Preface: No matter “WAF” or a traditional Layer 3 firewall. The SSH service daemon will be installed because such service is not uncommon.
Vulnerability details: Memory corruption in PAN-OS 7.1.24 and earlier, PAN-OS 8.0.19 and earlier, PAN-OS 8.1.9 and earlier, and PAN-OS 9.0.3 and earlier will allow a remote, unauthenticated user to craft a message to Secure Shell Daemon (SSHD) and corrupt arbitrary memory.
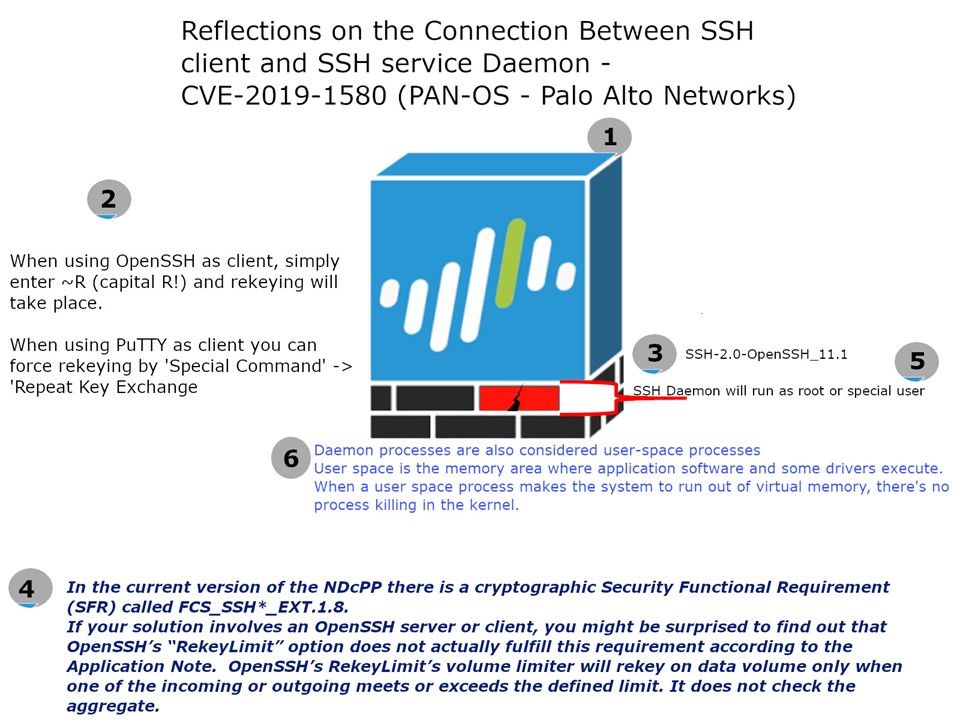
Additional:
In the current version of the NDcPP there is a cryptographic Security Functional Requirement (SFR) called FCS_SSH*_EXT.1.8.
If your solution involves an OpenSSH server or client, you might be surprised to find out that OpenSSH’s “RekeyLimit” option does not actually fulfill this requirement according to the Application Note. OpenSSH’s RekeyLimit’s volume limiter will rekey on data volume only when one of the incoming or outgoing meets or exceeds the defined limit. It does not check the aggregate.
From technical point of view, attacker is able to consume ssh service daemon memory resources. For instance when using OpenSSH as client, simply enter ~R (capital R!) and rekeying will take place. If they intend to increase the re-key times, the specify process will be in trouble!
Remedy: Only accept SSH connection with trust IP address and trust network.