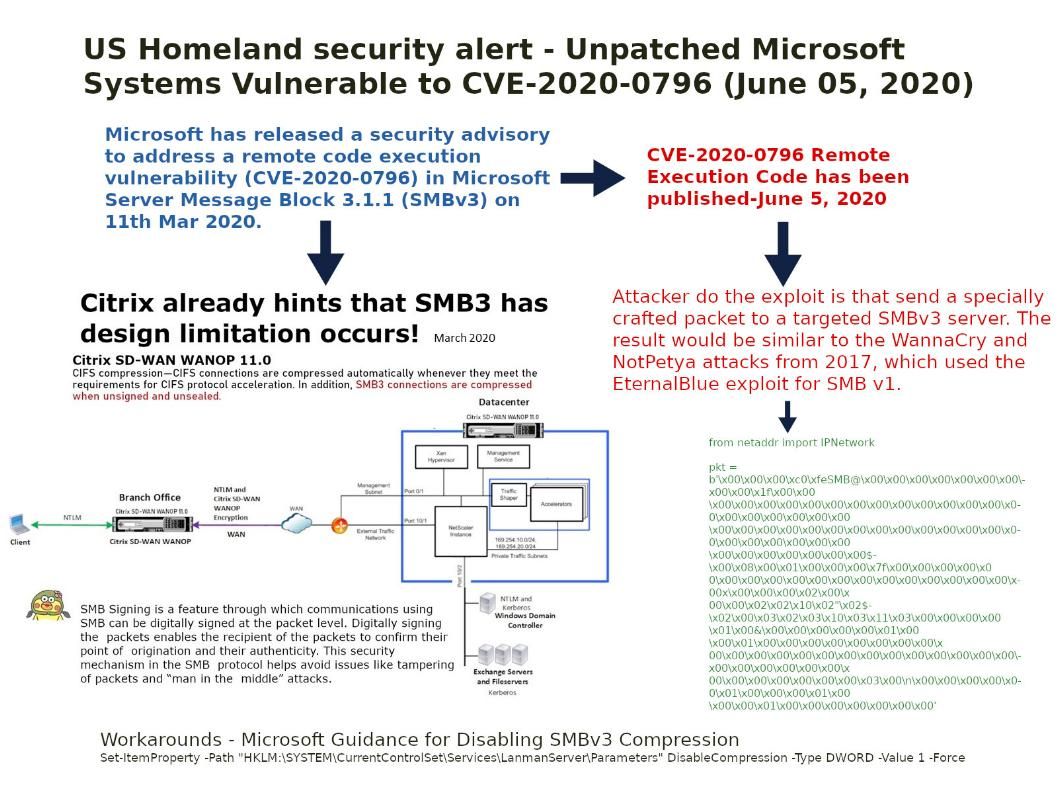
Please refer to attached diagram. Perhaps it will let you find out the root causes.
Official announcement: https://helpx.adobe.com/security/products/magento/apsb20-41.html
.jpg)