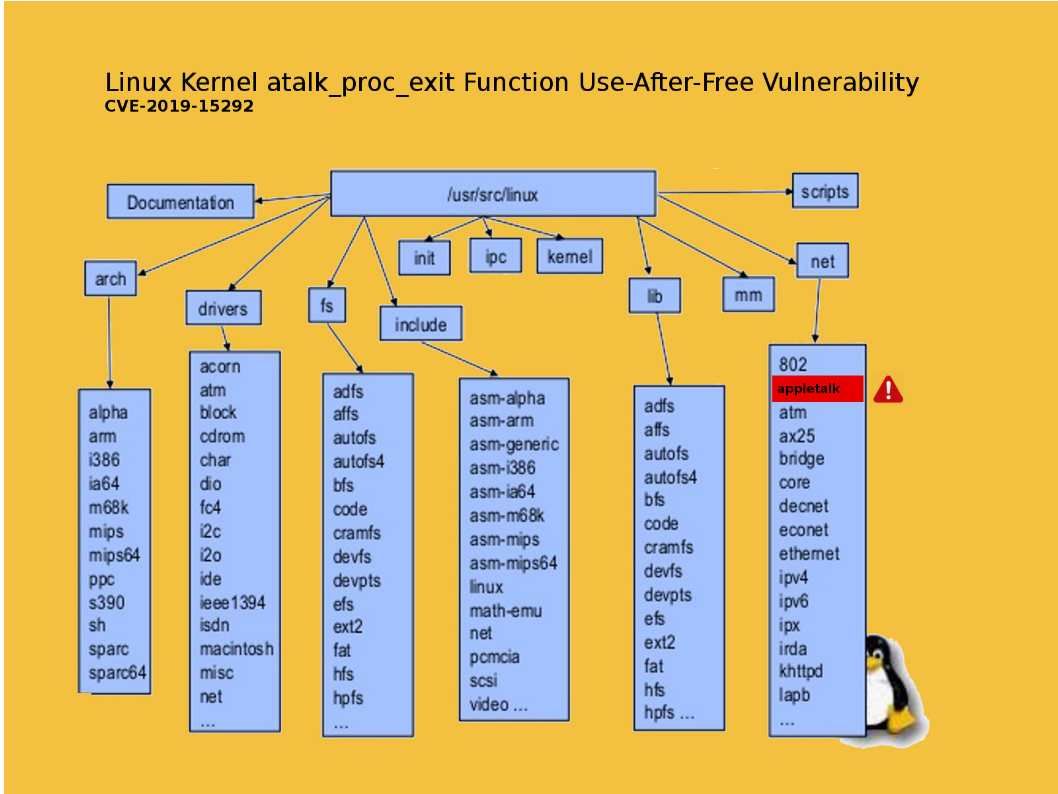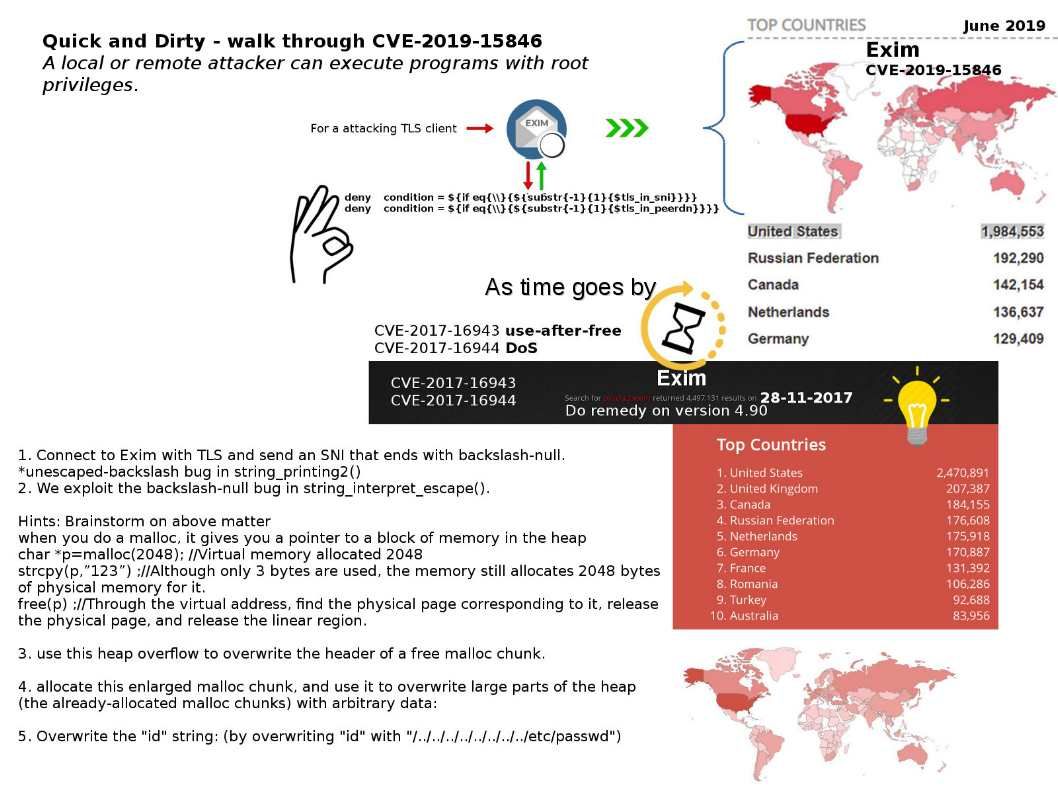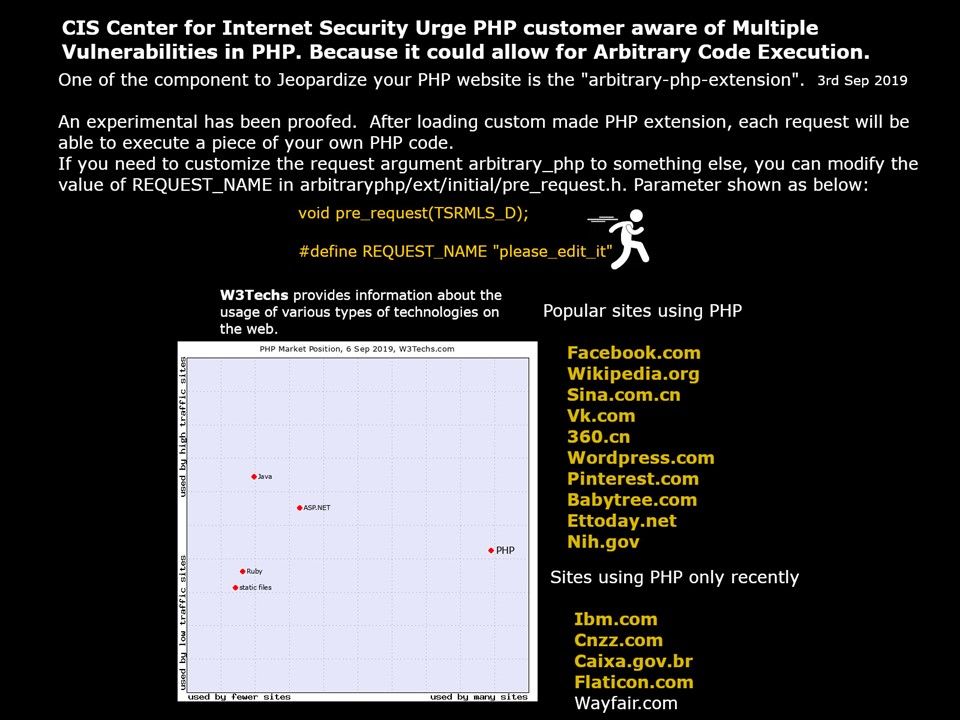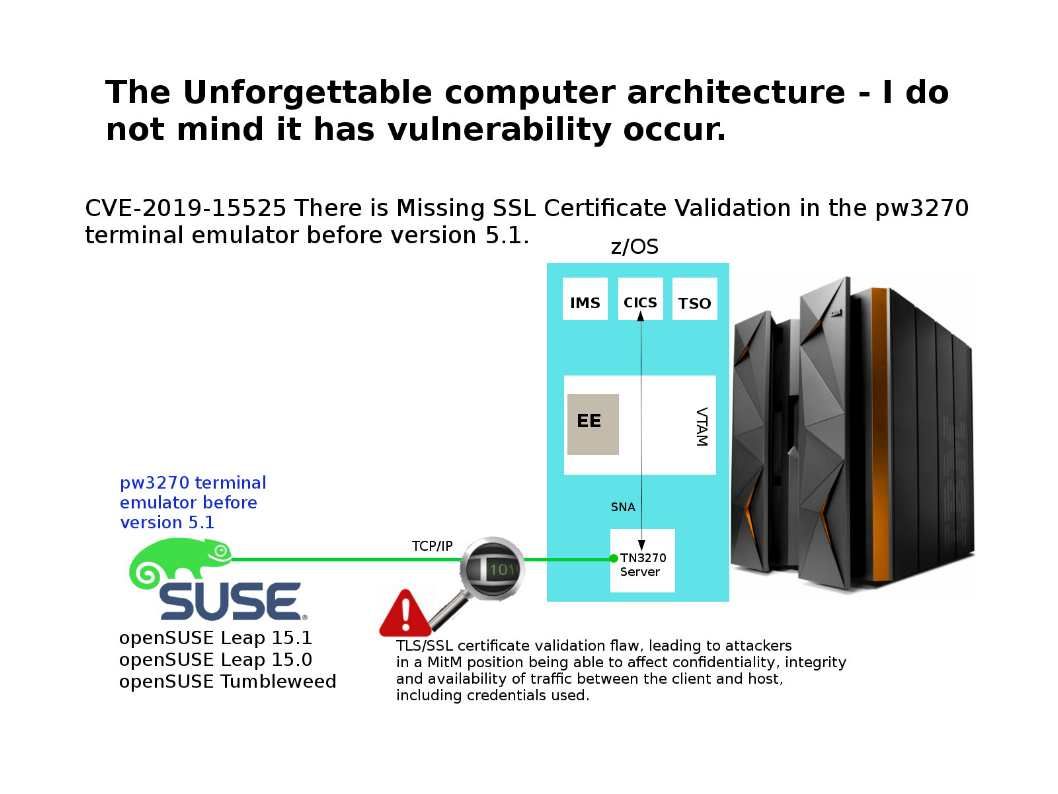
For healthcare, cyber attacks can have ramifications beyond financial loss and breach of privacy.
Preface: For healthcare, cyber attacks can have ramifications beyond financial loss and breach of privacy.
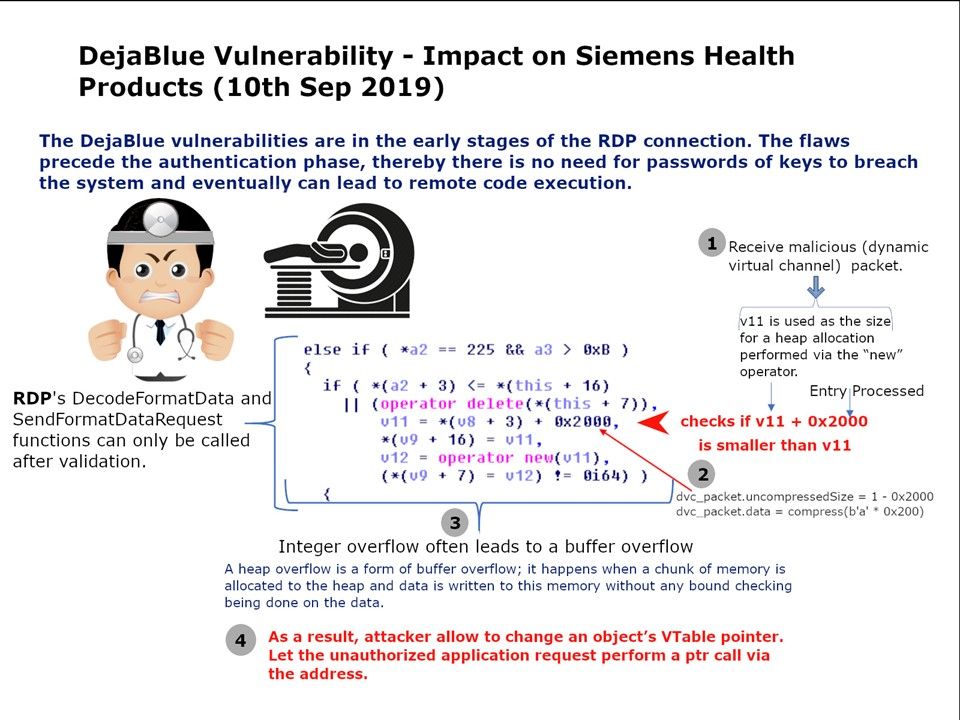
Background: The DejaBlue vulnerabilities are in the early stages of the RDP connection. The flaws precede the authentication phase, thereby there is no need for passwords of keys to breach the system and eventually can lead to remote code execution.
DejaBlue vulnerability trigger medical device manufacturer alert! People relies on doctor do the medical surgery to remediate their weakness of the health. But the medical industry itself also require cyber security doctor to remedy their product design weakness. It is fair. Siemens pioneer to introduce first computed tomography scanner in 70’s. In 1980 the first manufacturer to made the magnetic resonance imaging (MRI) scanner. As of today, their design has been intergarte with computing technology. And therefore the zero day and vulnerability happen in cyber world will become their pain!
Official announcement: SSA-187667: DejaBlue Vulnerabilities – Siemens Healthineers Products – https://cert-portal.siemens.com/productcert/pdf/ssa-187667.pdf