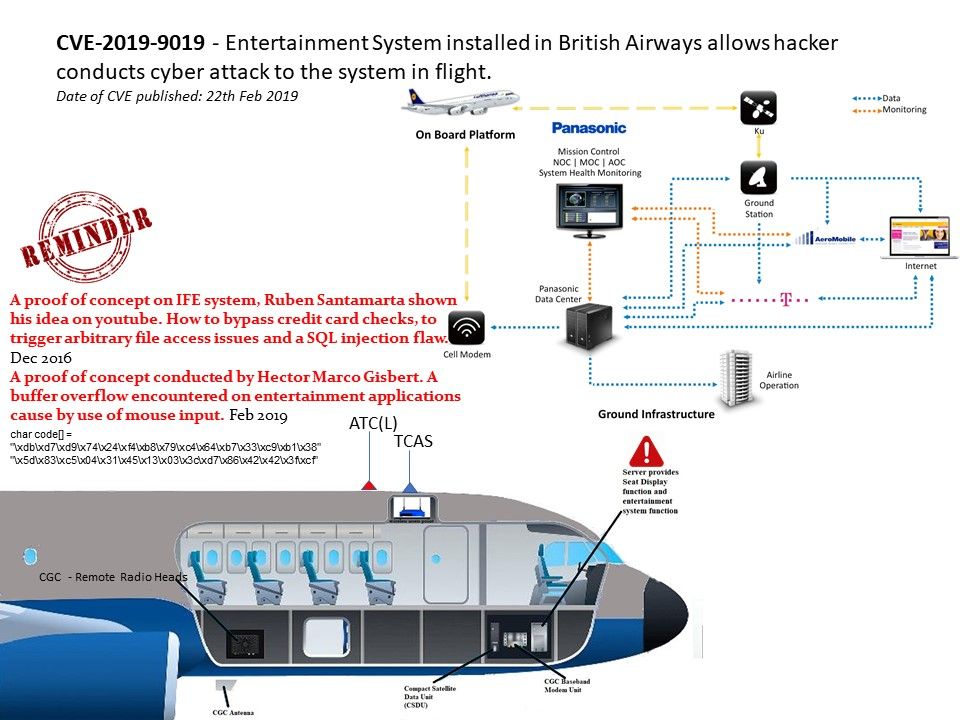
Preface: Linux-based airline seat-back entertainment system won the market since 2007.
Background: Seat back entertainment system including Wi-Fi, movies and television shows, games and music. Some of it is built into an airline’s fleet, and some have options where you can bring your own devices and access in-flight entertainment options.
Vulnerability details:
A buffer overflow vulnerability found in British Airways Entertainment System, as installed on Boeing 777-36N(ER) and possibly other aircraft. The system cannot not local attacker exploit USB charging/data-transfer feature conducting cyber attack.
Impact: Trigger a chat app Buffer overflow or other unknown impact.
Comment:
Panasonic IFE systems cover large scale of market. However the vulnerabilities found in past has similarity with existing one. The risks are given out from USB port. Since Panasonic product capabilities can provides advanced functions and features. So, we would urge vendor to hardening the cyber security of their products.
Headline News: https://cyware.com/news/cve-2019-9019-affects-british-airways-entertainment-system-on-boeing-777-36nersecurity-affairs-50cf43ec