Preface: Gobot is a framework for robotics, drones, and the Internet of Things (IoT), written in the Go programming language. The design goal of the decompression library is for embedded devices, because the flash memory capacity is limited and the processing speed is slow.
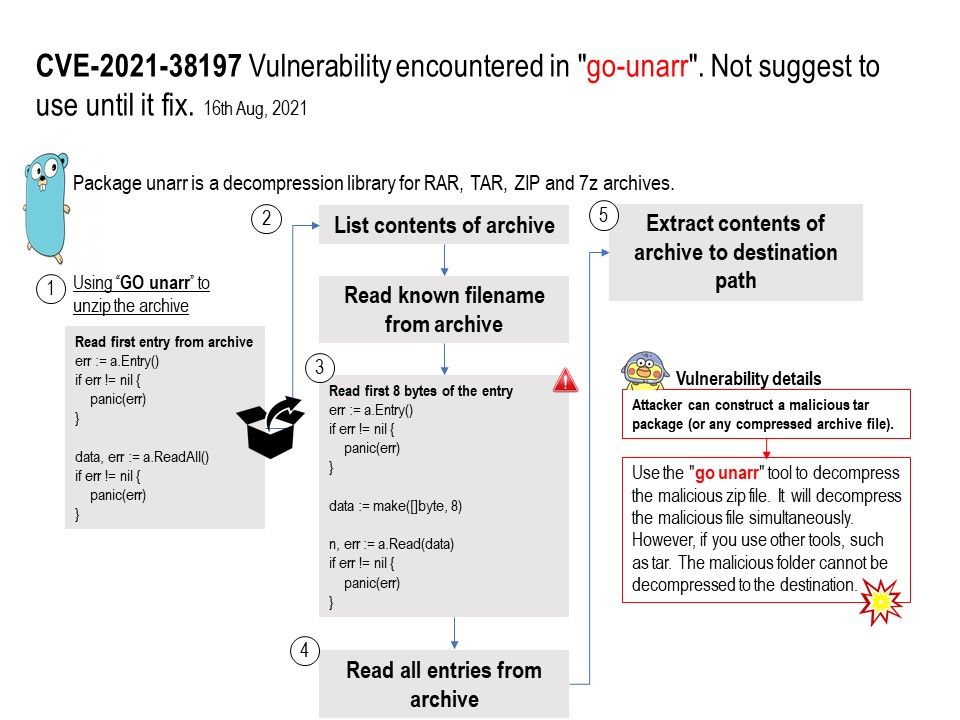
Background: Package unarr is a decompression library for RAR, TAR, ZIP and 7z archives.
Vulnerability details: Vulnerability occurred in unarr, which will lead to path traversal vulnerability. What is traversal attack? A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder.
Use the “go unarr” tool to decompress the malicious zip file. It will decompress the malicious file simultaneously. However, if you use other tools, such as tar. The malicious folder cannot be decompressed to the destination.By triggering the path traversal vulnerability, an attacker can store any file in any privileged place (which means that remote code execution can be caused under root privileges).
Workaround: No
Affected version: unarr 0.1.1
Remedy: Not yet announcement. Therefore not suggest to use until it fixed.