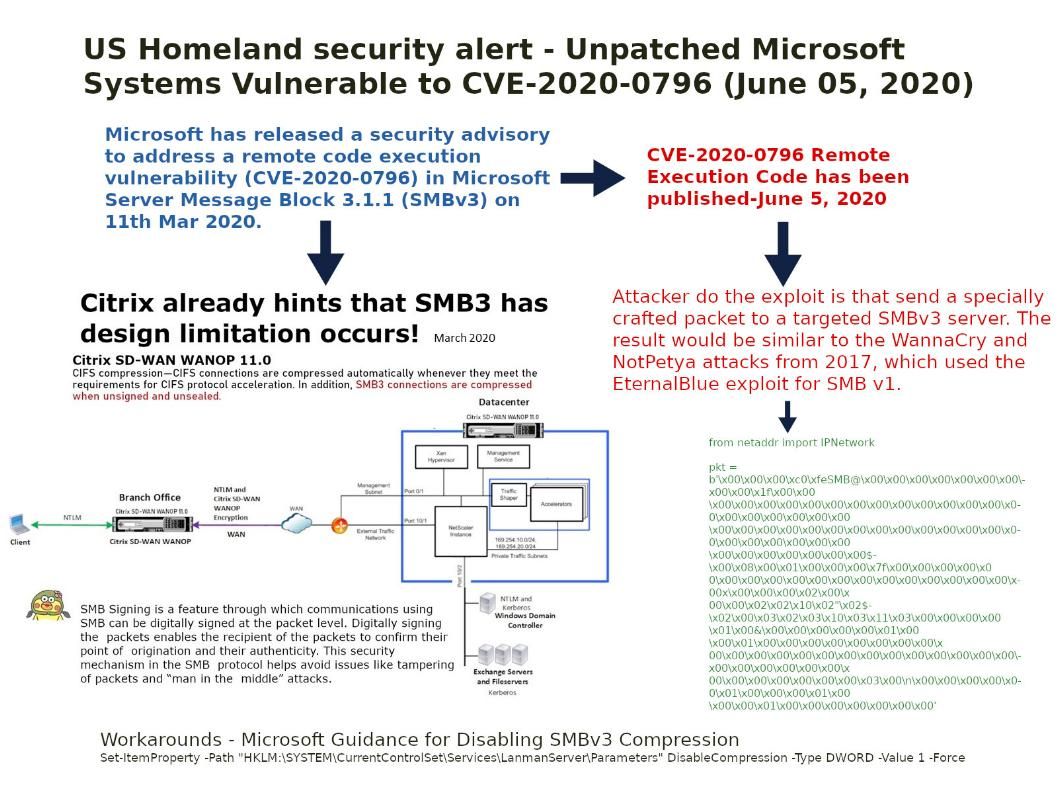
Preface: Microsoft has released a security advisory to address a remote code execution vulnerability (CVE-2020-0796) in Microsoft Server Message Block 3.1.1 (SMBv3) on 11th Mar 2020.
Synopsis: The proof of concept code vulnerability has been made public. Attacker do the exploit is that send a specially crafted packet to a targeted SMBv3 server. (refer to attached diagram). The result would be similar to the WannaCry and NotPetya attacks from 2017, which used the EternalBlue exploit for SMB v1.
Workarounds: Disabling SMBv3 Compression – refer to attached diagram. The solution display in the bottom .
Remedy solution by Microsoft – https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/adv200005
CISA urge to public – Although Microsoft disclosed and provided updates for this vulnerability in March 2020, malicious cyber actors are targeting unpatched systems with the new PoC, according to recent open-source reports. CISA strongly recommends using a firewall to block SMB ports from the internet and to apply patches to critical- and high-severity vulnerabilities as soon as possible.