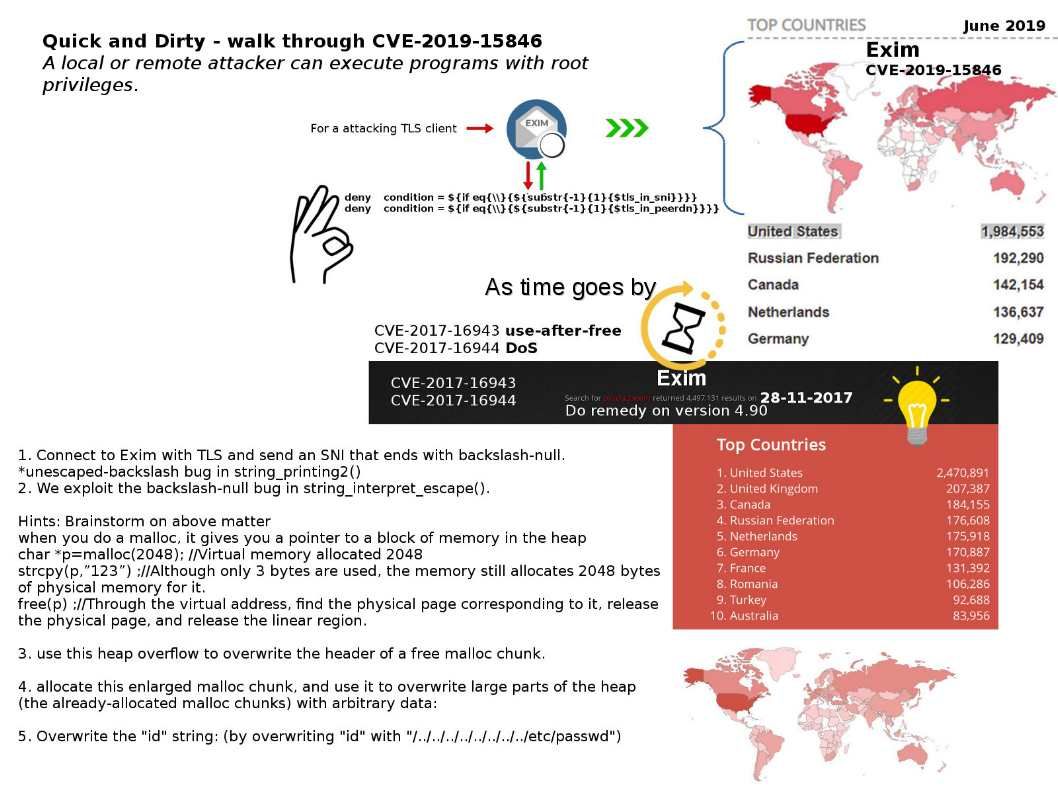
Preface: Quite a lot of cyber security expertise provides their explanation on vulnerability on Exim (A local or remote attacker can execute programs with root privileges). I will do a quick and dirty way to explain. Should you have interested, please refer below:
a. Connect to Exim with TLS and send an SNI that ends with backslash-null.
*unescaped-backslash bug in string_printing2()
b. We exploit the backslash-null bug in string_interpret_escape().
Hints: Brainstorm on above matter
When you do a malloc, it gives you a pointer to a block of memory in the heap
char *p=malloc(2048) – Virtual memory allocated 2048
strcpy(p,”123”) – Although only 3 bytes are used, the memory still allocates 2048 bytes of physical memory for it.
free(p) – Through the virtual address, find the physical page corresponding to it, release the physical page, and release the linear region.use this heap overflow to overwrite the header of a free malloc chunk.
c. use this heap overflow to overwrite the header of a free malloc chunk.
d. allocate this enlarged malloc chunk, and use it to overwrite large parts of the heap (the already-allocated malloc chunks) with arbitrary data:
e. Overwrite the “id” string: (by overwriting “id” with “/../../../../../../../../etc/passwd”)
Official announcement:
Download and build a fixed version:
Tarballs: https://ftp.exim.org/pub/exim/exim4/
Git: https://github.com/Exim/exim.git
- tag exim-4.92.2
- branch exim-4.92.2+fixes