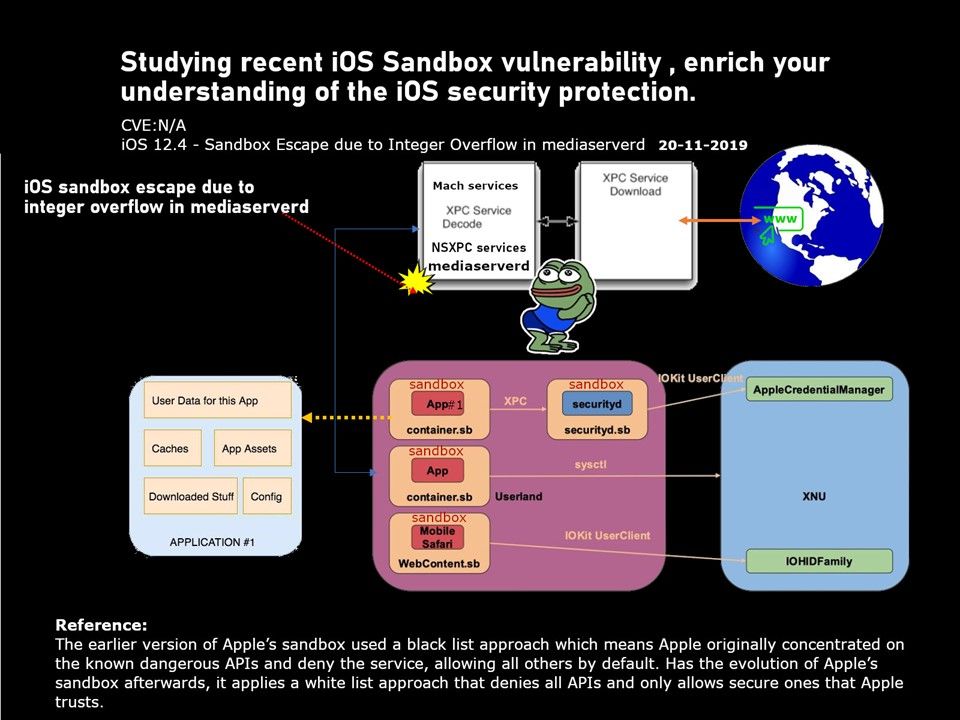
Background: XPC is a type of iOS IPC. Through XPC, an app can communicate with some system services. mediaserverd (/ usr / sbin / mediaserverd) is a daemon process launched by the root process launchd, and its description file is com.apple.mediaserverd.plist stored in / System / Library / LaunchDaemon directory, when the system starts, it will scan all plist files under this directory, start all background processes separately, probably there are more than 50 background processes are the real reason for the pseudo background in the iOS system. The decoding of audio and video involves the operation of hardware. Mediaserverd contains a large amount of code that calls the driver layer. Through xpc, users can prevent overflow attacks and improve system stability. Because the same xpc interface is cross-process, it makes it more difficult for overflow attacks to forge data.
Synopsis: Mediaserverd has various media parsing responsibilities, its reachable from various sandboxes and is able to talk to kernel drivers. Perhaps, hacker can find a valid trigger point in this place.
Status – Even though 13.1.3 IPXR, it also vulnerable. For more details, please refer to diagram.